
Halcyon has identified a new ransomware operator, dubbed Volcano Demon, responsible for a series of recent cyberattacks involving phone call-based extoriton. Their signature ransomware, LukaLocker, encrypts files with a .nba extension and has demonstrated a troubling capability to infiltrate both Windows and Linux systems.
Discovery
The Halcyon Research Team discovered LukaLocker in the aftermath of several attacks over the preceding fortnight. The team analyzed the malware and found it to be a sophisticated x64 PE binary written in C++. LukaLocker uses API obfuscation and dynamic API resolution to evade detection, making it a formidable adversary for traditional cybersecurity defenses.
The ransomware was identified using various command-line options, some of which, despite being implemented, do not function. These include the -l flag for log file output, which creates an empty file, and modes such as net and backups, which appear intended to target network shares and backup files but currently do nothing.
LukaLocker uses the Chacha8 cipher for data encryption, employing a randomly generated key and nonce. The Elliptic-curve Diffie-Hellman (ECDH) algorithm over Curve25519 generates the encryption key, which is stored in the file's footer along with the nonce and other metadata.
The ransomware supports different encryption percentages, allowing for partial encryption of files to increase the complexity of decryption efforts without a valid key, as well as to speed up the attacks, leaving defenders fewer opportunities for intervention.
Halcyon
Attack vectors and tactics
Volcano Demon employs a comprehensive approach to compromising networks. They harvest common administrative credentials to gain access and lock both workstations and servers. Prior to encryption, data is exfiltrated to command and control (C2) servers, enabling double extortion tactics. Logs are cleared to hinder forensic investigations, further complicating recovery efforts.
The ransomware has been observed to terminate various services and processes critical to antivirus, endpoint protection, backup, and database management. This tactic, akin to methods used by Conti ransomware, helps LukaLocker avoid detection and prevention measures. Services and processes targeted include:
- Antivirus and endpoint protection: Sophos, Symantec, McAfee, Avast, Defender, Malwarebytes, BitDefender, Spyhunter, Kaspersky, SentinelOne
- Backup and eecovery: Acronis, Symantec, Veeam, SQL Safe
- Databases: Microsoft SQL Server, MySQL, IBM DB2, Oracle
- E-Mail servers: Microsoft Exchange
- Virtualization and cloud: VMware, BlueStripe, ProLiant
- Remote access and monitoring: Alerter, Eventlog, UI0Detect, WinVNC4
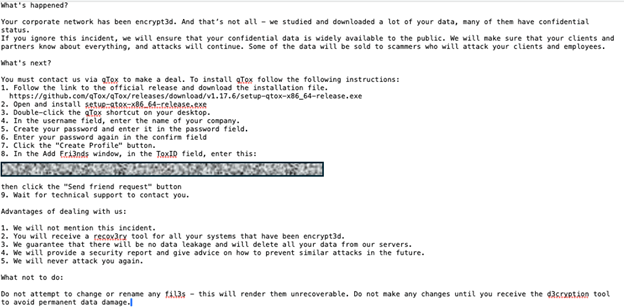
Instead of a traditional leak site, Volcano Demon uses direct phone calls to the leadership and IT executives of targeted organizations. These calls are made from unidentified numbers and can be aggressive and threatening, emphasizing the urgency and seriousness of their demands.
Defense tips
To defend against LukaLocker and similar ransomware threats, organizations should:
- Implement robust logging and monitoring solutions to detect unauthorized access and suspicious activity.
- Use strong, unique passwords and implement multi-factor authentication (MFA) to protect administrative accounts.
- Maintain regular, encrypted backups stored offline or in secure, isolated networks.
- Deploy advanced endpoint protection solutions capable of detecting and stopping ransomware before it can execute.
- Develop and regularly update an incident response plan, including procedures for isolating infected systems and restoring from backups.







Leave a Reply