
Security researchers have uncovered a new phishing technique that sidesteps FIDO key protections by abusing legitimate cross-device sign-in functionality.
The method, which was recently observed in actual attacks in the wild, uses adversary-in-the-middle (AitM) tactics to trick users into scanning malicious QR codes, effectively neutralizing one of the most secure MFA options available.
The attack was discovered by Expel’s Security Operations Center (SOC). The researchers attribute the campaign to PoisonSeed, a threat actor known for phishing operations targeting cryptocurrency holders. This new technique does not exploit a vulnerability in the FIDO protocol itself but rather leverages user trust and authentication workflows to sidestep FIDO’s security barriers.
FIDO (Fast Identity Online) keys are physical MFA devices that use public-key cryptography to authenticate users. They are widely regarded as more secure than SMS or email-based MFA methods because they require physical interaction and are typically bound to a user’s device. Cross-device sign-in is a usability feature allowing a user to authenticate on an unregistered device by scanning a QR code with an authorized mobile app.
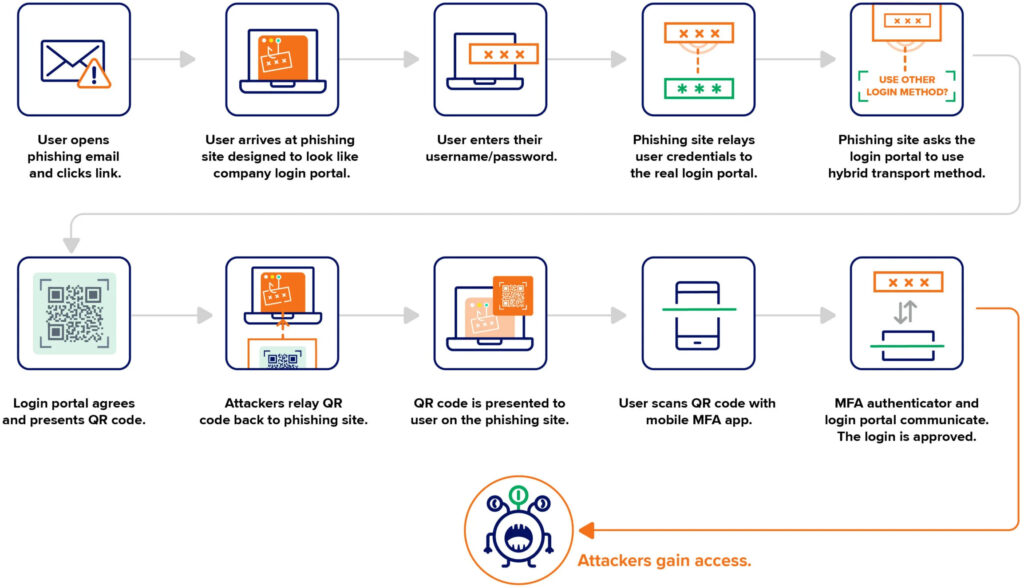
In the attack observed by Expel, phishing emails directed victims to a fake Okta login page hosted on a suspicious domain at okta[.]login-request[.]com. Upon entering their username and password, users were shown a QR code mimicking a legitimate login process. Unbeknownst to the victim, this QR code had been generated by the real authentication portal using their stolen credentials. The phishing site simply relayed it back to the victim, who then scanned it with their legitimate MFA app, completing the login process for the attackers.
Expel Security
The affected organization, an Expel customer, had deployed FIDO keys for high-value accounts. Under normal conditions, an attacker lacking physical access to the FIDO device would be locked out. However, by invoking the cross-device flow and intercepting the QR code, the attackers successfully authenticated without touching the user’s key.
This represents a significant advancement in phishing sophistication, as it bypasses one of the most resilient MFA mechanisms currently available. PoisonSeed’s use of infrastructure hosted on Cloudflare further masked the malicious nature of their domains, helping the phishing pages evade detection and gain user trust.
FIDO keys remain a strong defense against account compromise but defenders must now audit cross-device sign-in activity and scrutinize the registration of new MFA devices more closely. Organizations should:
Monitor authentication logs for anomalous cross-device login requests.
Investigate FIDO key registrations from unusual geographies or unfamiliar key brands.
Require Bluetooth proximity for cross-device sign-ins to ensure physical presence.
Immediately terminate all sessions and reset credentials when suspicious activity is detected.







Leave a Reply