
In a newly published paper, Dr. Mordechai Guri from Ben-Gurion University has unveiled the “PIXHELL” attack, a novel method for exfiltrating sensitive data from air-gapped, audio-gapped systems.
The attack allows rogue actors to leak information through acoustic signals generated by LCD screens, exploiting coil noise and capacitor vibrations caused by manipulated pixel patterns. Unlike previous acoustic attacks, PIXHELL requires no audio hardware, bypassing the defense known as the “audio gap,” which prohibits speakers in highly sensitive environments.
Air-gapped systems, typically used in sectors like defense, finance, and critical infrastructure, are isolated from external networks to protect sensitive data. Audio-gapped systems take this a step further by prohibiting the use of sound-generating hardware to prevent audio-based data leakage.
However, PIXHELL bypasses both of these security measures, leveraging the acoustic properties of LCD screens rather than traditional speakers. This attack has serious implications for environments that depend on air-gapped systems, showing once again that physical isolation does not guarantee immunity from cyber threats.
PIXHELL details
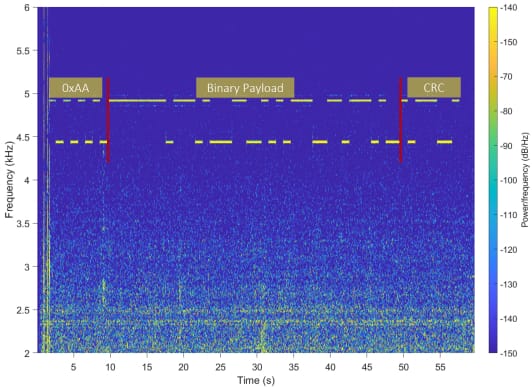
The PIXHELL attack works by having malware installed on an air-gapped machine and manipulating the screen's pixel patterns to generate specific acoustic signals within the 0-22 kHz range. The noise, which emanates from the internal components of the LCD, can be captured by nearby devices like smartphones, laptops, or microphones placed within a 2-meter radius. These acoustic signals are subtle and often inaudible, but they carry encoded information that attackers can capture and decode to extract sensitive data.

Arxiv.org
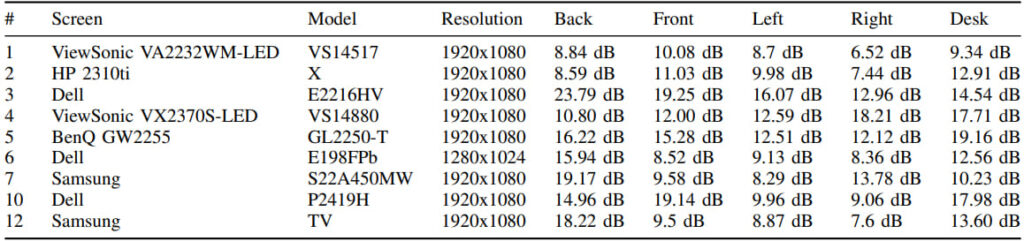
Dr. Guri's research team tested this method on various screen models and demonstrated that the technique could exfiltrate both textual and binary data at a slow but consistent rate. The attack employs modulation techniques such as On-Off Keying (OOK), where binary data is represented by the presence or absence of sound, and Frequency Shift Keying (FSK), which uses two distinct frequencies to represent binary 1s and 0s. By carefully manipulating these patterns, attackers can leak valuable information such as encryption keys, passwords, or sensitive documents.
Arxiv.org
The method is especially dangerous because it can operate without alerting the system's user. Attackers can configure the pixel patterns to appear nearly black or indistinguishable to human observers, enabling stealthy data transmission over time. This low visibility makes the PIXHELL attack difficult to detect, even in highly secure environments.
Arxiv.org
Protections
The research proposes several countermeasures, such as using noise jammers to interfere with the acoustic signals or monitoring the audio spectrum for unusual activity. Physical security measures, like restricting the proximity of portable devices to sensitive machines, could also help mitigate the risk of such attacks. However, Dr. Guri notes that these measures might introduce complexity and cost, making them difficult to implement in large-scale operations.
This research further demonstrates how attackers continue to find creative ways to breach isolated networks, following Dr. Guri's recent work on the RAMBO attack, which exfiltrated data through electromagnetic emissions from RAM.







Leave a Reply