
Security researchers have uncovered a new denial-of-service (DoS) technique targeting HTTP/2 implementations, dubbed “MadeYouReset” (CVE-2025-8671).
The attack, which causes servers to reset their own connections and overconsume resources, has the potential to severely disrupt unpatched systems through distributed denial-of-service (DDoS) campaigns.
The vulnerability was discovered by Gal Bar Nahum, Prof. Anat Bremler-Barr, and Dr. Yaniv Harel of Tel Aviv University, in collaboration with researchers from Imperva. The flaw was disclosed through the CERT Coordination Center, and its mechanics reveal a subtle yet dangerous evolution from the 2023 “Rapid Reset” vulnerability (CVE-2023-44487). While Rapid Reset relied on clients explicitly spamming RST_STREAM frames, MadeYouReset leverages malformed yet protocol-compliant frames to provoke the server into issuing resets itself.
A deceptively compliant exploit
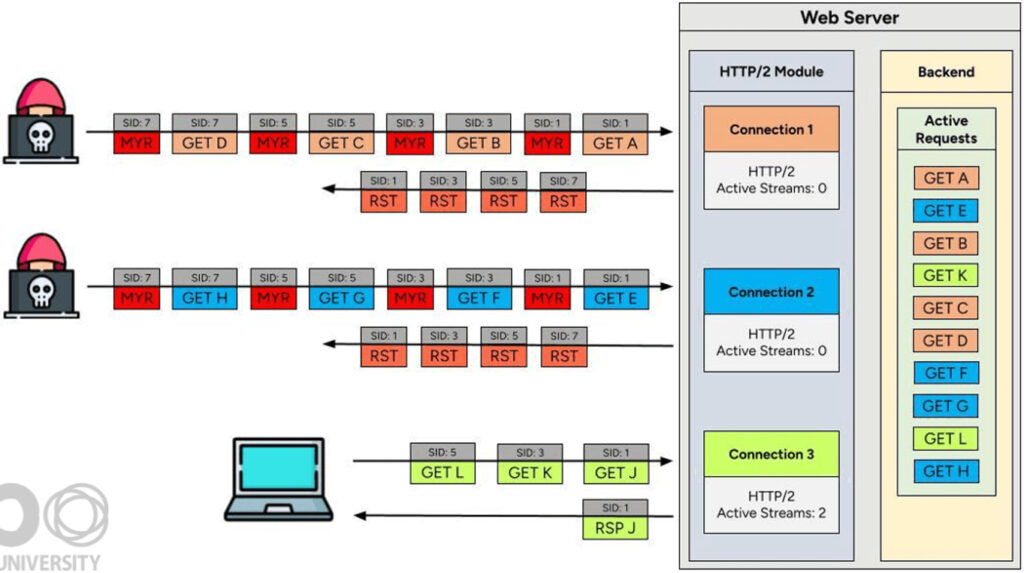
At the heart of the vulnerability lies a mismatch between the HTTP/2 specification and real-world server behavior. HTTP/2 allows both clients and servers to cancel streams at any time. In practice, many implementations continue to process requests even after a stream is reset, causing a resource leak. MadeYouReset exploits this by sending specially crafted frames that subtly violate the protocol, prompting the server to reset the stream without freeing up backend processing resources.
Among the key techniques used in the attack are:
- Window-Overflow: Sends WINDOW_UPDATE frames that exceed the allowed flow-control window size, triggering a reset.
- Zero-Increment Updates: Uses WINDOW_UPDATE frames with a 0 increment, which the server responds to with a PROTOCOL_ERROR and a RST_STREAM.
- Half-Closed Stream Abuse: Sends additional DATA or HEADERS frames after a stream is half-closed, forcing server-side resets.
- Priority-Length Mismatch: Sends PRIORITY frames with incorrect lengths to induce error states and resets.
Imperva
These behaviors result in a situation where streams appear closed to the protocol but remain active in the server's backend, allowing attackers to effectively bypass the SETTINGS_MAX_CONCURRENT_STREAMS limit. Over time, this leads to memory or CPU exhaustion and eventual service degradation or outage.
Imperva
Scope of impact and mitigation
The vulnerability impacts several widely used HTTP/2 implementations, including Apache Tomcat (tracked separately as CVE-2025-48989), Netty, Jetty, IBM WebSphere, BIG-IP (F5), gRPC, Mozilla, Eclipse Foundation, Fastly, Varnish, SUSE Linux, Zephyr Project, and Wind River.
Many vendors have released or are preparing patches. CERT/CC recommends a review of vendor advisories and immediate application of relevant updates.
Some major infrastructure providers, such as Cloudflare, were unaffected by the attack thanks to existing mitigations deployed during the 2023 Rapid Reset incident. Cloudflare noted that its systems were not vulnerable due to proactive rate limiting and behavioral detection mechanisms that were already in place. Its open-source Pingora framework, which relies on the Rust-based h2 library, could be affected in older versions. Users are advised to update to h2 v0.4.11 or later.
Imperva emphasized that the MadeYouReset technique is harder to detect because it doesn't rely on overt protocol violations. Instead, it sends well-formed frames that trigger spec-compliant server-side error handling, making the attack traffic nearly indistinguishable from legitimate HTTP/2 activity. Existing rate limits on client-sent RST_STREAM frames are ineffective here, since the resets originate from the server itself in response to protocol edge cases.
Organizations running HTTP/2 servers should apply all available updates from software vendors and HTTP/2 library maintainers, drop malformed or non-compliant frames early during packet parsing, and ensure that server-side logic accounts for backend request processing independently from protocol-level stream states.







Leave a Reply