
Security researchers at Proofpoint have identified FrigidStealer, a newly discovered MacOS information stealer being distributed through fake browser update scams.
The malware is part of a growing trend in web inject attacks, where cybercriminals compromise legitimate websites to serve malicious scripts. The threat actor TA2727 has been observed delivering FrigidStealer alongside malware for Windows and Android devices.
FrigidStealer: A new threat to Mac users
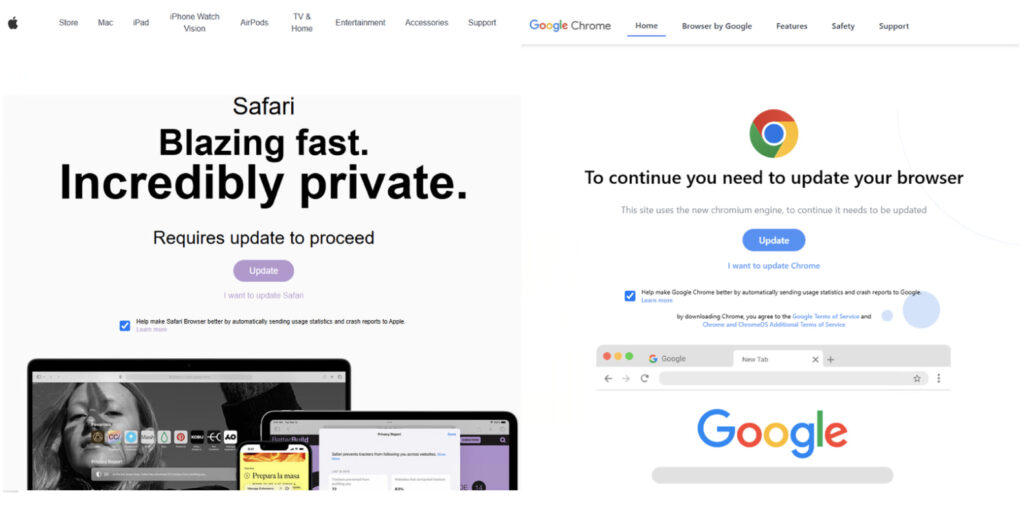
MacOS malware remains relatively rare compared to its Windows counterparts, but FrigidStealer is the latest example of attackers expanding their focus beyond traditional targets. Delivered through compromised websites, FrigidStealer masquerades as an urgent Google Chrome or Safari update, tricking users into installing a trojanized DMG file.
Proofpoint
Once executed, the malware uses social engineering tactics to gain elevated privileges, bypassing Apple's built-in security features. Specifically:
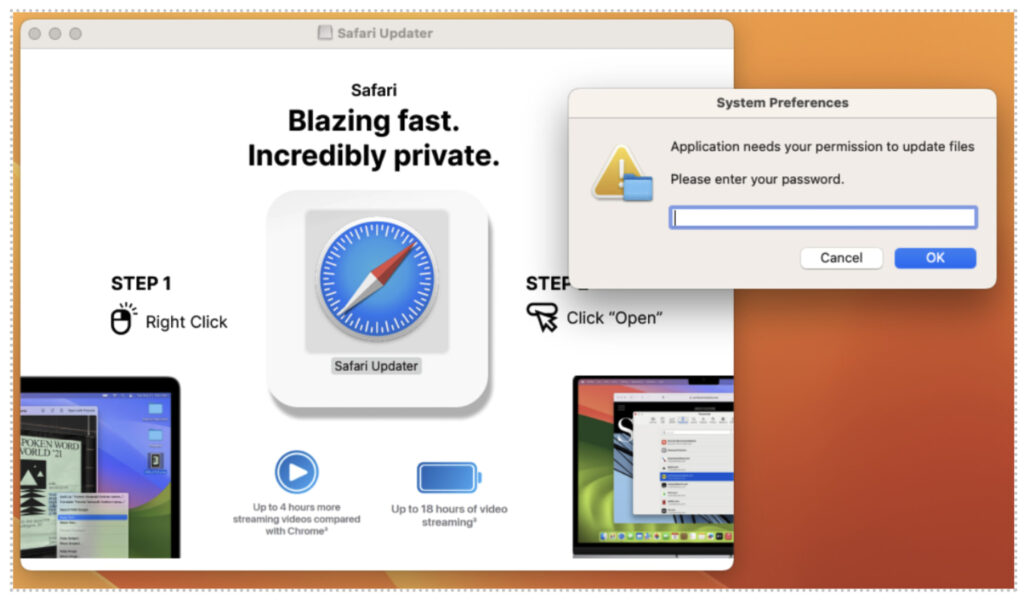
- The DMG file presents legitimate-looking browser icons and instructs users to manually right-click and select “Open”, a common technique to bypass MacOS Gatekeeper warnings.
- The embedded Mach-O executable, written in Go and ad-hoc signed, launches a process that prompts the user to enter their Mac password using AppleScript (osascript).
- After obtaining system access, FrigidStealer scans the system for browser cookies, saved passwords, cryptocurrency-related files, and Apple Notes stored on the device.
- The stolen data is exfiltrated to askforupdate[.]org, the malware's command-and-control (C2) server.
Proofpoint researchers note that FrigidStealer was first observed in late January 2025 as part of a broader campaign that also distributed Windows and Android malware.
Proofpoint
Threat actors behind the attack
Although FrigidStealer is a new MacOS malware, the infrastructure behind its distribution follows a well-established attack pattern involving two cooperating cybercriminal groups.
TA2727 is a financially motivated cybercrime group responsible for delivering FrigidStealer via fake update scams. This threat actor uses traffic distribution networks to filter victims by region and device type, serving different malware payloads accordingly.
TA2726 is an established Traffic Distribution System (TDS) operator that plays a key role in these campaigns by redirecting victims to TA2727-controlled infrastructure. This actor has been active since at least September 2022 and works with other cybercriminal groups, including TA569 (SocGholish).
The use of web injects—malicious JavaScript code inserted into legitimate websites—has surged in recent years, with multiple threat actors adopting this technique. Unlike traditional email phishing or exploit-based malware delivery, web injects rely on compromised websites to distribute social engineering lures, making detection and mitigation more challenging.
Fake update scams remain a particularly effective method for macOS infections, as users may be accustomed to downloading updates manually when prompted.







Leave a Reply