
Cisco Talos has disclosed a new data theft campaign by the advanced persistent threat (APT) actor “LilacSquid,” active since 2021.
The campaign targets a diverse array of sectors across the globe, employing sophisticated malware and leveraging vulnerabilities in public-facing servers and compromised remote desktop protocol (RDP) credentials.
LilacSquid campaign
The campaign involves sophisticated tactics aimed at long-term access and data exfiltration. LilacSquid targets IT organizations in the U.S., energy sectors in Europe, and pharmaceutical companies in Asia, indicating an industry-agnostic approach to data theft.
LilacSquid employs multiple initial access techniques, including exploiting vulnerabilities in public-facing application servers and using compromised RDP credentials. Once access is gained, the attackers deploy a variety of tools for post-compromise activities.
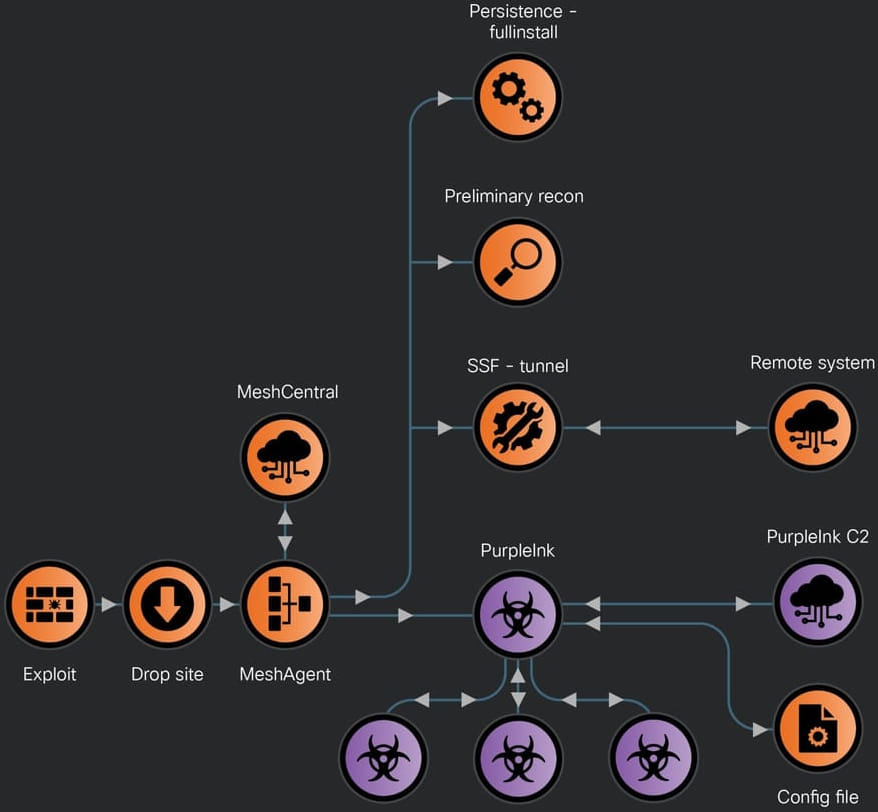
Key among these tools is MeshAgent, an open-source remote management tool used for preliminary reconnaissance and further malware deployment. They also use PurpleInk, a customized version of QuasarRAT, which serves as the primary implant, allowing full control over infected systems. Additionally, the threat actor utilizes two custom malware loaders, InkBox and InkLoader, to facilitate the deployment of PurpleInk and other malicious tools.
Infection chains
LilacSquid primarily uses two types of infection chains. The first involves exploiting a vulnerable web application. Successful exploitation leads to the deployment of a script that sets up directories and downloads MeshAgent. This tool then connects to its command-and-control (C2) server, performs reconnaissance, and activates other implants like Secure Socket Funneling (SSF) and PurpleInk.
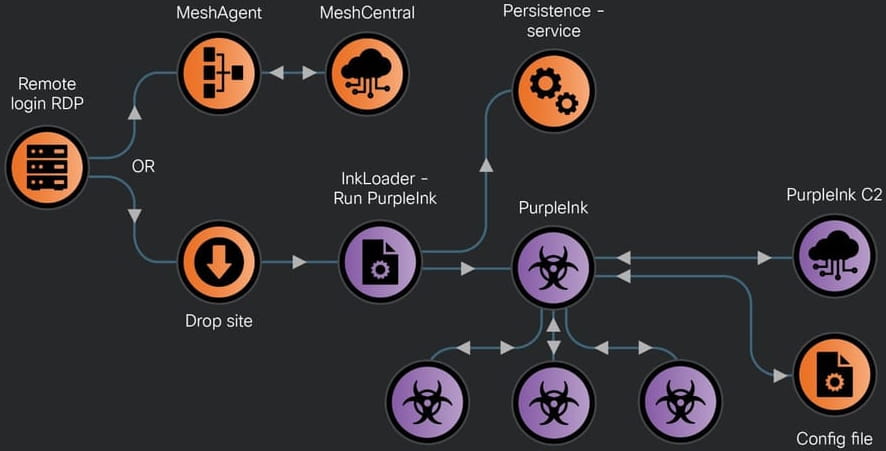
The second infection chain involves the use of compromised RDP credentials. In this scenario, the attackers download and execute InkLoader and PurpleInk. InkLoader is registered as a service to maintain persistence, ensuring that PurpleInk and other malware can be continually deployed even after system reboots.
Cisco Talos
PurpleInk capabilities
PurpleInk, LilacSquid's primary implant, has evolved from QuasarRAT and includes a range of capabilities:
- Enumerate the process and send the process ID, name, and associated Window Title to the C2.
- Terminate a process ID specified by the C2 on the infected host.
- Run a new application on the host.
- Get drive information for the infected host, such as volume labels, root directory names, drive type, and drive format.
- Enumerate a given directory to obtain underlying directory names, file names, and file sizes.
- Read a file specified by the C2 and exfiltrate its contents.
- Replace or append content to a specified file.
- Gather system information about the infected host using WMI queries.
- Start a remote shell on the infected host using ‘cmd[.]exe /K'.
- Rename or move directories and files and then enumerate them.
- Delete files and directories specified by the C2.
- Connect to a specified remote address, referred to internally as “Friend,” indicating that PurpleInk can act as an intermediate proxy tool.
- PurpleInk can also connect to new friends (proxies), send data to new or existing friends, disconnect from specified friends, and receive data from other connected friends.
Cisco Talos noted in its report similarities between LilacSquid's tactics and those used by North Korean APT groups, such as Andariel and Lazarus. The use of MeshAgent, SSF, and proxy tools aligns with known methods of these groups, suggesting possible overlaps or shared techniques.
LilacSquid's multi-faceted approach and use of customized malware highlight the evolving nature of APT threats. Organizations must enhance their security postures, employing comprehensive defense mechanisms and staying vigilant against such sophisticated campaigns.







Leave a Reply