
CYFIRMA's research team has uncovered Kematian Stealer, a new information-stealing malware being actively developed and distributed on GitHub.
These stealers are typically sold on malware-as-a-service (MaaS) platforms on the dark web, Telegram, and hacker forums, for a monthly subscription cost of $100-$400, depending on the malware's capabilities. Kematian is open-source and freely available, which has helped to quickly garner attention by the cybercrime community.
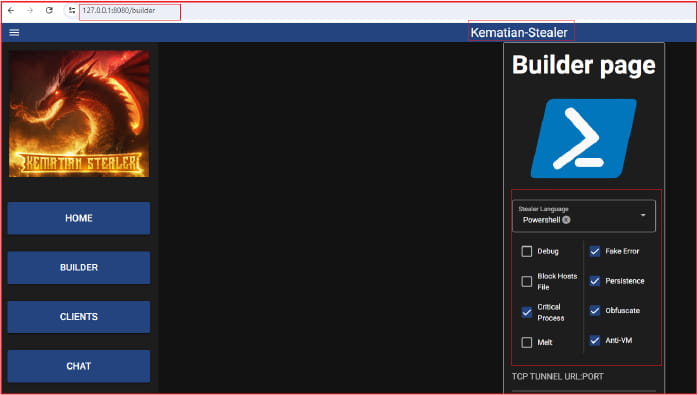
The GitHub repository hosting the malware under the “Somali-Devs” account features a builder that lets users configure the malware's features and input C2 server details through a web interface. The builder generates malicious binaries, emphasizing the malware's adaptability and potential for widespread use.
CYFIRMA's researchers found a RAR archive in the wild, likely spread via spam or phishing emails. This archive contained a loader binary that, once executed, deployed batch and PowerShell scripts to collect sensitive user information. The scripts attempted to download an additional malicious binary, identified as Kematian-Stealer, from a GitHub repository under the account “Somali-Devs.”
CYFIRMA
Kematian Stealer capabilities
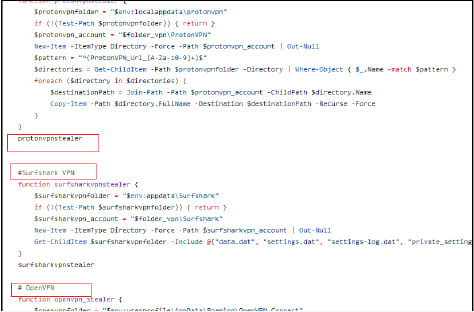
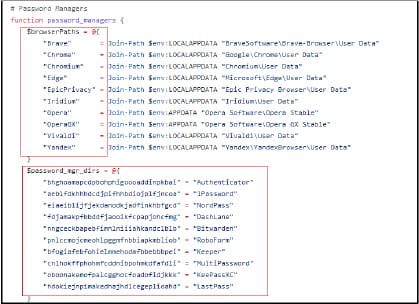
Kematian-Stealer is designed to covertly extract a wide array of sensitive data from Windows systems, including information from messaging applications, gaming platforms, VPN services, email clients, FTP clients, password managers, and cryptocurrency wallets.
CYFIRMA
The initial loader deploys a batch script that creates a PowerShell script to perform several tasks, including adding directories to the Windows Defender exclusion list, creating a scheduled task for persistence, gathering system information and sending it to a Discord webhook, and attempting to download and execute a secondary payload from GitHub.
CYFIRMA
Kematian-Stealer's capabilities are extensive, including the following:
- Extracts sensitive information from various applications.
- Captures images using the webcam and screenshots of the desktop.
- Processes cookie files and compresses collected data into a ZIP file for exfiltration.
- Deletes temporary files and the executed PowerShell script to minimize evidence.
The malware uses in-memory execution techniques to avoid detection and includes a builder tool hosted on GitHub, allowing users to customize and deploy the malware easily. This open-source availability and continuous development pose significant risks to organizations and individuals.
The discovery of Kematian-Stealer highlights the evolving threat landscape, where cybercriminals exploit open-source platforms to distribute sophisticated malware. This immediate availability lowers the bar of entry for aspiring cybercriminals and has the potential to make the operation of experienced actors more profitable. Also, the availability of capable off-the-shelf malware hampers threat analysts' capability to attribute attacks to specific threat actors, which helps them evade campaign tracking and disruptions.







Leave a Reply