
A new infostealer called Katz Stealer has entered the malware-as-a-service (MaaS) market, offering highly advanced data theft capabilities at prices starting as low as $100 per month.
Its low cost, combined with robust functionality, is making it a go-to choice for cybercriminals across the skill spectrum, as reflected by its rapidly growing popularity.
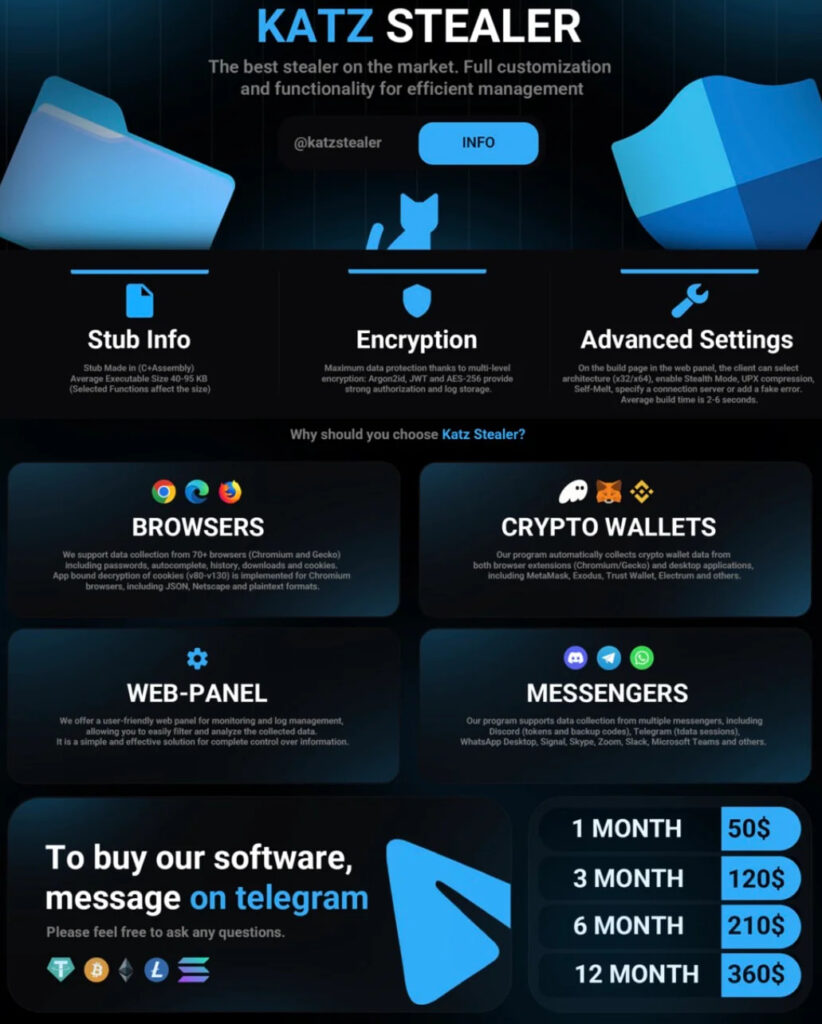
The emergence of Katz Stealer was documented by SentinelLabs. First advertised in early April on BreachForums, the stealer quickly gained traction within cybercrime circles due to its affordability, ease of use, and powerful capabilities. The malware is marketed via Telegram, Discord, and underground forums, and is offered in flexible subscription tiers: $100 for one month, $270 for three months, and $480 for six months. These prices significantly undercut many competing MaaS offerings, democratizing access to complex credential-theft operations.
SentinelOne
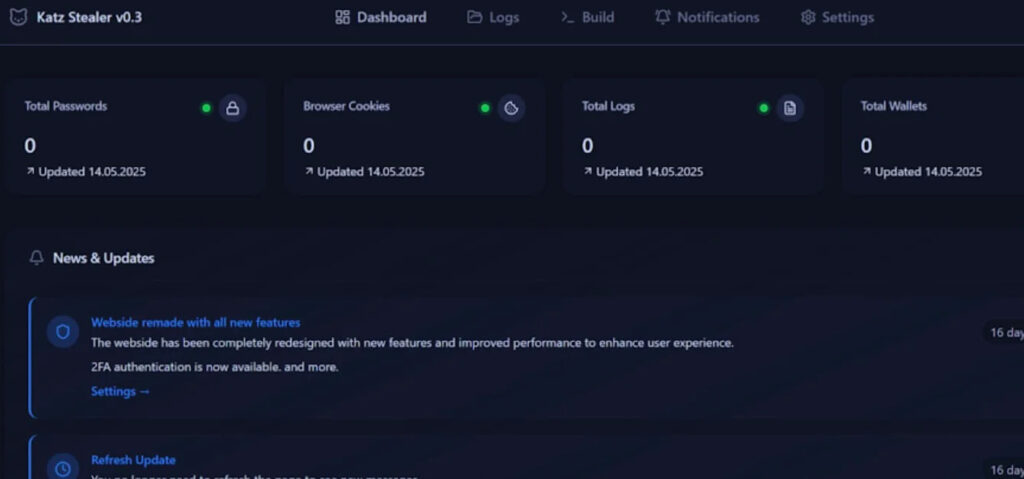
Buyers are given access to a web-based control panel used to create custom payloads, configure infection chains, and manage stolen data. This panel includes toggles for different theft modules, delivery options, anti-analysis settings, and data export features. The malware's infrastructure is supported by dedicated domains, such as katz-panel[.]com and katzstealer[.]com, which further streamline the attack lifecycle for its users.
SentinelOne
Delivered through phishing emails or trojanized downloads, the malware uses heavily obfuscated JavaScript loaders, steganography-laced images, and in-memory execution to bypass traditional defenses. It exploits legitimate Windows utilities like cmstp.exe for privilege escalation and persistence, and injects its payload into processes like MSBuild.exe for stealthy execution with elevated privileges.
Once active, Katz Stealer targets a wide array of personal data. It harvests credentials, cookies, autofill data, and decrypted passwords from browsers such as Chrome, Firefox, Edge, and Brave. For Chromium browsers, it defeats Google's Application Bound Encryption (ABE) by extracting the master key and decrypting credentials locally. Messaging apps like Telegram and Discord, gaming platforms like Steam, and VPN and FTP clients are also in scope.
The malware also searches for local cryptocurrency wallet files, private keys, and seed phrases from apps like MetaMask, Exodus, and Coinomi. It also scans for over 150 known browser extension IDs linked to crypto wallets and exfiltrates related data. Clipboard monitoring and screenshot capture allow attackers to intercept time-sensitive authentication codes or wallet addresses in real-time.
SentinelOne
All stolen data is funneled to command-and-control servers via HTTP/HTTPS POST requests. The malware is persistent, continually exfiltrating data and maintaining communication with the attacker infrastructure until instructed to clean up and terminate. A hardcoded C2 IP ensures connection stability, though its reliance on IPs over more resilient DNS-based infrastructure may be a weakness.
Although it's a complete package from a technical perspective, SentinelOne analysts emphasize that Katz Stealer's core innovation isn't technical novelty, but the aggressive pricing and ease of use that broaden access to sophisticated threats. The tool lowers the barrier to entry, allowing novice cybercriminals to perform operations that previously required skill or expensive tooling.







Leave a Reply