
The Secure Mobile Networking Lab at the Technical University of Darmstadt has launched CellGuard, an open-source iOS app designed to detect rogue base stations targeting iPhones.
Developed as part of a research project led by Lukas Arnold and supervised by cybersecurity expert Jiska Classen, the app leverages advanced algorithms to identify potential cellular network threats and anomalies, helping users uncover surveillance activities.
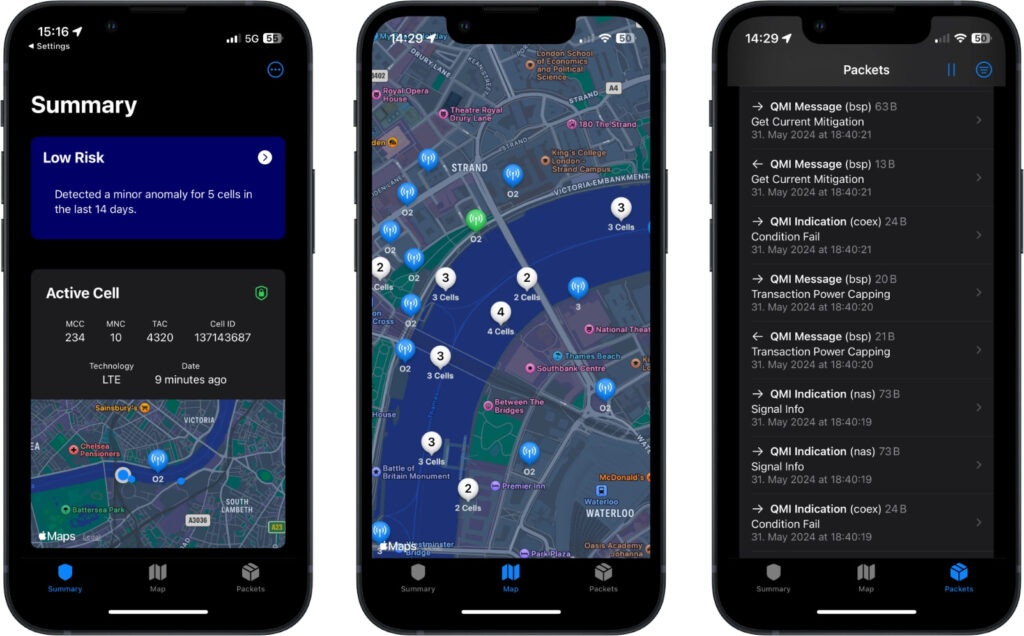
CellGuard works by monitoring baseband packets on iPhones and analyzing them for suspicious patterns that may indicate a rogue base station — also known as a “fake” base station. These rogue stations mimic legitimate cellular towers to intercept network traffic, track users, or even exploit vulnerabilities in a phone’s baseband chip, particularly in outdated networks like 2G. Since 2G lacks robust authentication measures, the best defense is to disable it, a feature supported in recent iPhones through Lockdown Mode.
Rogue base stations are often used by sophisticated attackers, including state-sponsored groups, who exploit mobile network infrastructure to force phones to connect to them. These setups can bypass security measures introduced in 3G and 4G networks, particularly when attackers collaborate with mobile operators or use roaming systems to authenticate their malicious stations. CellGuard’s primary goal is to detect these subtle network manipulations.
How CellGuard works
CellGuard employs several metrics to distinguish between legitimate and rogue base stations, including:
- Location database cross-references: Comparing detected base stations with Apple’s Location Services (ALS) database, identifying cells that have appeared too recently or have incorrect parameters.
- Signal analysis: Checking for signal strength anomalies, as rogue stations often emit much stronger signals to force connections.
- Bandwidth checks: Looking for base stations using outdated or low-cost hardware, often associated with rogue installations.
- Network reject packets: Spotting failed network authentication attempts, another potential indicator of malicious activity.
While the app is capable of detecting irregularities, the developers caution that false positives may occur due to legitimate network changes, such as newly set up base stations or overloaded network conditions.
cellguard.seemoo.de
Technical insights and public testing
CellGuard captures packets exchanged between the iPhone’s baseband chip and iOS and processes them to detect irregularities in real-time. The app’s algorithms, informed by real-world testing across Europe and the US, evaluate packet data, signal strength, and user location to flag suspicious base stations. However, as rogue base station attacks remain relatively rare, many warnings are likely to be false alarms.
Users interested in contributing to the project can join an opt-in study aimed at refining CellGuard’s detection algorithms. Participants share anonymized data from their devices, which will be used to improve future versions of the app.
If CellGuard flags a potential rogue base station, users are advised to remain calm, as many alerts may be benign network anomalies. However, if users are concerned about an actual threat, they can enable flight mode or turn off their phone to break the connection. Those encountering unusual phone behavior while connected to a suspicious base station are encouraged to save system diagnostic logs for further investigation.
Open-source and privacy-first approach
CellGuard is open-source, with its code available on GitHub under the GPL-3.0 license, encouraging community participation in improving the app’s functionality. The project prioritizes privacy, adhering to principles of minimal data usage and offline-first data processing. All personal data is stored locally on the device, and only anonymized information is shared with the research team if users opt into the study. No data is sold or shared with third parties.
As CellGuard continues its beta testing phase, the research team hopes to attract a broader audience of iPhone users to refine its detection methods and ultimately enhance the security of mobile networks.







Why do I need this, why is this important?