
Fortinet has discovered a new botnet dubbed “Goldoon” which has been exploiting a decade-old vulnerability in end-of-life (EoL) D-Link routers still in use globally.
This botnet specifically targets the D-Link DIR-645 Wired/Wireless Router Revision Ax, affecting systems with firmware version 1.04b12 and earlier. The vulnerability, identified as CVE-2015-2051, allows remote attackers to execute arbitrary commands through the router's HNAP interface, presenting a significant threat to network security.
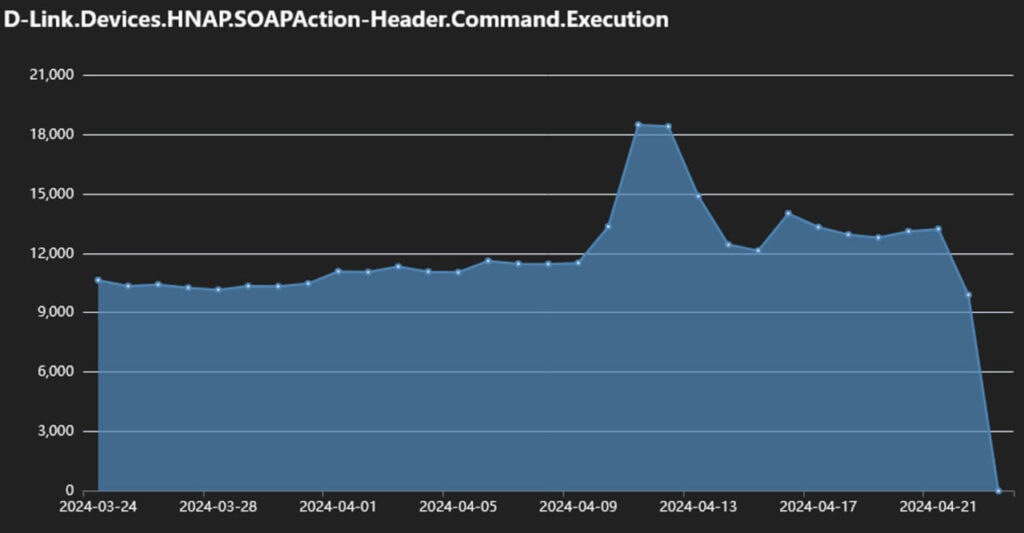
The malicious operation was discovered by FortiGuard researchers who observed increased attempts to exploit this weakness in April 2024. The botnet utilizes a crafted HTTP request that carries a malicious command in the header, targeting the GetDeviceSettings action on the HNAP interface of the vulnerable routers. This method enables attackers to gain complete control over the affected devices.
Fortinet
The initial phase of the attack involves the use of a “dropper” script downloaded from a compromised web address (hxxp://94[.]228[.]168[.]60:8080). This script is designed to download, execute, and subsequently remove various malware files across multiple Linux system architectures, thereby ensuring the persistence of the botnet across reboots and cleanups.
Following the dropper phase, the malware employs a downloader component that uses an XOR key to decrypt essential parts of its communication setup. This component also uses deceiving headers in its HTTP requests, such as “User-Agent: FBI-Agent (Checking You),” to download the final payload, evading basic security measures.
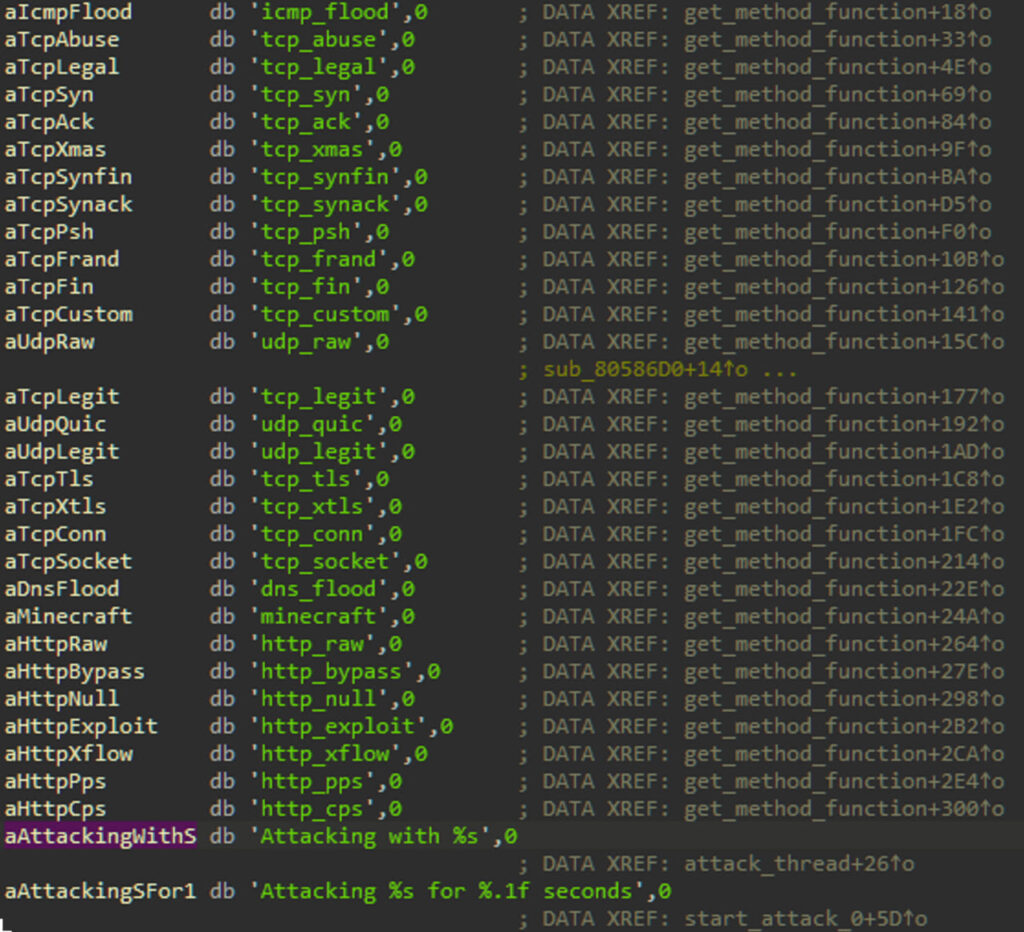
Once installed, the Goldoon malware establishes persistent connections with a command and control (C2) server and prepares the compromised device for further malicious activities. These include a variety of distributed denial-of-service (DDoS) attacks, such as ICMP flooding, TCP flooding, and others. Interestingly, the botnet is also capable of targeting specific applications, including Minecraft servers, through tailored DDoS attacks.
Fortinet
For users and organizations utilizing the affected D-Link routers, it is crucial to apply firmware updates immediately to mitigate this vulnerability. Although the targeted router models have long reached their end-of-life now, applying the last security updates that were made available by the vendor still address the particular vulnerability.
The emergence of the Goldoon botnet is a stark reminder of the persistence of cybercriminals in exploiting old vulnerabilities to commandeer large networks of devices for malicious purposes. Continuous vigilance and prompt application of security updates are essential in defending against these evolving threats.







Leave a Reply