
A new cash-out method called “Ghost Tap” has been discovered by ThreatFabric analysts, where cybercriminals exploit NFC relay tools to siphon money from stolen credit card details linked to mobile payment systems such as Apple Pay and Google Pay. This tactic allows fraudsters to remain anonymous while scaling their operations across multiple locations, posing a significant threat to financial institutions and retailers alike.
The rise of “Ghost Taps”
ThreatFabric’s investigation into underground forums revealed discussions about relaying stolen credit card details through NFC traffic. Posts highlighted the ability to transfer a linked Apple Pay or Google Pay card from one device to another, enabling fraudulent transactions at offline retailers. Cybercriminals achieve this by using tools like NFCGate, originally a legitimate academic research project from TU Darmstadt, which has been co-opted for malicious purposes.
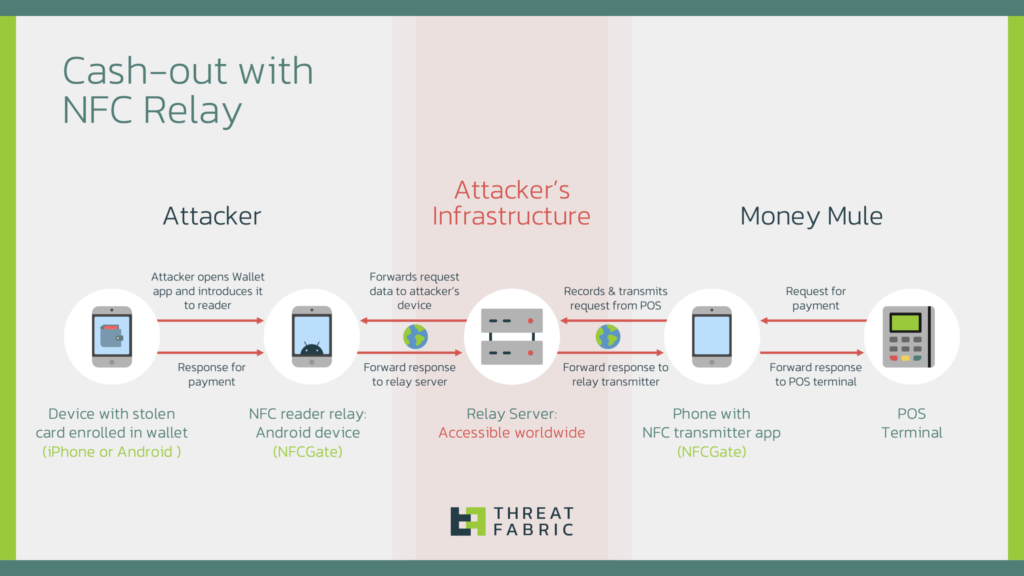
The tactic involves relaying NFC traffic between two devices to bypass the physical limitations of payment systems. The attacker possesses a device with a stolen card linked to a mobile payment service, while a mule uses another device to make purchases at point-of-sale (POS) terminals. The mule’s transactions appear legitimate, concealing the attacker’s identity and location.
This process requires minimal resources, including a mobile device with NFC and a stolen card linked to Apple Pay or Google Pay, two NFC-enabled devices running NFCGate, and a relay server to facilitate traffic between the attacker and the mule. Once set up, the stolen card can be used simultaneously in multiple locations, enabling attackers to scale their fraudulent activities while avoiding detection.
Attackers use phishing schemes and mobile banking malware to gain access to victims’ credit card details and the associated one-time passwords (OTPs) needed to link the card to a new device. Common techniques include banking malware with overlay or keylogging capabilities captures card details and OTPs sent via SMS or push notifications are intercepted and forwarded to attackers. Another scenario could be victims unwittingly entering card details and OTPs on fake websites controlled by attackers.
Risks and defending tips
Ghost Tap represents a significant evolution in fraud tactics, allowing attackers to conduct purchases anonymously and remotely, often from different countries, use the same stolen card in multiple locations in a short timeframe, and scale operations by employing multiple mules for simultaneous transactions.
Traditional anti-fraud systems struggle to detect Ghost Tap activity due to:
- Transactions appear to originate from the same linked device.
- Individual purchases are often below fraud detection thresholds, though they quickly accumulate into large sums.
- Attackers may disable location tracking, making it harder to identify the cardholder’s true location.
Financial institutions must adapt their security measures to counter this growing threat. Key steps include flagging newly linked devices, especially when paired with malware on the original customer device, as potential indicators of fraud, and identifying transactions performed in geographically improbable timeframes, such as rapid purchases in distant locations. Another solid defense tactic is implementing systems to recognize NFC relay anomalies, such as unusual latency in communication or discrepancies between device and transaction locations.







Leave a Reply