
Elastic Security Labs has identified a new malware family named FinalDraft, that uses Microsoft’s Graph API to communicate through Outlook email drafts, allowing attackers to bypass traditional network monitoring.
The malware is part of a sophisticated cyber-espionage campaign and includes a custom loader, a backdoor, and multiple post-exploitation modules targeting a foreign ministry.
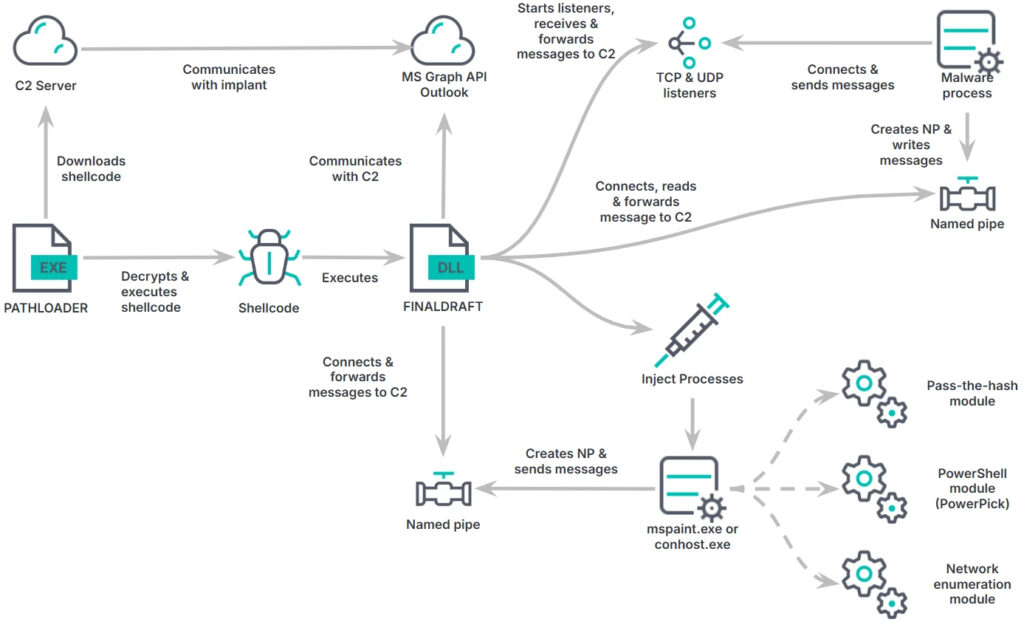
Elastic Security researchers uncovered FinalDraft along with its loader component, Pathloader, during an investigation. The analysis revealed a long-running development cycle, with multiple distinct versions and both Windows and Linux variants, suggesting a well-funded and organized threat actor.
Pathloader, a lightweight Windows executable, retrieves and executes encrypted shellcode from attacker-controlled infrastructure. The downloaded shellcode decrypts and launches FinalDraft, a 64-bit C++ malware specializing in data exfiltration and stealthy process injection. The malware obfuscates its activity through API hashing, string encryption, and sandbox evasion techniques.
Espionage via Outlook drafts
FinalDraft exploits Microsoft Outlook’s mail draft system for covert command-and-control (C2) operations. Instead of relying on conventional network protocols, the malware:
- Creates a session email draft upon infection.
- Retrieves commands from hidden drafts sent by the C2.
- Executes commands such as process injection, file manipulation, and lateral movement.
- Sends responses back to the C2 by updating the draft emails.
This method avoids direct network communications, reducing the likelihood of detection by firewalls or endpoint monitoring solutions. The malware stores its authentication tokens in the Windows registry and refreshes access via Microsoft’s OAuth system.
Elastic Security
Researchers identified an ELF (Linux) version of FinalDraft that supports additional C2 transport methods, including HTTP, UDP, ICMP, and DNS, indicating a broader targeting scope. Older Windows versions of the malware also used HTTP-based communication, typosquatting security vendors with domains like poster.checkponit.com (CheckPoint) and support.fortineat.com (Fortinet).
In terms of the malware’s capabilities, FinalDraft supports 37 commands, enabling:
- Process injection – Hides payloads in legitimate processes such as mspaint.exe.
- File operations – Copies, deletes, and exfiltrates files while using NTFS cluster manipulation to bypass security tools.
- Network proxies – Creates TCP/UDP listeners to relay traffic between infected hosts.
- Pass-the-hash (PTH) attacks – Uses stolen NTLM hashes for lateral movement.
- PowerShell execution – Runs PowerShell scripts without invoking powershell.exe, evading security detection.
Elastic Security Labs has released YARA rules and detection tips for FinalDraft, available in the bottom of its report. Generally, it is recommended to monitor Outlook Drafts for suspicious email activity, detect Process Injection via WriteProcessMemory and RtlCreateUserThread API calls, block AMSI and ETW Bypass Techniques used for stealth execution, and restrict OAuth Token Abuse by enforcing multi-factor authentication (MFA) and monitoring registry modifications.







Leave a Reply