
Security researcher mr.d0x has unveiled a new browser-based social engineering technique dubbed FileFix, a creative evolution of the ClickFix attack chain.
This method allows attackers to execute operating system commands on Windows systems directly through the file upload dialog, bypassing the need for the Run Dialog (Win + R), and demonstrates how benign features like file uploads can be exploited to gain command execution with minimal user interaction.
The FileFix attack was publicly disclosed in a detailed post by mr.d0x, the same researcher who previously contributed heavily to documenting the ClickFix method. FileFix emerged during the development of new course material for the Offensive Phishing Operations program, prompting deeper experimentation into alternate social engineering vectors. The result is a technique that operates entirely within the browser context but pivots to command execution by exploiting the File Explorer address bar.
At its core, FileFix manipulates the behavior of elements in web pages. When users click the “Choose File” or equivalent button, Windows opens a File Explorer dialog, where the address bar remains fully interactive. It turns out that pasting a specially crafted command into this address bar (e.g., powershell.exe -c ping example.com # C:…) executes it just as it would in a standard Run Dialog or terminal, and Chrome's own process tree confirms that cmd.exe is spawned from the browser session.
mr.d0x
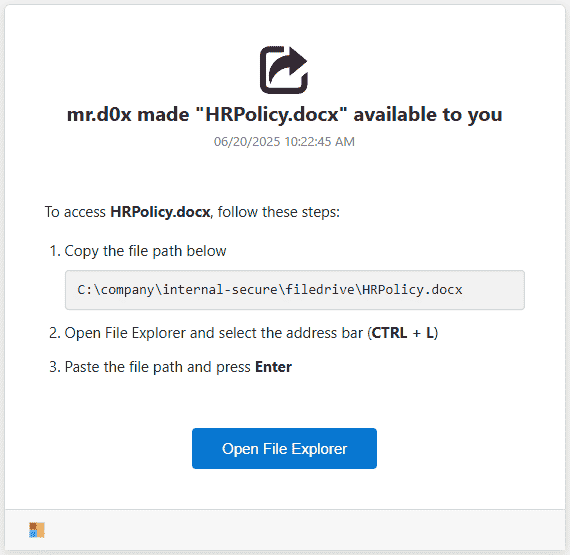
To convince users to perform this seemingly innocuous action, the attacker's phishing page simulates a secure file-sharing portal, instructing users to copy a file path and paste it into the File Explorer address bar. What appears to be a standard file path is, in fact, a comment obfuscating a PowerShell command, which runs unnoticed when executed.
mr.d0x
The phishing page includes a misleading “Open File Explorer” button that both opens the file upload prompt and copies the hidden PowerShell command to the user's clipboard. It also disables normal file uploads to discourage user deviation, alerting users and re-opening the upload dialog if they attempt to select a file. The result is a streamlined interaction funneling victims toward command execution.
FileFix represents a tactical pivot from the original ClickFix method, which relied on tricking users into manually entering or pasting PowerShell commands into the Run Dialog. That technique gained notoriety in 2024 following widespread campaigns uncovered by Sekoia and Proofpoint. ClickFix was used to distribute infostealers like Stealc, Rhadamanthys, and AMOS, typically delivered through spoofed Google Meet pages and executed via HTML or VBScript payloads.
Where ClickFix previously focused on fake popups and dialogue boxes, FileFix weaponizes familiar UX patterns like file uploads and clipboard copying to manipulate users without raising alarms. More alarmingly, mr.d0x notes a variation where executable files downloaded through the FileFix method can be launched with no Mark of the Web (MOTW) flag attached, allowing them to run without SmartScreen or Defender warnings under certain conditions. This happens when users execute the file via the File Explorer address bar, which strips the MOTW metadata in the process.
This subtle but impactful feature makes FileFix not only a command execution vector, but a method to launch downloaded payloads with reduced friction. Although browsers and antivirus products may still intercept the download itself, users who bypass warnings could end up executing unsigned binaries unknowingly, particularly if combined with obfuscation or sideloading techniques.
Security researcher mr.d0x previously demonstrated covert surveillance techniques using Chromium command-line flags, has also shown how attackers with local access can silently capture screenshots, webcam snapshots, and microphone audio by abusing browser features like –auto-select-desktop-capture-source and –auto-accept-camera-and-microphone-capture. These methods bypass user consent prompts and enable real-time monitoring through JavaScript and backend scripts posing a serious post-compromise risk on Chrome-based browsers like Chrome, Edge, Brave, and Opera.







Leave a Reply