
Zimperium's zLabs team has uncovered a new variant of the FakeCall malware, capable of taking full control of Android devices through voice phishing (vishing) aimed at tricking users into disclosing financial information.
First identified by ThreatFabric and Kaspersky, FakeCall has evolved with new capabilities that make it more difficult to detect, allowing attackers to manipulate device functionality remotely and bypass user permissions, as well as capture and control calls.
How FakeCall attacks work
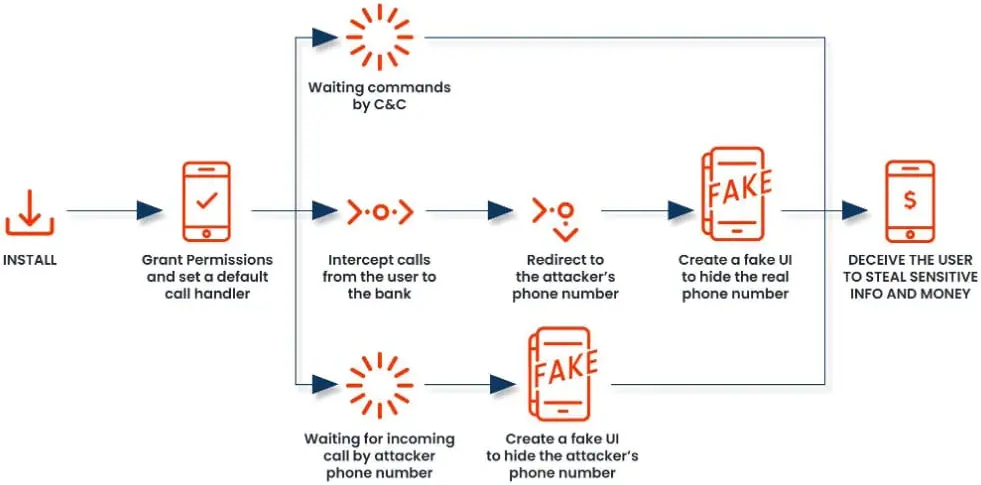
The FakeCall attack begins with a standard phishing attempt, usually a deceptive download link or SMS that lures the victim into installing a malicious APK file, which then downloads a second-stage malware payload. This malware, heavily obfuscated and capable of advanced anti-detection techniques, connects to a remote command-and-control (C2) server to execute commands.
The latest FakeCall variant mimics a standard dialer app on the infected device, intercepting and controlling both incoming and outgoing calls. Users attempting to reach their bank or other financial institution may be unknowingly redirected to attackers posing as customer support, who then extract financial and personal details.
By leveraging Android's Accessibility Service, FakeCall monitors dialer activities and responds to permission prompts without user consent, granting the malware extensive control over device actions. Additionally, by receiving remote commands from the C2 server, attackers can simulate interactions on the device, making unauthorized calls or clicking on-screen elements to further compromise the victim's account security.
Zimperium
New features
The latest FakeCall variant exhibits advanced functionalities that make it a severe security risk to users. These new capabilities are designed to increase the malware's longevity on the device and enable attackers to access a range of sensitive information.
For example, the malware now includes components to detect Bluetooth connectivity and screen states, potentially preparing for more sophisticated behaviors in future iterations. Also, FakeCall can conduct audio recordings, take photos, initiate live video streaming, and control both cameras.
The malware's command set, which has been enriched in the latest version, gives attackers granular control over the infected device, covering a wide spectrum of activities, such as:
- Information collection: The malware uploads device information, call logs, contacts, SMS, and location data to the C2 server.
- Device control: Remote attackers can end calls, manage app installations, take screenshots, start screen video streams, and access camera feeds.
- Data manipulation: FakeCall has the ability to add or delete contacts, delete call logs, and even send or delete SMS messages, enabling attackers to conceal malicious actions.
- Remote interface simulation: Using accessibility services, the malware can simulate taps and button presses, allowing attackers to navigate the device and manipulate it with precision.
To defend against this threat, avoid downloading apps from outside the Google Play store, independently verify caller identities when conveying sensitive information, and keep Play Protect active on your Android device.







Leave a Reply