
In May 2024, the Cleafy Threat Intelligence team identified a new variant of the Medusa (TangleBot) banking trojan, marking a significant evolution in this notorious malware family. Originally discovered in 2020, Medusa's latest version exhibits enhanced capabilities, a streamlined permission set, and a shift in distribution strategies, posing new threats to Android device users worldwide.
Discovery and analysis
The discovery was made by Cleafy's Threat Intelligence team while monitoring fraud campaigns in late May 2024. They noted a spike in installations of an unfamiliar app, “4K Sports,” which exhibited behaviors inconsistent with known malware families. A detailed analysis revealed that this app was linked to a newly evolved Medusa variant, demonstrating substantial changes in its command structure and overall capabilities.
Medusa, known for its sophisticated Remote Access Trojan (RAT) capabilities, has expanded its toolkit to include features such as keylogging, screen control, and the ability to read and write SMS messages. These features enable threat actors to perform On-Device Fraud (ODF), one of the most dangerous types of banking fraud. The latest variant includes new capabilities like displaying full-screen overlays and remotely uninstalling applications, further enhancing its malicious potential.
Evolution and distribution
Initially targeting Turkish financial institutions, Medusa quickly expanded its reach by 2022 to include major campaigns in North America and Europe. The latest campaigns indicate a further geographical spread, now targeting countries such as France and Italy in addition to Turkey and Spain.
Cleafy identified five distinct botnets operated by various affiliates, each with unique characteristics in terms of geographical targeting and decoy methods.
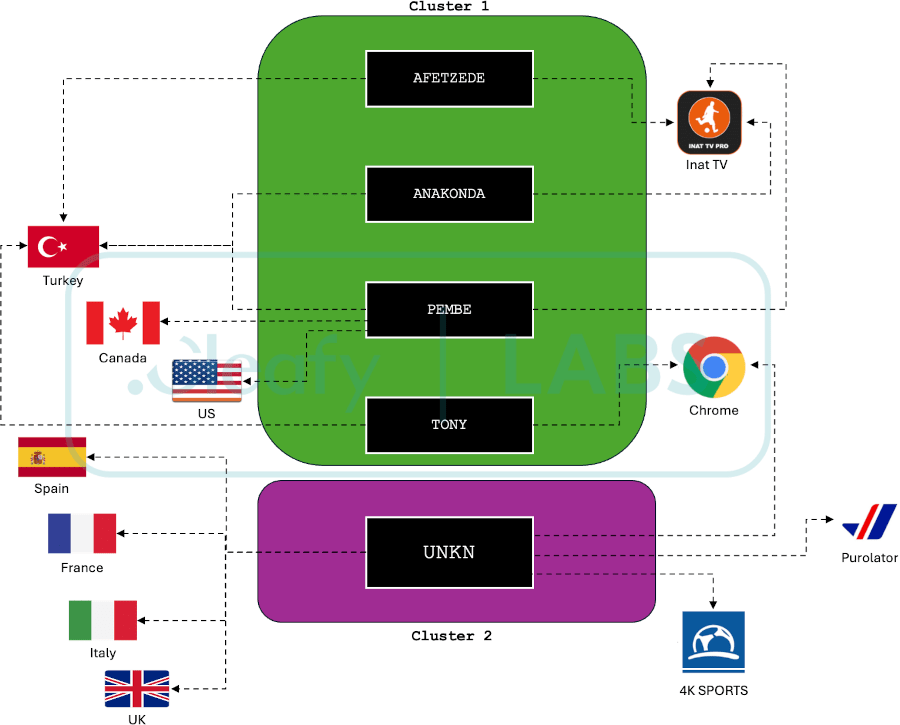
Cleafy Labs
The new Medusa variant employs a “dropper” distribution strategy, delivering the malware via fake update procedures. This method contrasts with traditional phishing tactics, suggesting that threat actors are experimenting with novel techniques to bypass security measures and achieve broader infection rates.
Cleafy's analysis revealed significant changes in the permissions requested by the new Medusa samples. The malware now requires only essential permissions, reducing its visibility during initial scans and making it harder to detect. This streamlined approach includes permissions for Accessibility Services, Broadcast SMS, Internet, Foreground Service, and Query and Delete Packages.
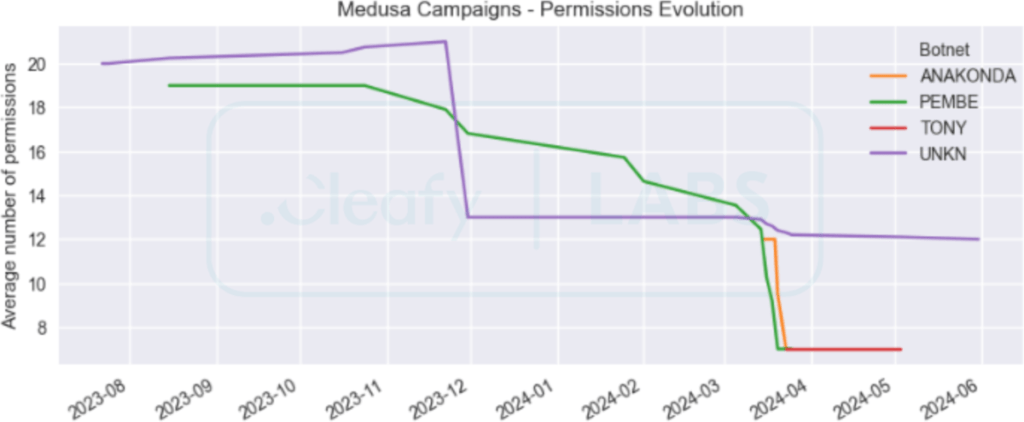
Cleafy Labs
The new variant also shows a refined command set, removing 17 commands from previous versions and introducing five new ones:
- destroyo: Uninstall specific applications
- permdrawover: Request drawing over permission
- setoverlay: Set black screen overlay
- take_scr: Take screenshot
- update_sec: Update user secret
These changes reflect a strategic move to maintain core functionalities while minimizing detection risks, thus enhancing the malware's stealth and reliability.
Defense tips
The emergence of this new Medusa variant underscores the evolving threat landscape in mobile malware. As the malware adapts and refines its methods, cybersecurity professionals must stay vigilant and proactive in their defenses. Users are advised to follow these measures to protect against such threats:
- Ensure all apps and operating systems are up-to-date to mitigate vulnerabilities.
- Only download apps from official app stores and avoid third-party sources.
- Employ reputable mobile security solutions to detect and prevent malware infections.
- Avoid clicking on suspicious links or providing personal information to unverified sources.
- Regularly review app permissions and restrict unnecessary access.
The latest variant of the Medusa banking trojan exemplifies the continuous evolution of malware, with threat actors refining their techniques to stay ahead of detection technologies. The reduced permissions and novel distribution methods highlight the need for enhanced vigilance and adaptive defense strategies. As Medusa expands its reach and capabilities, it remains a significant threat to Android users, necessitating ongoing monitoring and comprehensive security measures.







Leave a Reply