
A critical flaw affecting a broad range of Electron-based applications, including Signal, Slack, 1Password, and even Google Chrome, allows attackers to bypass code integrity checks and backdoor the apps.
The flaw, tracked as CVE-2025-55305, is exploited by tampering with V8 heap snapshot files, internal data used by Chromium-based apps to speed up loading times, allowing adversaries to stealthily embed persistent backdoors into otherwise signed and trusted applications.
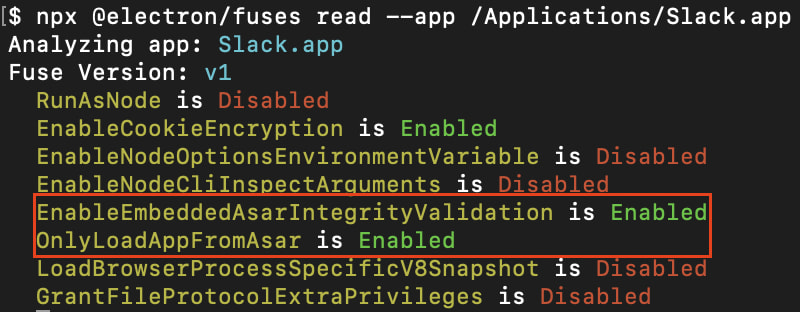
The issue was identified by researcher Darius Houle while exploring the effectiveness of Electron's integrity verification mechanisms, which are meant to prevent execution of tampered JavaScript. Houle found that while Electron supports code integrity enforcement via internal “fuses” like EnableEmbeddedAsarIntegrityValidation and OnlyLoadAppFromAsar, these protections did not extend to the V8 heap snapshot files. These snapshots, used to initialize JavaScript engine contexts, are not directly executable, but they can still be manipulated to alter core JavaScript behavior during runtime.
Trail of Bits tested the exploit on high-profile applications like 1Password, Slack, and Signal, demonstrating how JavaScript functions such as Array.isArray could be hijacked to run attacker-controlled code. The proof-of-concept payloads included a simple keylogger embedded into Slack, showcasing the real-world impact of this vulnerability.
Trail of Bits
1Password, a password management platform used by security-conscious individuals and enterprises, has already addressed the issue in version 8.11.8-40. The company emphasized its commitment to security in a statement from CISO Jacob DePriest, urging users to update to the latest version. Slack and Signal also reportedly responded swiftly to disclosures, though specific remediation details were not publicly shared.
Electron is a widely used open-source framework that enables the development of cross-platform desktop applications using web technologies. Applications built on Electron inherit much of their architecture from Chromium, including the V8 JavaScript engine and its associated snapshot mechanisms. However, unlike executable files, these snapshots aren't covered by operating system-level code signing or integrity enforcement, making them an attractive target for post-installation tampering, especially since most Electron apps are installed in user-writable locations like %AppData%\Local on Windows or /Applications on macOS.
Trail of Bits noted that the attack requires only local file system write access; no privilege escalation or elevated permissions are needed. This makes it feasible for attackers to either modify existing installations or distribute pre-tampered applications that still pass code signature verification. Tools like Loki C2 have already leveraged similar weaknesses in the wild to evade endpoint detection systems and gain persistence through trusted app binaries.
Beyond Electron, the implications of this vulnerability ripple through the broader Chromium ecosystem. Trail of Bits researcher Emilio Lopez expanded on Houle's work by showing that Chrome and other Chromium-derived browsers are similarly susceptible. Although Google's threat model explicitly excludes local attacks, Trail of Bits argues this position underestimates the real-world risk of persistent local compromise through stealthy snapshot manipulation.
Users of affected applications should ensure they are running the latest versions, and generally avoid installing Electron or Chromium apps in user-writable directories when possible, as this leaves them vulnerable to tampering.







Leave a Reply