
A new variation of the well-known clickjacking attack, termed “DoubleClickjacking,” poses a serious security threat to web applications and their users. This novel technique exploits a user's double-click action to bypass all known defenses against traditional clickjacking, including SameSite cookies and X-Frame-Options headers. By taking advantage of timing quirks between mouse events, attackers can manipulate users into unknowingly authorizing malicious actions, such as granting OAuth permissions or altering account settings.
How DoubleClickjacking works
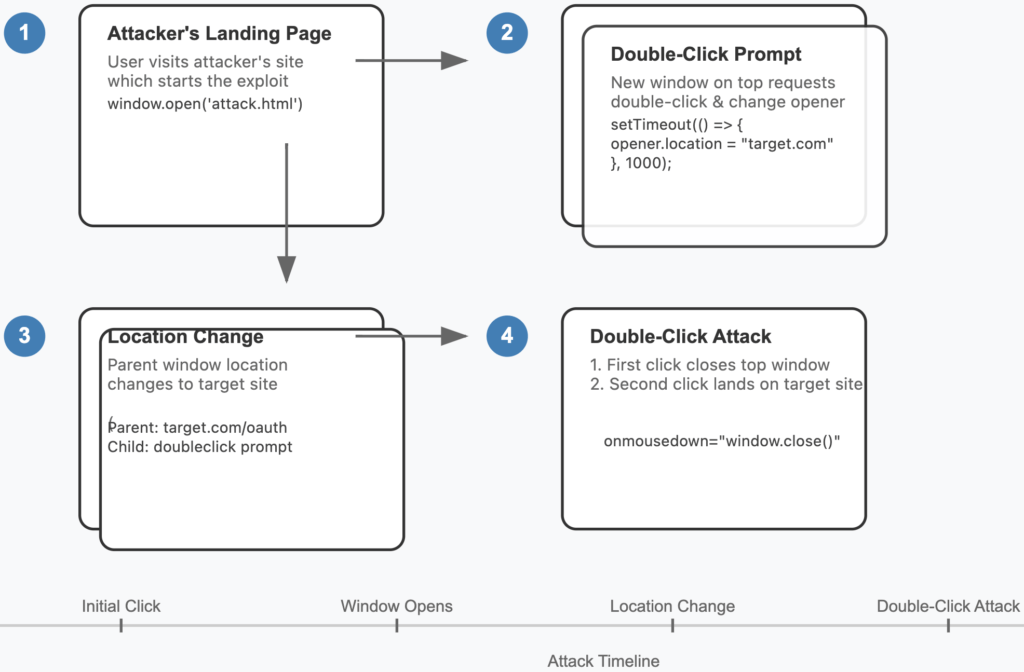
The attack, devised by security researcher Paulos Yibelo involves a deceptive sequence where a user interacts with two browser windows. Here's the breakdown:
- Initial setup: An attacker-controlled webpage opens a new window, presenting a seemingly legitimate prompt like a CAPTCHA.
- Window hijack: Upon the user's first click, the attacker's script manipulates the parent browser window to load a sensitive page, such as an OAuth authorization form.
- Click exploitation: As the user completes the double-click, the second click inadvertently interacts with the now-exposed sensitive page in the parent window, authorizing the attacker's request.
The attack leverages the delay between the ‘mousedown' and ‘onclick' events to execute this swap seamlessly. Importantly, it requires minimal user interaction and works across all major web platforms supporting OAuth APIs, making it a universal threat.
paulosyibelo.com
DoubleClickjacking has been demonstrated on high-profile platforms like Salesforce, Slack, and Shopify. These services, which cater to millions of users worldwide, are particularly susceptible due to their reliance on OAuth for user authentication and API permissions.
Key threats posed by DoubleClickjacking include account takeovers where users unknowingly grant attackers broad API access, and settings manipulation, where attackers can disable security features, change account configurations, or confirm fraudulent transactions. Additionally, the attack could extend beyond websites to include browser-based crypto wallets and mobile apps, further broadening its scope.
Mitigation strategies
Traditional anti-clickjacking measures, such as X-Frame-Options headers and SameSite cookies, are ineffective against DoubleClickjacking. These defenses are designed to prevent single-click attacks but do not account for multi-click scenarios or rapid window context switching. Additionally, the reliance on mouse event timing gives attackers a powerful tool to bypass security controls without raising suspicion.
To combat this new threat, developers and security teams should implement immediate protective measures:
- Client-side defenses: A JavaScript-based library that disables buttons by default and activates them only after detecting genuine user interaction (e.g., mouse movement or keyboard input) can prevent exploitation. Platforms like Dropbox and GitHub have successfully deployed similar protections.
- Long-term browser improvements: Introducing a new HTTP header, such as ‘Double-Click-Protection: strict,' could mitigate this attack by restricting rapid UI changes during a double-click sequence. Expanding content security policy (CSP) capabilities to cover such scenarios is another potential solution.
- Tips for developers: Sensitive pages, especially those handling OAuth, payments, or high-privilege actions, should adopt protective libraries or ensure strict UI validation.







Let’s get rid of captchas forever.