
Security researchers at Kaspersky have uncovered a powerful new commercial spyware named Dante, developed by Italian surveillance vendor Memento Labs, in a campaign that previously exploited a Chrome zero-day (CVE-2025-2783) to compromise high-profile targets in Russia and Belarus.
The discovery connects the spyware to Operation ForumTroll, a long-running cyber-espionage effort first exposed in March 2025.
Kaspersky's technical deep dive reveals that the Dante spyware had been quietly operating in the wild since at least 2022, but only now has it been definitively identified and attributed. The malware was initially misattributed as a separate implant named LeetAgent, but researchers have since linked the two via overlapping infrastructure, infection methods, and shared code. Notably, some attacks deployed Dante through LeetAgent, further confirming their connection.
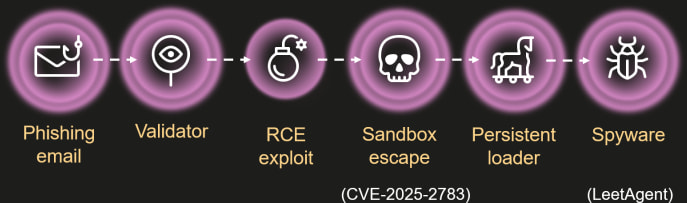
The infection chain used in Operation ForumTroll began with highly targeted phishing emails crafted to appear as legitimate invitations to the Russian “Primakov Readings” expert forum. Victims who clicked the embedded links were redirected to malicious websites that silently exploited a Chrome vulnerability (CVE-2025-2783) to gain code execution. The exploit chain culminated in a sandbox escape using a flaw in how Chrome's Mojo IPC layer interacted with Windows pseudo-handles, allowing attackers to escalate privileges and deploy a persistent malware loader via COM hijacking.

Kaspersky
At the center of the operation was the exploitation of CVE-2025-2783, a logic bug in Chromium's Mojo IPC system that let attackers pass pseudo-handles through Chrome's IPC mechanism. Due to insufficient validation, the renderer process could obtain a real handle to the browser thread, effectively breaking Chrome's sandbox model. This allowed the malware to manipulate thread context and execute shellcode directly in the browser process, leading to full system compromise.
Kaspersky
Memento Labs, previously known as Hacking Team, is one of the most controversial players in the commercial spyware market. Known for its earlier Remote Control Systems (RCS) spyware, the company rebranded after a major 2015 breach that exposed internal documents and client lists. Despite claims of a clean slate, the firm's new product, Dante, appears to carry forward many hallmarks of the old codebase while introducing extensive anti-analysis features and an advanced modular architecture.
The Dante spyware is packed with VMProtect and heavily obfuscated, employing low-level Windows API techniques to avoid detection and bypass hooking-based monitoring. It performs numerous anti-debugging and anti-VM checks, including parsing Windows event logs for signs of analysis tools, detecting sandbox artifacts, and validating execution timing of CPU instructions to detect emulation. The malware decrypts its orchestrator and configuration on the fly, supports AES-256-CBC module encryption, and uses machine-specific keys derived from system hardware and OS identifiers to tie infections to specific targets.
Once deployed, Dante maintains persistence via COM hijacking and operates via a modular orchestrator that handles C2 communication, configuration updates, and plugin loading. Though full functionality remains unknown due to the lack of active infections in Kaspersky's telemetry, analysts observed the orchestrator's ability to load modules from disk or memory and delete itself entirely if it remains disconnected from its command server for too long, a clear indicator of a well-funded and carefully managed spyware operation.
Kaspersky also identified infrastructure overlap with the previously reported LeetAgent spyware, which used command structures written in leetspeak and a simpler feature set focused on keylogging, file theft, and process injection. While LeetAgent was initially considered the primary payload, it now appears to have served as a preliminary foothold or decoy, with Dante handling long-term surveillance.
Despite Memento Labs' apparent attempt to keep Dante under wraps, the presence of the spyware's name in the binary, along with code reuse from prior RCS versions, allowed researchers to make a confident attribution. The name “Dante” is presumed to be a continuation of the company's tradition, following the earlier “Da Vinci” spyware.
At this time, there is no evidence that Dante was used directly in the ForumTroll campaign exploiting CVE-2025-2783, but Kaspersky found similar file system paths, obfuscation methods, and malware loader behaviors across campaigns that involved both tools. Based on these technical overlaps and the sophistication of the malware ecosystem involved, analysts conclude that the same threat actor had access to, or deployed Dante in related espionage operations.







Leave a Reply