
A newly disclosed vulnerability named Brash demonstrates how a fundamental design flaw in Chromium's Blink engine can be weaponized to crash browsers in seconds, potentially impacting billions of users across desktop, mobile, and embedded systems.
Security researcher Jose Pino published the exploit under the MIT license on GitHub just days ago, documenting how uncontrolled document.title updates can be leveraged to saturate the UI thread, rendering the browser unresponsive and ultimately forcing a crash.
According to him, all Chromium-based browsers are vulnerable in current and recent versions, including Chrome, Edge, Brave, Vivaldi, and others. The flaw does not affect Firefox or Safari due to their use of different rendering engines (Gecko and WebKit, respectively).
CyberInsider
Crashing Chrome in seconds
The vulnerability stems from the absence of rate limiting on the document.title API in the Blink engine. Pino's proof-of-concept (PoC), titled Brash, initiates a high-frequency flood of title updates using pre-generated high-entropy strings to avoid browser optimizations and memory caching. This approach enables the exploit to perform millions of DOM mutations per second, effectively choking the browser's main thread.
The attack unfolds in three key phases:
- Preparation: Brash generates 100 unique 512-character hexadecimal strings and stores them in memory to avoid runtime delays and maximize injection speed.
- Burst Injection: The exploit then executes rapid bursts (up to 8,000 updates per millisecond) of document.title changes using a triple-update pattern to thrash the rendering pipeline.
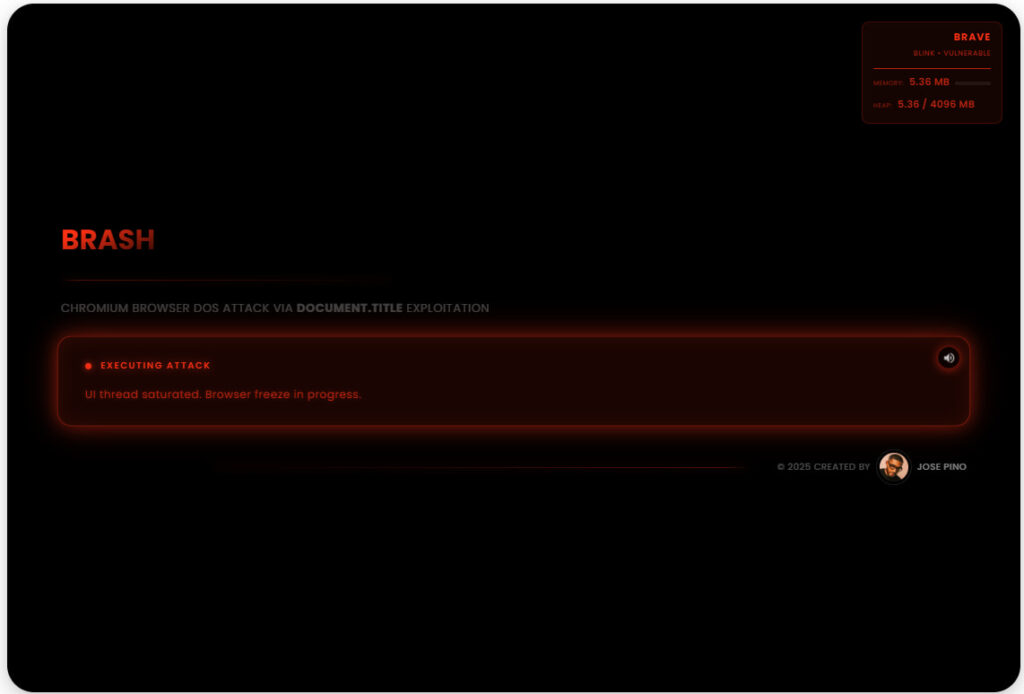
- Collapse: Continuous execution saturates the browser's UI thread, freezes the tab, blocks user input, and eventually forces the entire browser process to crash, typically within 15 to 60 seconds.
Pino tested the vulnerability across 11 major browsers on macOS, Windows, and Linux. All Blink-based browsers exhibited severe failures, while Firefox and Safari remained unaffected.
Scope and impact
Chromium-based browsers account for over 70% of the global browser market, meaning the reach of Brash spans billions of users. The flaw affects Chromium versions up to 143.0.7483.0, with confirmed crashes on versions 138.0.7204.251, 141.0.7390.108, and 143.0.7483.0.
Google's Blink engine, developed to provide high-performance rendering in Chrome and its derivatives, sits at the core of Chromium. Its design handles most DOM operations synchronously on the main thread, which becomes a critical weakness in the case of uncontrolled API calls like document.title.
The exploit is currently operational and publicly accessible via live and local demos.
CyberInsider
However, the real problem arises from the weaponization potential. Pino outlines several high-impact attack scenarios where Brash could cause real-world harm, like:
- Headless Chromium browsers used by AI agents for scraping or compliance monitoring can be silently crashed, halting data pipelines.
- Web-based surgical navigation systems could be brought down mid-operation, risking lives.
- Traders using web terminals could be targeted at critical moments, potentially triggering market instability.
- Banking systems could be blinded during transaction spikes, allowing fraud to slip through undetected.
What makes Brash especially dangerous is its timing flexibility. Using a simple API, attackers can delay or schedule execution, creating opportunities for stealth, trust-building, and well-timed sabotage.
Until Chromium developers address this risk by adding rate limiting for ‘document.title' updates in Blink, users and organizations in mission-critical environments should consider switching to alternative browsers such as Firefox and Safari.







Leave a Reply