
Researchers from Intel 471 have identified a new Android banking trojan named BlankBot, which exhibits advanced capabilities such as screen recording, keylogging, and remote control. Primarily targeting Turkish users, this malware is still under development but poses a significant threat due to its sophisticated design and evasion techniques.
Discovery and analysis
On July 24, 2024, Intel 471 Malware Intelligence researchers detected BlankBot within Android samples disguised as utility applications. The malware could not be linked to any known malware families, leading to the name BlankBot. Initial samples date back to late June 2024, with most remaining undetected by antivirus solutions.
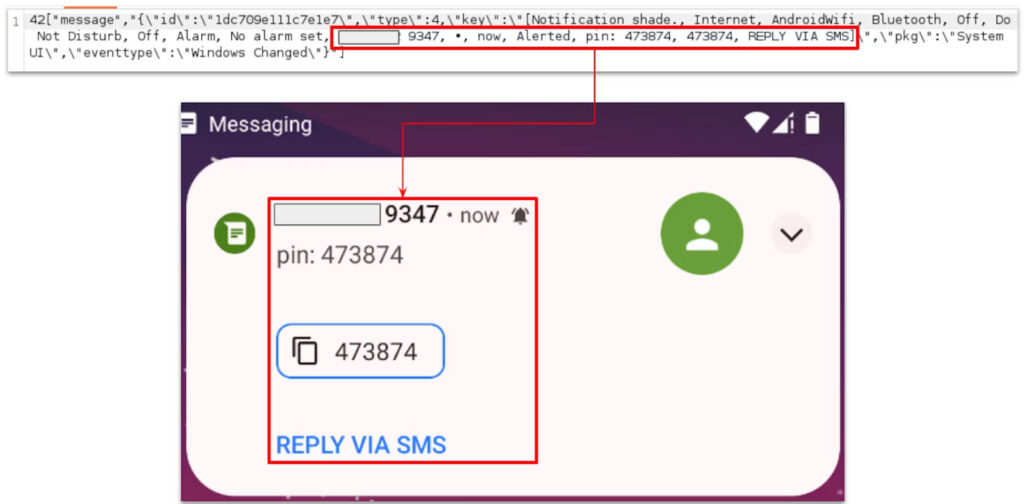
BlankBot leverages Android's accessibility services to gain control over infected devices. It logs information displayed on the device, including SMS texts, sensitive data, and a list of installed applications. The malware can also conduct custom injections to steal banking information, such as payment card data and device lock patterns.
Communication with the control server begins with an HTTP GET request that includes device information, and subsequent communications occur over port 8080 using a WebSocket connection.
Intel 471
BlankBot Capabilities
BlankBot's capabilities are extensive, and include:
- Screen recording: Utilizes MediaProjection and MediaRecorder APIs to capture and save device screen videos as MP4 files, though this feature is still under development.
- Keylogging: Abuses accessibility services to intercept and send keystrokes using a custom virtual keyboard.
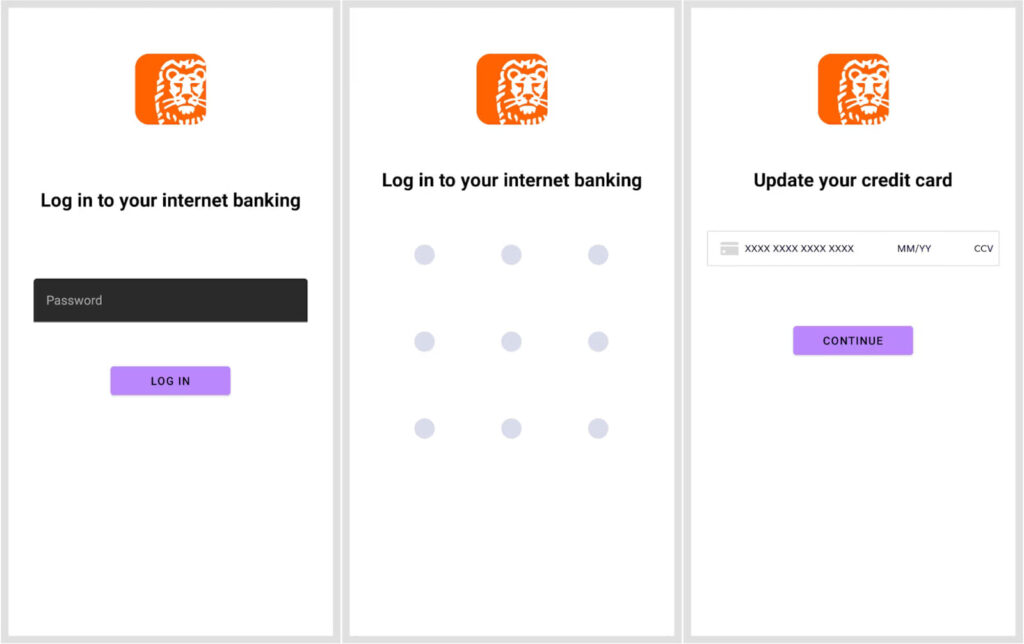
- Custom injections: Can create customizable overlays to solicit banking credentials, personal information, or payment card data. It uses external libraries like CompactCreditInput and Pattern Locker View to implement these injection templates.
Intel 471
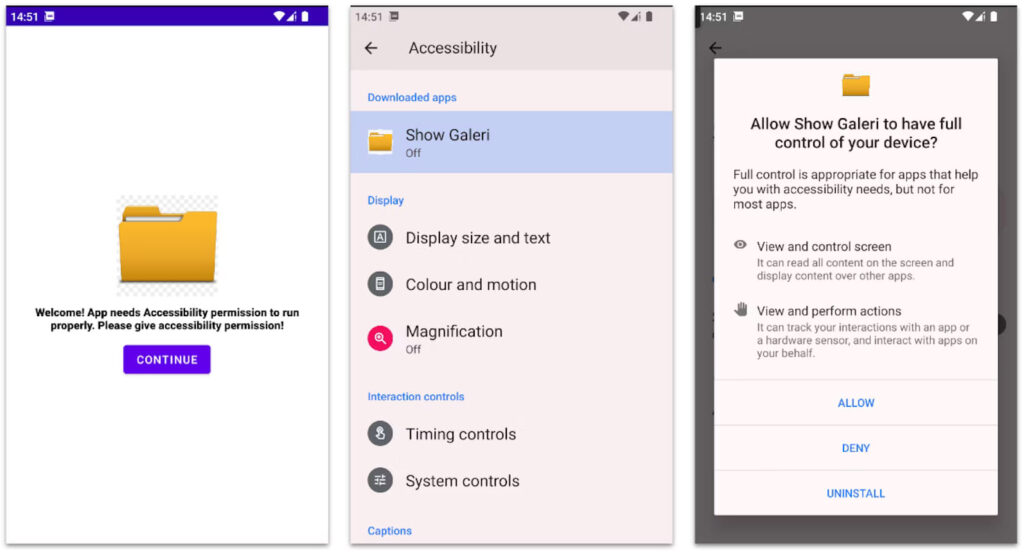
Once installed, BlankBot hides its icon and prompts the user for accessibility permissions with a misleading message. After gaining these permissions, it displays a fake update screen while automatically obtaining necessary permissions in the background. For devices running Android 13 or newer, BlankBot uses a session-based package installer to bypass restricted settings, allowing the installation of applications from third-party sources.
Intel 471
Defense recommendations
BlankBot primarily targets Turkish users, though its potential distribution could expand to other regions if it's rented to other threat actors or the targeting scope of the existing operators is broadened.
The malware employs several evasion techniques, such as checking if the device is an emulator and maintaining persistence by preventing users from accessing settings or antivirus applications. Recent samples include obfuscation and junk code to hinder reverse engineering efforts.
To stay safe from the threat, avoid downloading APK files from outside the Google Play Store, regularly run Play Protect scans, and revoke risky permissions on newly installed apps. Accessibility permissions should never be granted to applications downloaded from third-party sources.






USE AN IPHONE, EVEN IF YOU HAVE TO BUY A USED ONE OR BORROW FROM THE BANK