
A newly identified technique used by credential-stealing malware forces users to input their login credentials into their browsers, allowing attackers to harvest this sensitive data. This method, uncovered by security researchers on August 22, 2024, uses an AutoIt script, in conjunction with the Stealc malware, to target and compromise victims' credential stores by exploiting browser features.
The discovery comes from OALABS with intelligence shared by the Loader Insight Agency, pointing primarily to Amadey malware deployments. Once Amadey infects a system, it deploys Stealc and a credential flusher script to manipulate the victim's browser. This flusher forces the browser into kiosk mode, restricting navigation and coercing users to enter their login information. The credentials, once entered, are stored in the browser and can then be accessed and extracted by Stealc malware.
Forced credentials theft
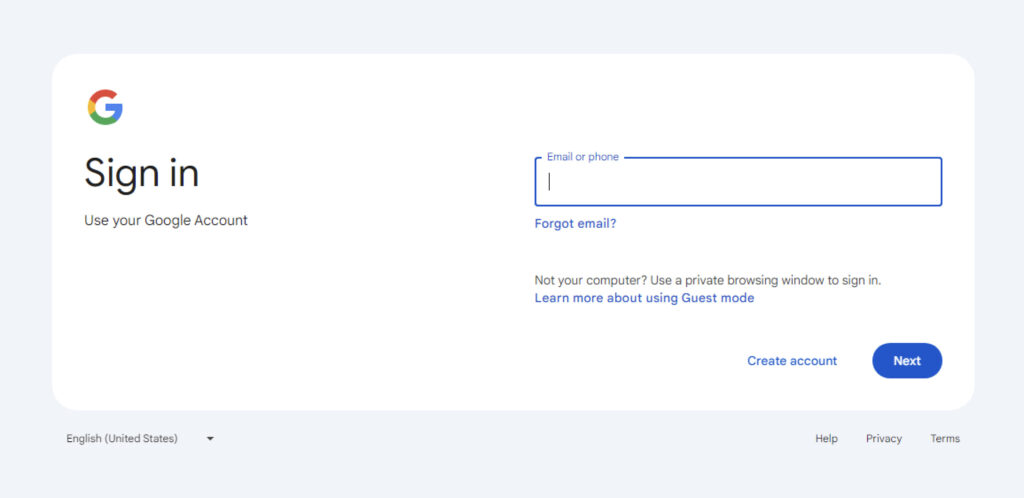
The credential flusher tactic manipulates the victim's browser to launch in kiosk mode, specifically targeting login pages of popular services such as Google. Kiosk mode renders the browser in full-screen, disabling the user's ability to close or minimize the window, thus pressuring them to enter their credentials. This seemingly benign tactic significantly boosts the likelihood of success for credential-stealing malware like Stealc, which operates by retrieving stored passwords once the victim submits them.
Key details of the attack chain include:
- Amadey malware first infects the victim's system.
- Amadey downloads the Stealc malware from a remote server.
- The AutoIt credential flusher is then deployed, coercing the user to enter credentials by simulating legitimate login environments in full-screen kiosk mode.
- Once the credentials are submitted, Stealc retrieves and exfiltrates them.
The AutoIt script used in this attack determines which browser is installed on the system and then forces it to navigate to the target login page in kiosk mode. By leveraging AutoIt's scripting capabilities, the malware restricts users from closing or interacting with the browser in typical ways, increasing the likelihood that they will input their credentials. A sample script example shows a URL pointing to Google's login page, but this could be modified to target any service.
OALABS
The script, once compiled into a binary via AutoIt2Exe, checks for the presence of browsers like Chrome, Edge, or Brave and launches the relevant browser in kiosk mode. If the user attempts to escape this mode by pressing shortcut keys like ESC or F11, the script ignores these inputs, keeping the window active until credentials are entered.
Broader impact
The Amadey malware, already notorious for its modular nature and ability to drop various payloads, is now utilizing this credential flusher technique to increase its effectiveness. Amadey typically operates as a loader, meaning it delivers other types of malware to infected systems, and its use of Stealc for credential theft marks a growing trend in multi-stage attacks.
Given the widespread adoption of popular browsers like Chrome and Edge, this attack has significant potential to compromise a broad range of users, especially those unfamiliar with recognizing kiosk mode as an attack vector.







Leave a Reply