
A recent investigation by Citizen Lab and First Department revealed that spyware resembling the notorious Monokle family was implanted on a device returned to a Russian programmer after his detention. The malware, linked to Russian state-backed entities, demonstrates advanced surveillance capabilities, raising concerns about its use for targeted espionage.
Monokle spyware, first identified in 2019 by Lookout Security, was attributed to the Special Technology Center (STC), a St. Petersburg-based contractor linked to the Russian government. The discovery of this modified spyware reinforces suspicions of its continued use by Russian intelligence agencies for targeted surveillance operations, particularly against individuals perceived as politically adversarial.
Key overlaps with Monokle include shared command-and-control (C2) structures, code segments, and techniques, such as using accessibility settings for enhanced surveillance. However, some differences — like updated encryption mechanisms — suggest either an evolution of Monokle or the reuse of its codebase for a new tool.
Discovery of new spyware variant
The incident centers on Kirill Parubets, a Russian programmer accused of transferring money to Ukraine. Following his detention by Russia's Federal Security Service (FSB), during which he was subjected to coercion and beatings, Parubets's Android device was confiscated. Upon its return, suspicious behavior was observed, including notifications indicative of unauthorized activity. A forensic investigation by First Department — a legal advocacy group — and Citizen Lab identified the device had been compromised with a trojanized application.
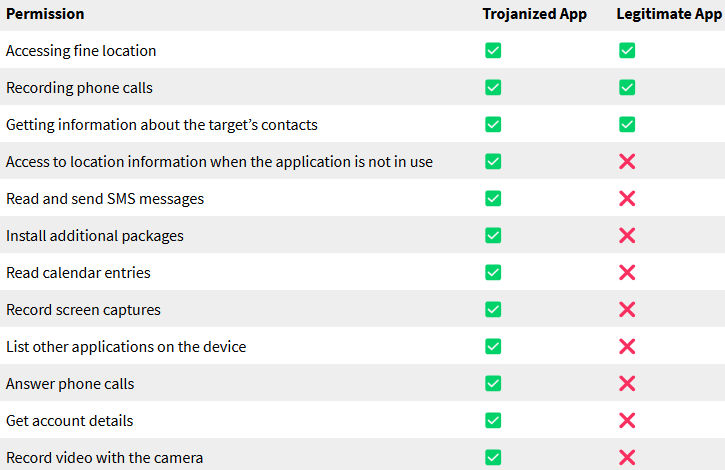
The app in question mimicked the legitimate Cube Call Recorder app, a Google Play Store application for recording phone calls and messaging app communications. However, this version included malicious modifications designed for covert surveillance.

Citizen Lab
The spyware, suspected to be an updated variant or derivative of Monokle, exhibits a broad range of advanced capabilities designed for comprehensive device monitoring and data exfiltration. Key functionalities include:
- Location Tracking: Monitors the target's precise movements in real-time, even when the app is not actively in use.
- Screen Recording and Keylogging: Captures screen activity and keystrokes, allowing attackers to collect sensitive information such as passwords or private conversations.
- Call and Message Surveillance: Records phone calls, accesses text messages and retrieves messages from encrypted apps like Signal or WhatsApp.
- File and Data Extraction: Harvests stored files, photos, and videos and extracts login credentials from the device.
- Remote Control Capabilities: Allows attackers to activate the camera or microphone, install additional software, and execute commands.
- Geofencing and Device Administration: Adds geofencing rules to monitor or trigger actions based on a user's location and establishes itself as a device administrator for persistent control.
Deeper analysis of the spyware revealed sophisticated obfuscation techniques. The malicious app utilizes a two-stage deployment system, with the second stage encrypted and hidden within the app's assets. This stage includes libraries for advanced functions like real-time streaming and remote file uploads. The spyware's permissions far exceed those of the legitimate Cube Call Recorder app, enabling deep access to device systems and user data.
Citizen Lab
Recommendations for targeted individuals
If you're at high risk of state surveillance, a human rights and freedom of speech proponent, or a politically active individual in countries ruled by authoritarian regimes, you should regularly update your device and apps, only use the minimum required number of apps, scrutinize their permissions, and use mobile security tools from reputable vendors.
If you lost physical custody of your smartphone during an arrest or similar situation, replace it after its return from confiscation. If impossible, seek professional analysis of the device to ensure that no spyware has been implanted on it.







Trying to reach at RestorePrivacy but it directs here
Hi Cristopher, yes we merged RestorePrivacy with CyberInsider, explained here:
https://cyberinsider.com/restoreprivacy-com-merges-with-cyberinsider-com/
Thanks Alex
I’ll be following the site content.
Congrats and wishing many many followers and supporters
Thank you very much Christopher!