
Cybersecurity researchers from Cleafy have identified a sophisticated new Android Remote Access Trojan (RAT) called DroidBot. First detected in late October 2024, with traces of activity dating back to June, DroidBot is a Malware-as-a-Service (MaaS) operation, providing advanced tools for surveillance and fraud targeting financial and governmental institutions across Europe.
Cleafy’s Threat Intelligence and Research (TIR) team discovered DroidBot while investigating malware campaigns exploiting Android devices, finding that the new variant has no confirmed connections to existing malware families. The name DroidBot originates from a domain associated with its operation.
Key characteristics of DroidBot include:
- Hidden VNC and overlay attacks allow real-time remote control and interception of sensitive user credentials.
- Keylogging and monitoring to capture user interactions for credential theft.
- Dual communication channels, MQTT for data exfiltration and HTTPS for receiving commands, which enhance its operational flexibility and resilience.
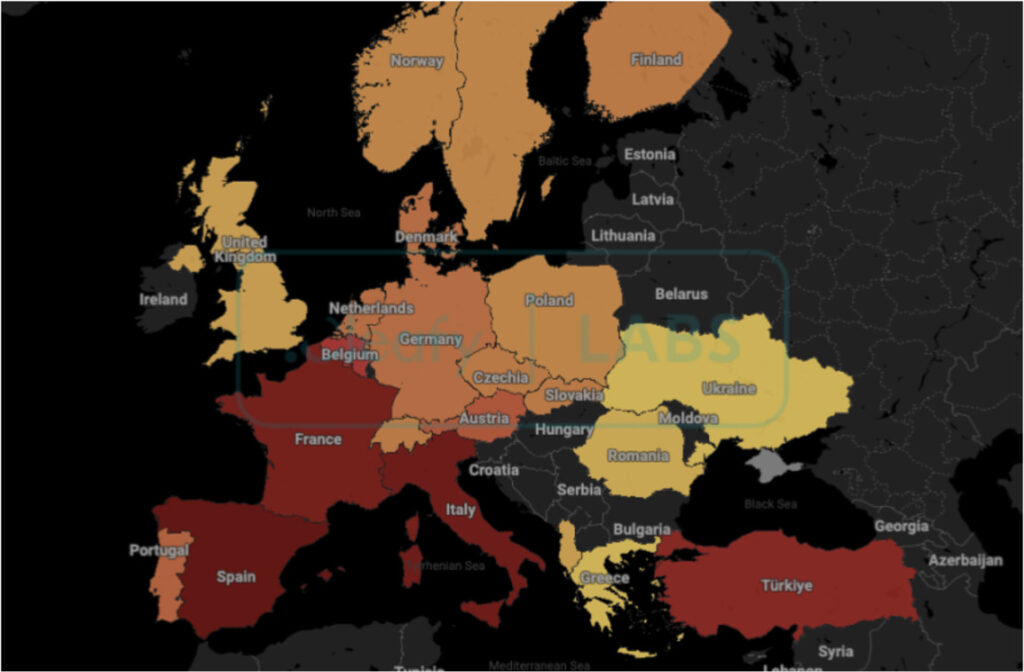
Researchers identified 77 targets, including banks, cryptocurrency exchanges, and governmental organizations in the UK, France, Italy, Spain, and Portugal. The malware is still evolving, evidenced by placeholder functions and varying levels of obfuscation across samples.
Cleafy
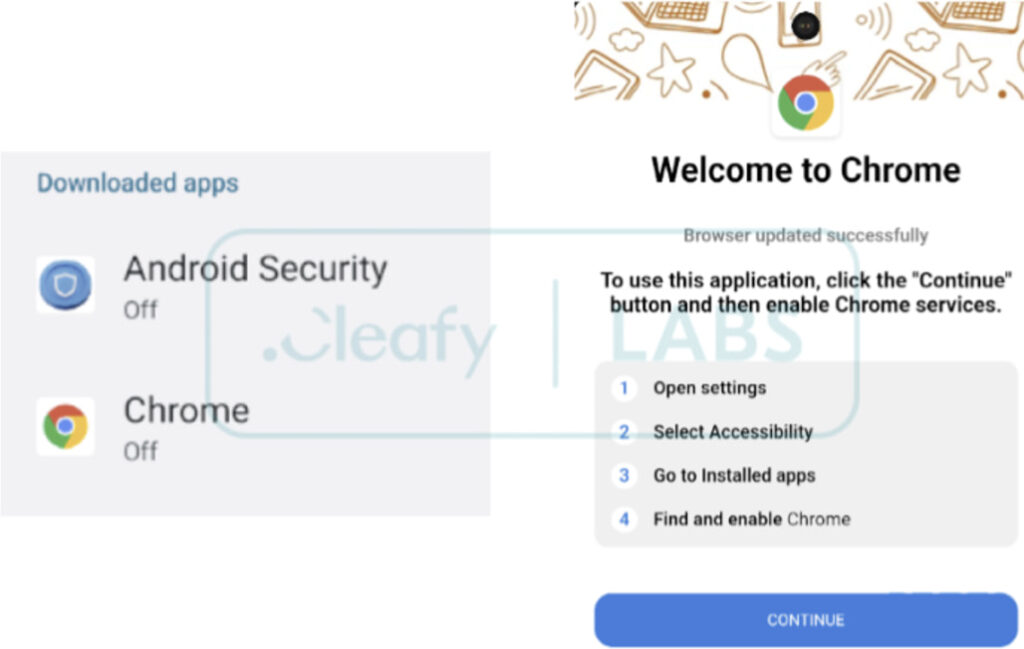
DroidBot also exploits sideloading techniques to infect devices, often masquerading as legitimate apps like Google Play Store or Chrome.
Cleafy
Malware-as-a-Service model
DroidBot operates as a MaaS platform, where its creators sell access to affiliates. These affiliates use malware to conduct their campaigns, which are facilitated by a dedicated infrastructure.
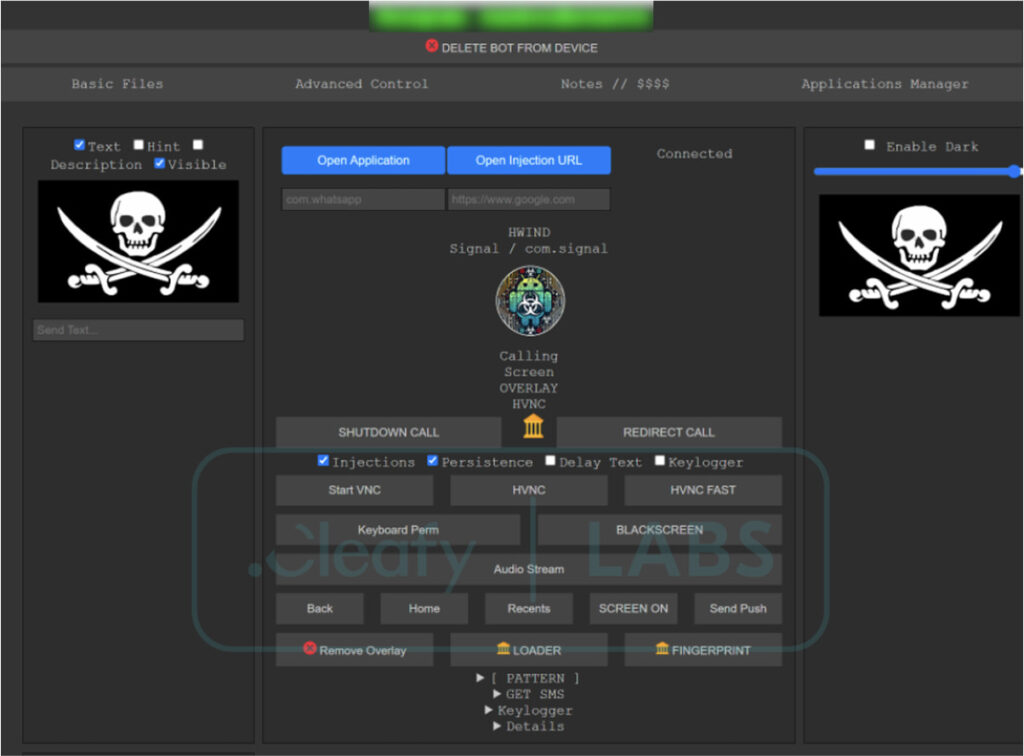
Cleafy identified 17 distinct affiliate groups with unique identifiers in DroidBot samples pointing to multiple operators, some sharing the same infrastructure. The affiliates are given a builder tool that allows them to customize the malware for specific targets. The operation also provides a command and control (C2) panel from where affiliates can perform remote device control, credential harvesting, and injection attacks through a centralized dashboard.
Cleafy
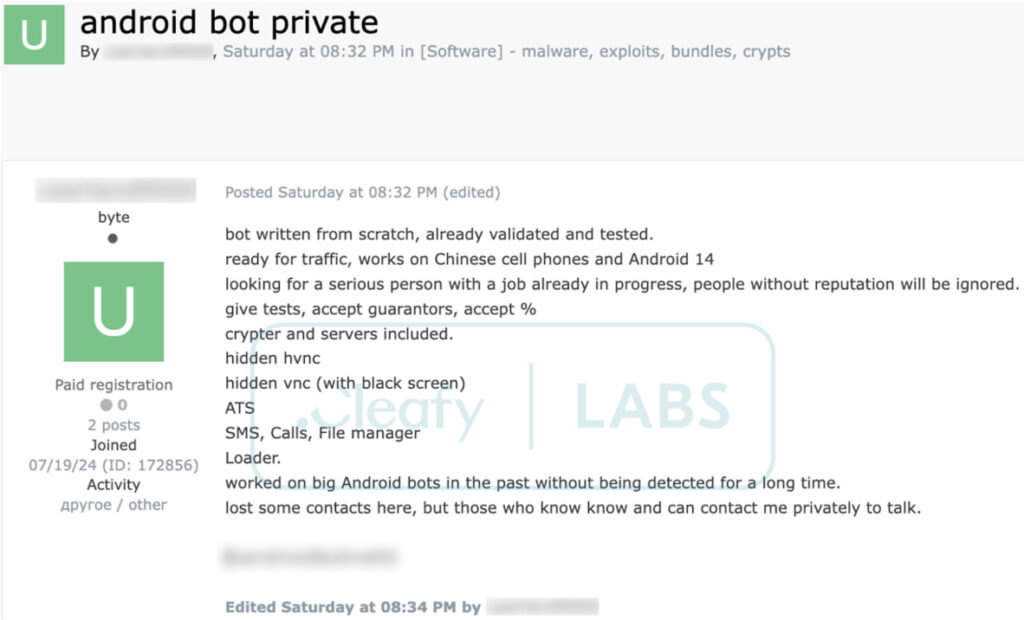
Advertising on Russian-speaking forums, DroidBot’s creators promote features like automated transfer systems (ATS) and remote device control for $3,000 per month. Analysis of leaked Telegram posts and screenshots suggests a strong connection to Turkish developers, as revealed by language settings and geolocated metadata.
Cleafy
DroidBot employs a mix of common and uncommon techniques in the Android malware space.
- The malware requests Accessibility Service permissions during installation, enabling it to intercept user input, control screens, and execute overlay attacks.
- Rare in Android malware, the MQTT protocol is used for C2 communications, allowing stealthy and efficient data transfer.
- Dynamic updates retrieving the C2 server details via encrypted Base64 messages to enhance adaptability and resilience against takedowns.
To mitigate DroidBot’s risks, users should avoid sideloading apps and only install applications from the Google Play store. Also, users should deny accessibility permissions unless necessary for the app’s functionality. Finally, users should ensure that Google Play Protect is always running on their devices. Android’s default anti-malware tool is constantly updated with new virus definitions and is capable of detecting and blocking threats like DroidBot.







Leave a Reply