
A new Android banking trojan named “ToxicPanda” has started spreading across Europe and Latin America, primarily targeting banking institutions with advanced techniques for account takeover and financial fraud.
Discovered by Cleafy's Threat Intelligence team in late October 2024, this malware originated from a similar malware family named TgToxic, previously seen in Southeast Asia. While TgToxic had limited reach, ToxicPanda has managed to infect over 1,500 devices in Italy, Portugal, Spain, France, and Peru, marking a rare instance of Chinese-speaking cyber actors expanding banking fraud operations beyond Asia.

Cleafy
ToxicPanda's capabilities
ToxicPanda leverages a range of tools for “On-Device Fraud” (ODF), allowing attackers to initiate unauthorized transactions directly from infected devices. This tactic bypasses security measures by exploiting device access to mimic legitimate user behavior. The malware's functionalities include:
- Accessibility service abuse: ToxicPanda uses Android's accessibility features to manipulate settings, control input fields, and perform hidden actions within banking applications.
- Remote control: With full remote access, attackers can interact with compromised devices, conduct fraudulent transactions, and modify account settings.
- OTP interception: ToxicPanda intercepts one-time passwords sent via SMS or app-based authenticators, bypassing two-factor authentication and facilitating unauthorized transactions.
Expansion and evolution
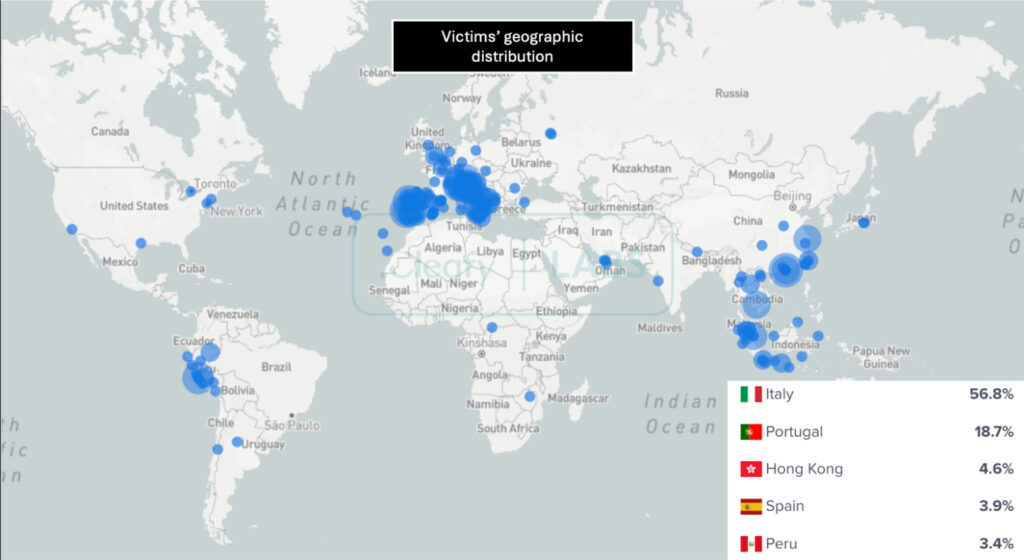
Cleafy reports that this malware campaign has an active botnet controlling infected devices, with Italy identified as the primary hotspot, holding over 50% of cases, followed by Portugal and Spain. This distribution signals a strategic shift from its developers, who are adapting their operations to target European financial institutions.
Cleafy
According to Cleafy, the actors behind ToxicPanda appear to be Chinese-speaking, an uncommon origin for banking fraud targeting Europe and Latin America. While the code maintains similarities with TgToxic, many functions appear underdeveloped, suggesting the malware is in its early stages or undergoing adaptation to new target regions.
Cleafy
ToxicPanda is an advanced yet simplified iteration of its predecessor, lacking some sophisticated obfuscation features and relying instead on a few hardcoded Command and Control (C2) domains (e.g., dksu[.]top and mixcom[.]one). The malware uses AES encryption for communication, though its static configuration highlights a need for ongoing refinement. This simplicity may be due to regulatory challenges in Europe, such as PSD2, and limitations in targeting Western banking infrastructure.
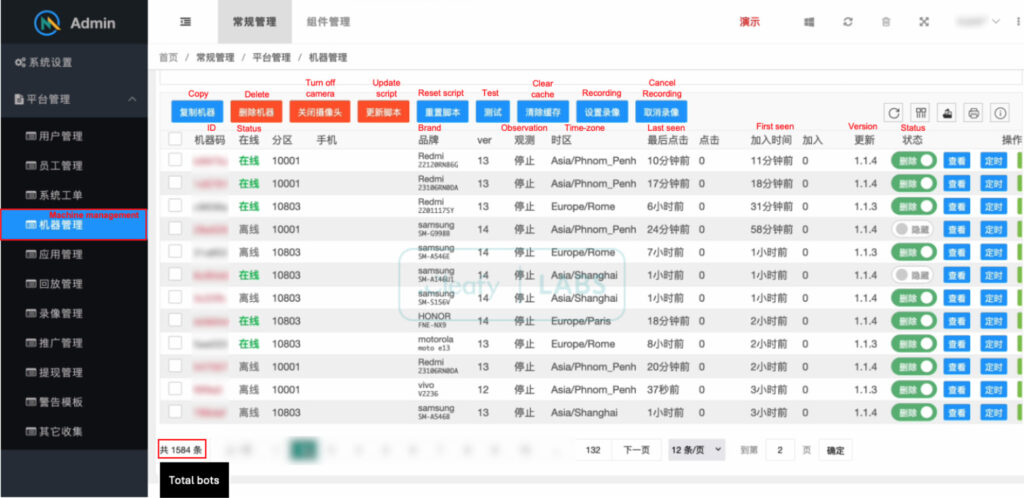
Key to ToxicPanda's operations is its use of a C2 infrastructure, enabling fraud operators to monitor and control infected devices. Through a dedicated “Machine Management” interface, threat actors can track each infected device's status, location, and device specifications, allowing them to conduct region-specific fraud. Infected devices are also monitored for security and configuration changes that might hinder fraudulent activities, allowing attackers to maintain persistent access.
Cleafy
ToxicPanda's appearance outside Southeast Asia highlights a growing trend of regional cybercrime expansion. With the malware still in an evolving phase, vigilance in tracking updates and enhancing Android device protections remains essential to mitigating the risk posed by this emerging banking trojan.
Android users can minimize the risk by only downloading apps from Google Play Store, keeping Play Protect active on their device, and protecting their bank accounts with multi-factor authentication.







Leave a Reply