
Security researchers have identified several critical vulnerabilities in the Netgear WNR614 router, a device known for its reliable connectivity and user-friendly interface. These vulnerabilities, if exploited, could allow unauthorized access and the retrieval of sensitive data, posing significant security risks.
The affected model is the Netgear WNR614 JNR1010V2 N300, specifically firmware version V1.1.0.54_1.0.1. Notably, this model reached its End of Service (EOS) in 2021, which means it no longer receives security updates or support from Netgear.
Netgear flaw details
Improper Authentication (CVE-2024-36787): Attackers can bypass authentication and access the router's administrative interface through unspecified methods. Weak authentication protocols allow for insecure passwords, significantly increasing the risk of unauthorized access and data breaches.
Users should disable remote management, use strong passwords, change them regularly, and implement network segmentation to protect critical systems.
Cookie Without HTTPOnly (CVE-2024-36788): The router fails to set the HTTPOnly flag for cookies, allowing attackers to intercept communications. This vulnerability could lead to unauthorized access to sensitive data and compromise network security.
A solution is configuring the router to use HTTPS for all communications and using browser security features to enforce secure connections.
Password Policy Bypass (CVE-2024-36789): Attackers can create passwords that do not meet the security standards, bypassing password policies This allows for insecure passwords, making the network susceptible to unauthorized access and data manipulation.
The mitigation recommendation is to implement and enforce a strong password policy, use third-party security software, and regularly audit password practices.
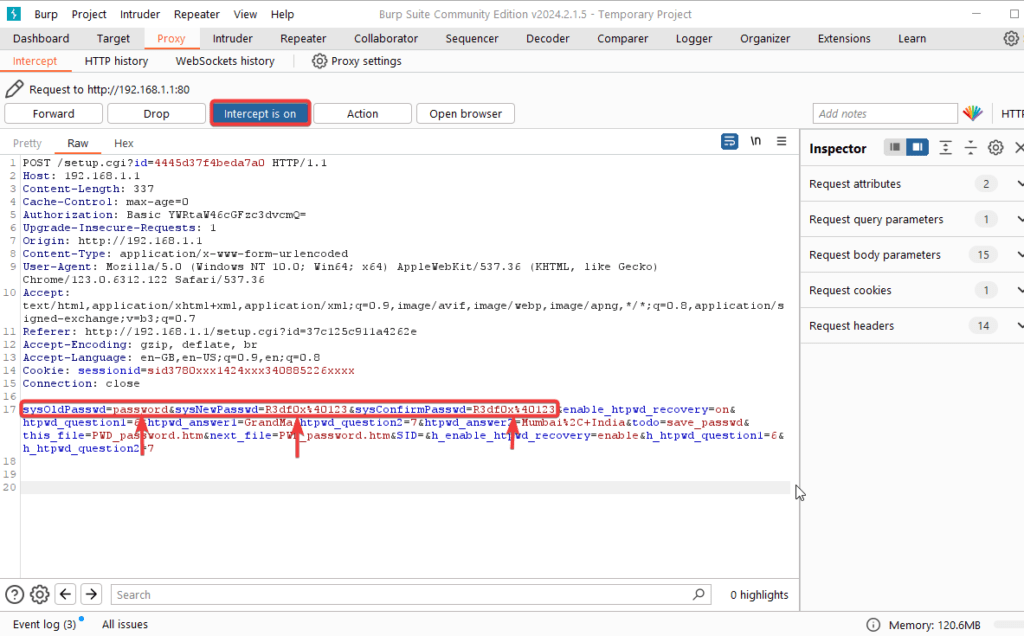
Password Storage in Plaintext (CVE-2024-36790): The router stores credentials in plaintext, posing a significant security risk. Storing sensitive information in cleartext can lead to unauthorized access and manipulation of network settings.
RedFox Security
A proposed solution is to encrypt stored credentials and regularly change passwords while also monitoring for unauthorized access.
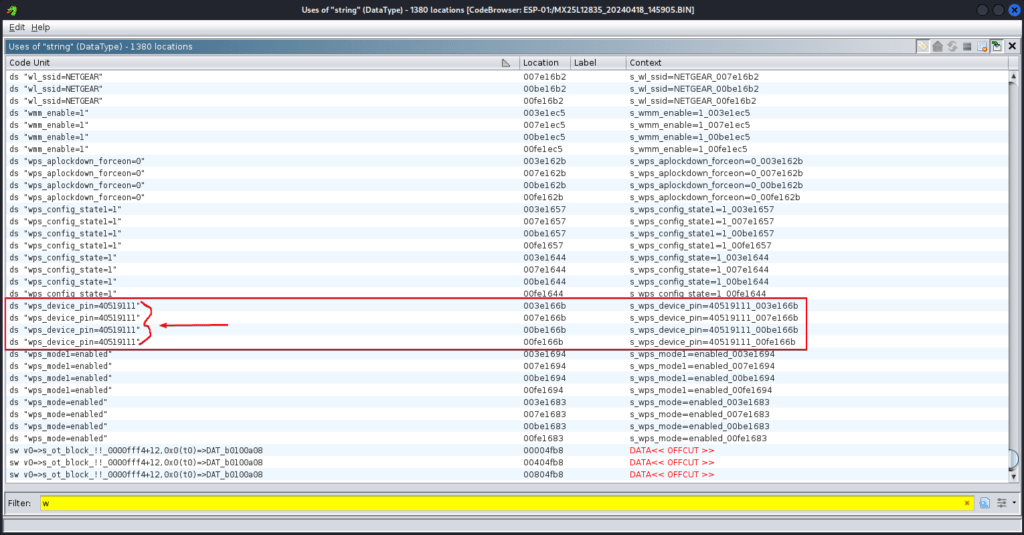
WPS PIN Exposure (CVE-2024-36792): Flaws in the WPS implementation allow attackers to access the router's PIN. Exploiting this vulnerability could lead to unauthorized network access and setting manipulation.
RedFox Security
Disabling WPS functionality, using WPA3 if supported, and regularly monitoring WPS settings are recommended.
Insecure Permissions (CVE-2024-36795): Due to insecure permissions, attackers can access URLs and directories within the firmware. This could result in unauthorized access to sensitive data and control over router settings.
Users should implement access control measures and encrypt sensitive data stored on the router.
Given that the Netgear WNR614 N300 router is no longer supported, it is highly recommended that this model be replaced with a newer, actively supported router. In the meantime, applying the mitigations outlined above is essential to securing your network against potential exploits.







Leave a Reply