
Kaspersky researchers uncovered a new version of the Necro Trojan that has infected millions of Android devices via popular apps, both from Google Play and unofficial sources. The malware uses advanced techniques like obfuscation and steganography, making it difficult to detect. Applications such as Wuta Camera and Max Browser were found to be infected on the Google Play Store, while unofficial versions of Spotify and WhatsApp mods were also compromised, impacting over 11 million devices.
Necro on Google Play
The Necro loader infected two notable apps from Google Play: Wuta Camera and Max Browser. Wuta Camera, downloaded over 10 million times, contained Necro starting from version 6.3.2.148. The malicious code remained embedded in subsequent versions, including 6.3.6.148, until Kaspersky reported it to Google, resulting in the removal of the loader in version 6.3.7.138. Similarly, Max Browser, with over a million downloads, was infected, starting with version 1.2.0. This app was also taken down after the discovery.
Kaspersky
Apps from unofficial sources
The malware was also found in unofficial versions of popular apps like Spotify Plus (distributed via “spotiplus[.]xyz”) and various WhatsApp mods such as GBWhatsApp and FMWhatsApp. These versions, commonly found on third-party websites, claimed to offer enhanced features but were instead laden with the Necro Trojan. The infection vector often came from ad modules integrated into these modified apps. The Trojan also spread via game mods for Minecraft, Stumble Guys, and Car Parking Multiplayer.
Kaspersky
Malicious SDK
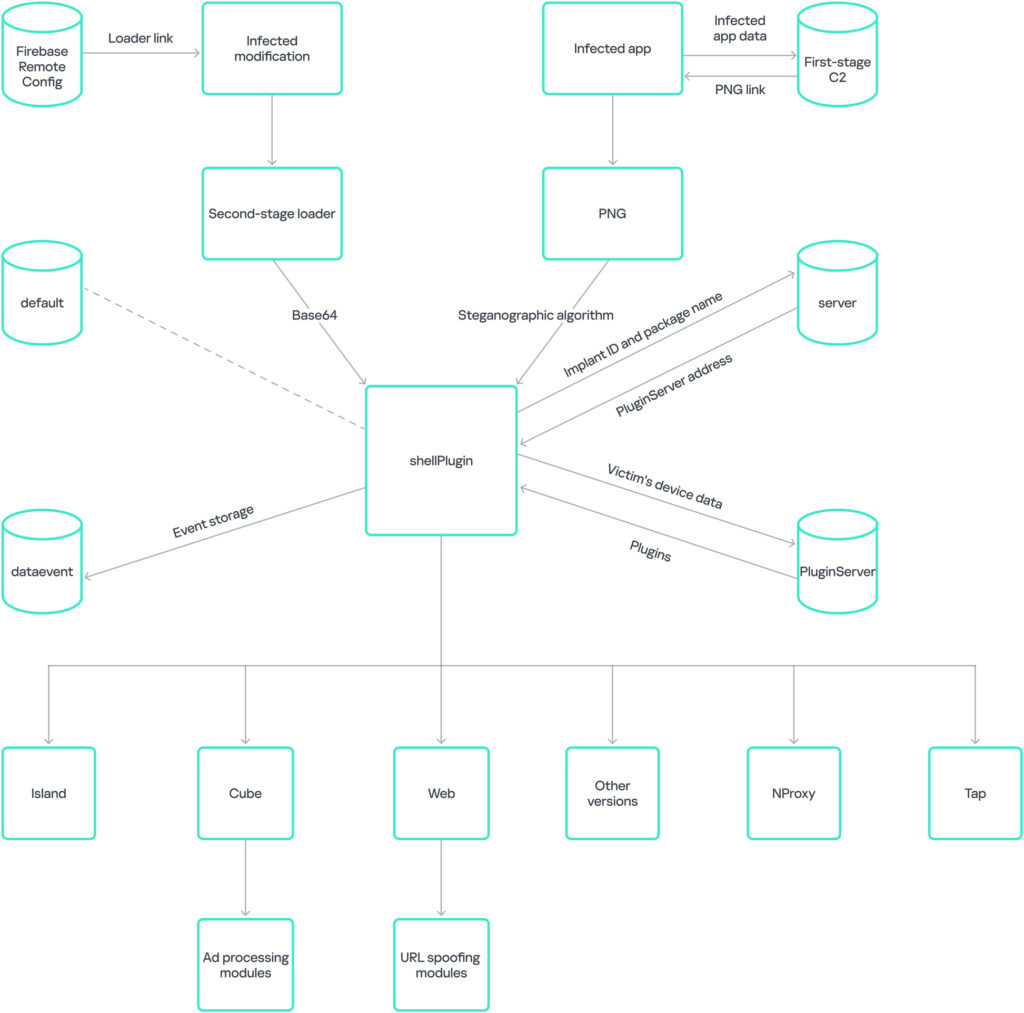
The Necro Trojan relies on a malicious SDK (Coral SDK) which is embedded in the infected apps. Once the SDK is initialized, it communicates with command-and-control (C2) servers, sending encrypted data about the device and app through a POST request.
The C2 server responds with instructions, including a link to download a seemingly benign image file. This image hides the second-stage payload, which is extracted using steganography. The least significant byte in the image's blue channel contains the payload encoded in Base64. This payload is then executed using DexClassLoader or similar mechanisms.
Once installed on a device, Necro can:
- Download and run arbitrary code, including DEX files and additional malicious apps.
- Open WebView windows in the background to interact with ads, generating fraudulent revenue.
- Install other applications silently or subscribe users to premium services without their knowledge.
- Create a tunnel through the device using modules like NProxy, allowing attackers to route malicious traffic.
- Regularly send device data, such as IMEI, OS version, and whether debugging tools are enabled, back to its C2 servers.
The malware's modular architecture allows it to dynamically load new features or functionalities, making it highly adaptable. In some cases, Necro's plugins, such as Web or Island, are used to display ads at random intervals or open malicious websites in the background. Other plugins, like Happy SDK or Cube SDK, are designed to help Necro evade detection or further download additional payloads, expanding its capabilities on infected devices.
Kaspersky
User recommendations
If you downloaded Wuta Camera previously, upgrade to the latest version and run a complete AV scan on your device. Max Browser should be uninstalled, as there's no known clear version.
Regarding apps outside Google Play, those should be avoided entirely unless the user knows and trusts the publisher/creator.
Whenever installing a new app, monitor its battery and data consumption for a while to uncover any background activity that may be taking place.







Leave a Reply