
A security audit of Mullvad VPN's web application by Assured Security Consultants found no critical, high, or medium-risk vulnerabilities, affirming the platform's robust security posture.
The audit surfaced only one low-severity input validation flaw, promptly resolved by Mullvad, and several minor issues without security impact.
Based in Sweden, Mullvad VPN is a privacy-first, no-logs VPN service operator that has a good reputation, transparency, and strong security practices.
Assured's penetration test was conducted between August 11 and August 22, 2025, with follow-up verification completed on September 26. The assessment included Mullvad's primary web application, its administrative CMS, the Tor-based Onion service, and the rsync setup used for synchronizing static web content. The scope deliberately excluded backend APIs and payment services.
Key audit findings
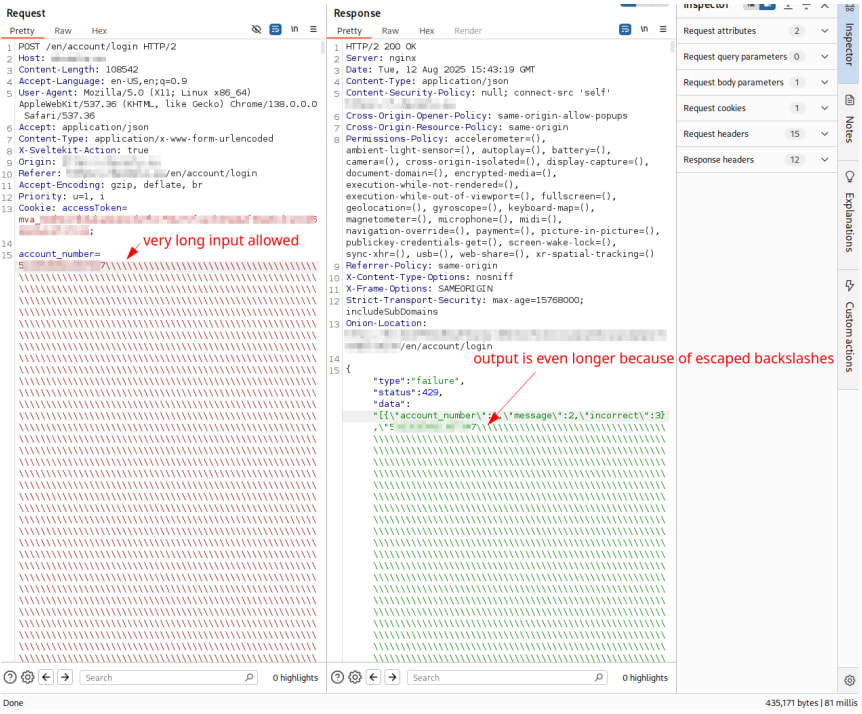
The only security-rated issue found during the assessment was the lack of input length restrictions on fields such as account numbers and voucher codes. Attackers could submit oversized strings, up to 500,000 characters, resulting in error messages that reflected the raw input and consuming excessive server resources. While no denial-of-service condition was observed, this behavior could have been exploited to degrade performance or produce verbose error logs. Mullvad has since enforced strict application-layer input validation and sanitized error responses to eliminate these issues.
Five additional observations were labeled as “Notes” without security impact. These included:
- A misconfiguration where a null value appeared in the Content Security Policy (CSP) header for non-HTML responses. This was fixed by returning CSP headers only where appropriate.
- Two error-handling issues where malformed headers or content types (such as text/plain instead of expected types) triggered 500 Internal Server Errors. These now return appropriate 415 responses or are gracefully handled.
- An overly permissive Cross-Origin Resource Sharing (CORS) header (Access-Control-Allow-Origin: *) in the CMS, which has been corrected to enforce stricter origin policies.
- Access to a development version of the CMS over the Tor Onion service, which was non-functional due to CSRF protection. This path has been blocked entirely.
- One non-security-impacting issue where an unhandled error can be triggered by modifying the Host header in login requests. This was acknowledged but not fixed, as it requires changes in the SvelteKit framework and does not pose a practical risk.
Assured commended Mullvad for several proactive implementations that reflect a mature security posture. The web application achieved an A+ rating for its use of HTTP security headers, including a robust Content Security Policy (CSP), HTTP Strict Transport Security (HSTS), a restrictive Referrer Policy, and correctly configured X-Content-Type-Options. The Tor Onion service was found to be well-isolated, operating in a minimal Docker environment and deliberately excluding features such as IP checks and credit card payments to maintain user anonymity. Similarly, the rsync service used to synchronize static content is confined to a hardened Docker container, relies on SSH key authentication, and is tightly scoped to avoid unintended access.
Finally, the administrative CMS was praised for being completely inaccessible from both the public internet and Mullvad's own VPN, ensuring that content management is restricted to authorized internal networks only.
Assured concluded that Mullvad maintains good security hygiene across its web services. Their recommendations focused on improving error handling, fine-tuning CSP behavior, and maintaining strict input validation.







Wait, Mullvad have a web app? As in, a progressive web app that allows control of their VPN connection via a web browser engine?