
Mullvad VPN has introduced QUIC obfuscation support for WireGuard connections on all desktop platforms, aiming to enhance connection reliability in restrictive networks and assist users in circumventing censorship and firewall-based blocking.
The new feature, introduced in version 2025.9 of the Mullvad desktop client, encapsulates WireGuard traffic using the QUIC protocol, disguising it as regular web traffic to evade detection. QUIC obfuscation relies on the MASQUE protocol (RFC 9298), which enables the tunneling of UDP through HTTP/3, making it significantly harder for state-level censors and network administrators to distinguish VPN usage from ordinary internet activity.
This update is particularly relevant for users in countries where VPN protocols such as WireGuard are routinely blocked or throttled. In such environments, traditional obfuscation methods may no longer suffice, prompting the need for more resilient techniques like QUIC tunneling.
Mullvad VPN, a Swedish privacy-focused VPN provider known for its no-logs policy and anonymous account system, continues to develop advanced features to maintain connectivity under hostile network conditions. The company previously implemented multiple obfuscation layers but now turns to QUIC, a protocol originally developed by Google and now a foundational part of HTTP/3, to blend VPN traffic seamlessly into legitimate web communication.
Technically, QUIC obfuscation builds on MASQUE (Multiplexed Application Substrate over QUIC Encryption), a set of extensions for HTTP/3 that allows proxying of UDP packets. When enabled in the Mullvad client, WireGuard packets are encapsulated in HTTP/3 sessions over QUIC, creating a traffic profile that closely mimics that of a typical web browser. Since blocking HTTP traffic would break large portions of the internet, this approach makes it far riskier for censors to disrupt QUIC-tunneled VPN traffic without causing collateral damage.
Mullvad
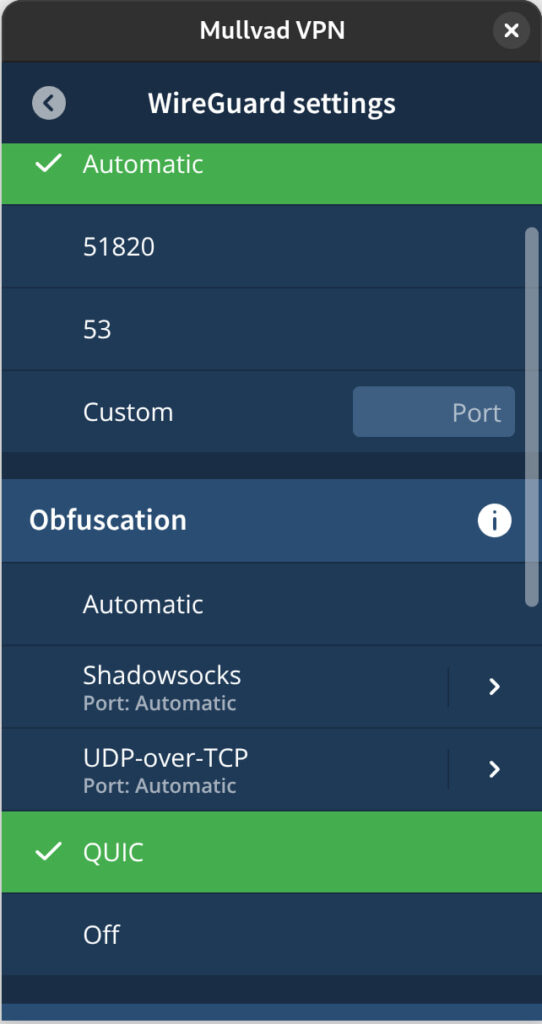
Users running version 2025.9 or later of Mullvad's desktop app can enable the feature either through the GUI (Settings → VPN Settings → WireGuard Settings → Obfuscation → QUIC) or by issuing the terminal command mullvad obfuscation set mode quic. By default, the client will attempt to use QUIC obfuscation automatically after several failed connection attempts, though this behavior can be configured manually.
Support for QUIC obfuscation is expected to arrive on Android and iOS in future updates.







Caution! QUIC at Mullvad is absolutely dubious and half-baked!
QUIC ONLY works if you deactivate DAITA and Multihoop in the app and there are only around 15 servers or even less so, there is no consensus. that supposedly work. Here is the discussion: https://github.com/mullvad/mullvadvpn-app/issues/8742
The customer will neither be informed about this in the blog nor in the app after the update!
Problems with all security features, such as DAITA, Multihoop etc. and then QUIC:
– Page structure extremely slow until page does not open!
– Streams don’t work and you’re in a constant loop!
– YouTube videos load extremely slowly!
– Twitter (X) can hardly be opened!
– And if the Mullvad Proxy Addon is activated in the FF, then you have a party, then no page opens and everything is blocked!
The customer was not informed about any of this and wonders why everything is going worse and worse!
Stay away from Mullvad`s QUIC! It is unsuitable and not made for everyday use!
What Mullvad has done here is dubious.