A severe vulnerability, designated as CVE-2024-36877, has been discovered in the firmware of MSI motherboards, potentially allowing attackers to execute arbitrary code within the highly privileged System Management Mode (SMM).
The flaw affects a broad range of MSI motherboards, including those equipped with Intel 300 through Intel 700 chipsets, as well as AMD AM4 and AM5 platforms.
Vulnerability overview
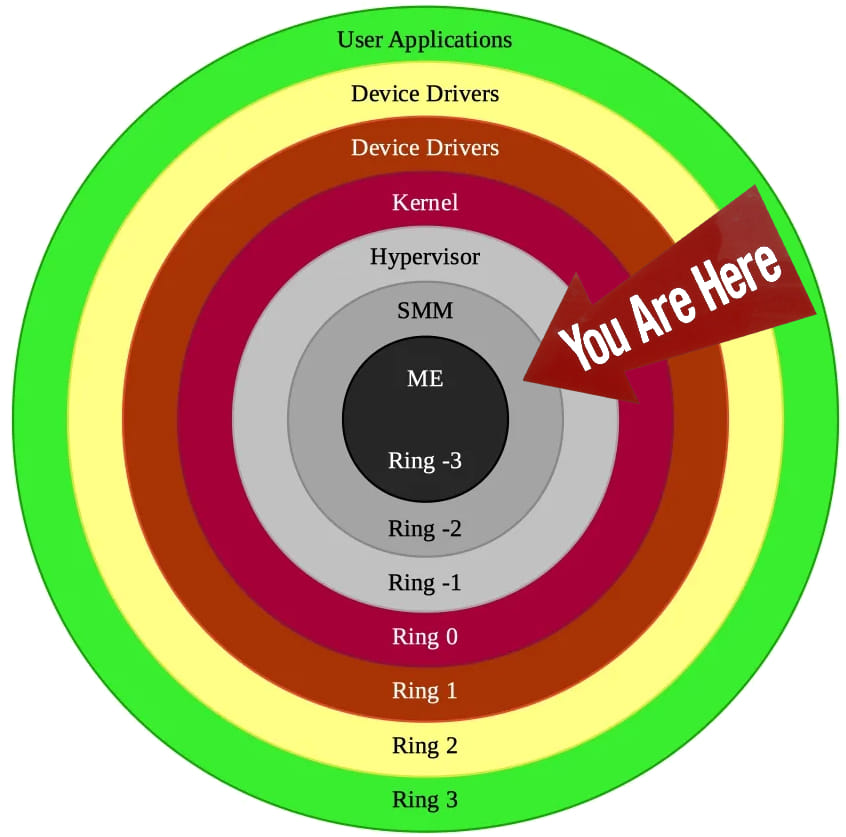
This vulnerability was discovered by security researcher Jared Jensen, who detailed his findings in a comprehensive write-up. The flaw is a buffer overflow in the SMM driver, which can be exploited by attackers to gain code execution within the System Management RAM (SMRAM). This area of memory is reserved for the firmware's most sensitive code and is generally inaccessible to the operating system, making it a prime target for sophisticated attacks.
Jensen's analysis revealed that an attacker could manipulate this vulnerability to write malicious code to the motherboard's firmware, establishing persistence that could survive operating system reinstalls and even BIOS updates. The implications of this are significant, as malicious code executing in SMM could have full control over the system, with the ability to intercept and modify the operating system's boot process, disable security features, or inject code into other processes.
Impact
MSI has confirmed that this vulnerability impacts a wide array of their products. The affected models include those using the following chipsets:
- Intel 300, 400, 500, 600, and 700 series
- AMD AM4 and AM5 platforms
As of the latest update, MSI has released beta BIOS updates to address this vulnerability for most of the affected chipsets:
- Complete fixes are available for Intel 300, 400, 500, AMD 300, 400, and 500 series chipsets.
- Fixes for Intel 600 and 700 series, as well as AMD 600 series, are still in progress.
Users of affected motherboards are strongly advised to update their BIOS as soon as possible. However, MSI has noted that even with these updates, there could be a delay in distribution as OEMs need time to integrate these updates into their release channels. In the meantime, users should ensure that they download BIOS updates only from trusted sources to avoid further security risks.
Proof of concept exploit out
Jensen has also published a proof-of-concept (PoC) exploit on GitHub, demonstrating the vulnerability's exploitability. The PoC highlights the potential dangers of this flaw, especially in scenarios where an attacker could gain physical or remote access to a system.
To mitigate the risks associated with CVE-2024-36877, users are advised to take the following actions:
- Apply the latest BIOS updates provided by MSI once available for your specific motherboard model.
- Ensure BIOS updates are downloaded only from MSI's official website or other verified sources.
- Stay informed on the availability of finalized BIOS updates, particularly if using Intel 600, 700 series, or AMD 600 series motherboards.







Leave a Reply