
In a detailed analysis by Fortinet's FortiGuard Labs, researchers have uncovered a malware dissemination method involving a crafted Minecraft source pack.
The malware, known as the zEus stealer, is specifically targeted at Microsoft Windows users, posing a high threat level by potentially enabling future attacks through the stolen information.
zEus stealer has been cleverly concealed within a Minecraft source pack distributed through YouTube, exploiting the game's customization features that typically enhance user experience. The particular variant leverages a WinRAR self-extracting file disguised as a Windows screensaver file, deceiving users into executing the malicious payload.
Once activated, the zEus stealer initiates by checking for any ongoing analysis attempts, evading detection by scrutinizing the computer's name and running processes against a predefined blacklist of analysis tools and environments.
If the environment is deemed safe, it proceeds to harvest a variety of sensitive data, including IP addresses, hardware details, and browser information from multiple popular web browsers like Chrome and Firefox.
Fortinet
Data theft operations
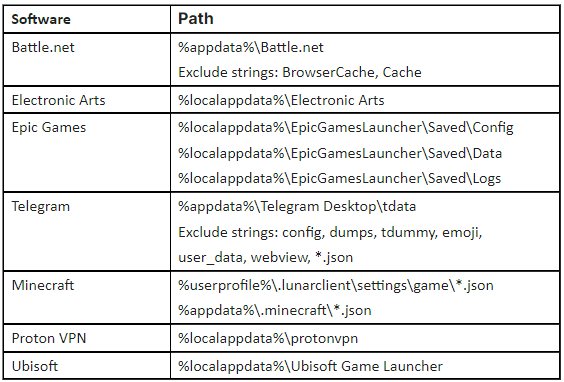
The malware organizes the stolen data into several folders, each designated for specific types of information such as browser cookies, hardware specifications, and even gaming software details from platforms like Minecraft, Steam, and Discord. zEus attempts to pilfer backup codes from Discord, crucial for account recovery, indicating a sophisticated approach to bypass multi-factor authentication.
Fortinet
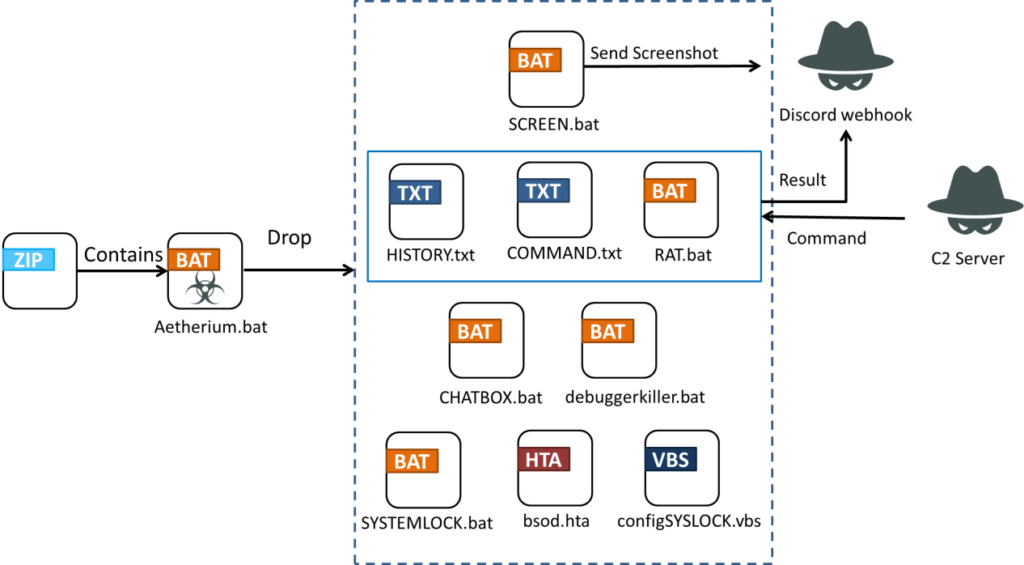
The persistence of the malware is ensured by auto-run entries in the Windows registry, which execute several scripts dropped by the stealer, including those that disable task manager functionalities and monitor the system through continuous screenshot captures.
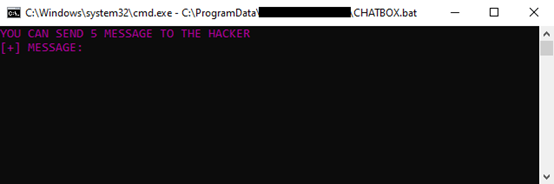
Control over the infected system is maintained through a command-and-control (C2) script named RAT.bat, which retrieves commands from a remote server and executes them. The malware also facilitates direct communication with the attacker through a simple chat box system, allowing the victim to send messages of up to five sentences to the attacker, a very uncommon malware feature.
To combat threats like zEus, the use of multi-factor authentication (MFA), which adds an additional layer of security even if the primary password is compromised, is crucial. Users are advised to download files exclusively from reputable sources and to remain vigilant about the authenticity of the file sources. That is especially the case when downloading custom-crafted game mods and Minecraft files.







Leave a Reply