
Trend Micro exposed a social engineering attack that leveraged a Microsoft Teams call to deploy DarkGate malware. The attackers manipulated a user into installing a remote access tool, AnyDesk, to infiltrate the system, execute malicious commands, and attempt to establish a command-and-control (C&C) connection. While the attack was thwarted before data exfiltration occurred, the incident highlights the evolving threat of vishing (voice phishing) techniques.
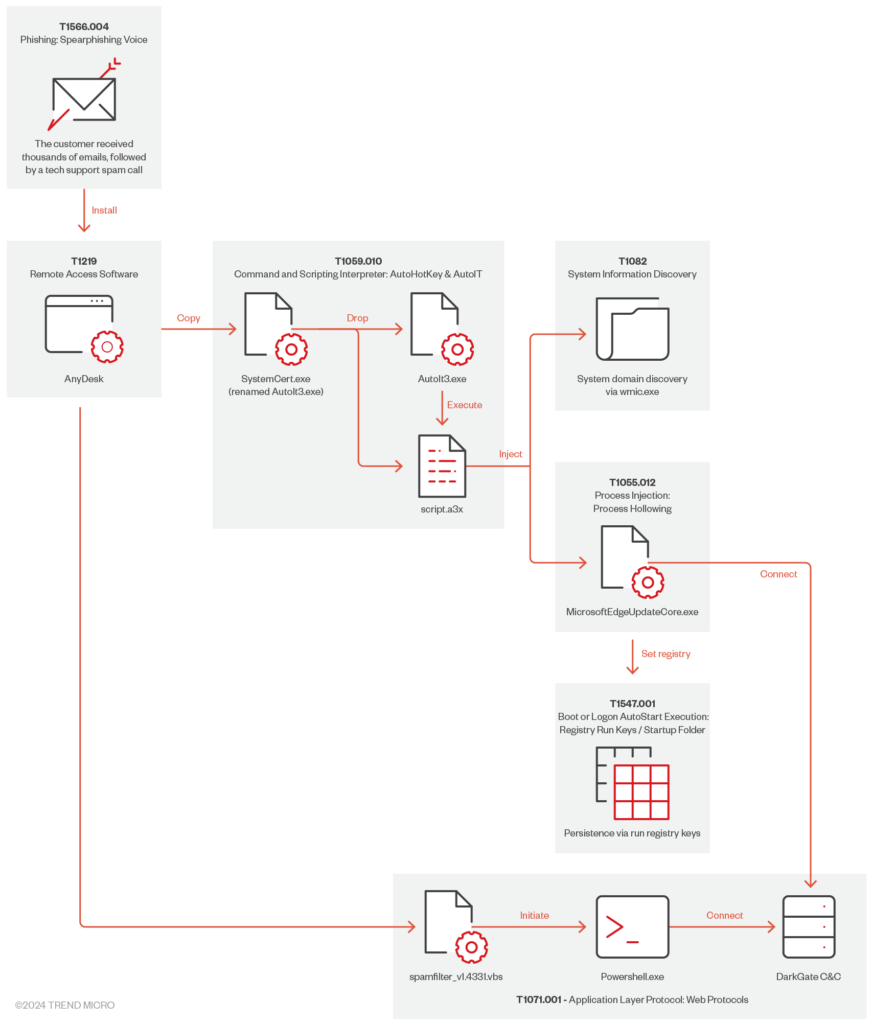
The attack began with the victim receiving an email flood followed by a Microsoft Teams call from an individual impersonating an employee of a trusted supplier. During the call, the attacker instructed the victim to download Microsoft Remote Support software. When installation failed, the victim was directed to download AnyDesk, a legitimate remote access application. Using social engineering, the attacker obtained the user’s credentials to gain access.
Once connected, the attacker dropped multiple suspicious files, including a DLL file, SafeStore.dll, executed via rundll32.exe. This DLL employed side-loading techniques to trigger additional malicious activities. DarkGate malware, packaged in an AutoIt script, was subsequently deployed, enabling system reconnaissance and connection to a C&C server.
Deploying DarkGate via Teams
DarkGate malware was delivered through an intricate chain of events involving the execution of the encrypted AutoIt script, script.a3x, and its integration with legitimate system processes like MicrosoftEdgeUpdateCore.exe. These steps allowed the malware to operate covertly and evade detection. Key commands executed by the malware included:
- Collecting system information (cmd /c systeminfo).
- Gathering network details (cmd /c ipconfig /all).
- Creating persistent registry entries to maintain access.
The malware also attempted to identify and bypass antivirus software by creating decoy files and running duplicate instances of itself. During this phase, connections to a C&C server at 179.60.149[.]194 were observed.
Trend Micro
Implications and defense tips
DarkGate malware is a potent tool capable of enabling remote control, system discovery, data collection, and further payload delivery. Its use in this attack underscores the growing sophistication of threat actors employing voice phishing to bypass traditional email-based defenses.
The malware family is broadly distributed via ‘ClickFix’ campaigns, SEO poisoning, and even Excel Files in SMB shares. Most likely, this latest vishing campaign is a distribution method chosen by an operator renting the malware tool to target corporate environments.
To avoid infections by powerful info-stealers, always verify the identity of technical support personnel or vendors before granting remote access. Organizations should establish protocols to validate third-party support claims and enforce multi-factor authentication on all remote access platforms.







Leave a Reply