
Microsoft has uncovered an extensive spear-phishing campaign by the Russian-backed hacking group known as Midnight Blizzard, which aims to gather intelligence by exploiting Remote Desktop Protocol (RDP) files in phishing emails. The attack targets key sectors worldwide, including government, defense, academic, and non-governmental organizations.
According to Microsoft Threat Intelligence, the Midnight Blizzard campaign began on October 22, 2024, and continues to impact targeted users in the United Kingdom, Europe, Australia, and Japan. This campaign marks a shift in Midnight Blizzard’s approach, introducing the use of signed RDP configuration files embedded within phishing emails, a method allowing attackers to control targeted systems and harvest sensitive data.
Midnight Blizzard, known also as APT29 or “Cozy Bear,” is attributed to Russia’s Foreign Intelligence Service (SVR) and has a track record of intelligence collection dating back to 2018. Its targets primarily include government entities, NGOs, and IT providers, with operations centered in the U.S. and Europe.
Midnight Blizzard has previously utilized various tactics, including credential theft, lateral movement in cloud environments, and supply chain compromises to infiltrate its targets. Notably, the group has employed sophisticated malware such as FOGGYWEB and MAGICWEB to infiltrate Active Directory Federation Services (AD FS) environments, achieving stealthy, long-term access to sensitive data.
Overview of attack methods
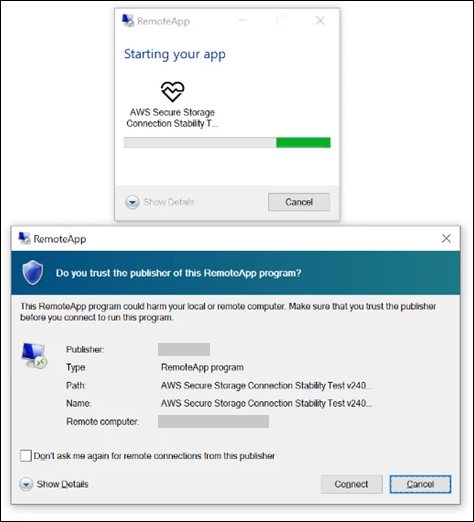
The spear-phishing emails used in this campaign are highly targeted, leveraging impersonation tactics by referencing reputable companies like Microsoft and AWS. Embedded within these emails, a signed RDP configuration file prompts recipients to initiate a remote connection, thereby granting the attackers access to various system resources.
Microsoft revealed that once the target opens this malicious RDP file, a connection to a Midnight Blizzard-controlled server is established, allowing for direct access to:
- Files and directories
- Connected network drives and peripherals (e.g., smart cards, printers)
- Clipboard data and authentication mechanisms like Windows Hello and security keys
Through these connections, the attackers can deploy additional malware, such as Remote Access Trojans (RATs), to maintain prolonged access to the infected device and network. Microsoft’s analysis indicates that resources and credentials from the compromised systems could be exposed to the attacker, potentially allowing broader organizational infiltration.
Microsoft
IoCs and response
Microsoft has shared key IoCs related to this campaign, detailing domains and IP addresses linked to the attacker-controlled servers. Targeted domains include compromised organizations across sectors, and the .RDP filenames used in phishing emails, such as “AWS IAM Compliance Check.rdp” and “Zero Trust Architecture Configuration.rdp,” are part of the group’s lure for tech-savvy targets.
To defend against this threat, Microsoft recommends that users restrict outbound RDP connections using Windows Firewall, enforce multi-factor authentication (MFA) with phishing-resistant methods like FIDO tokens, and enable tamper protection, network protection, and web protection within Microsoft Defender for Endpoint.






Leave a Reply