
Microsoft has issued a warning about a surge in cyberattacks leveraging Node.js to deliver malware and steal sensitive information.
Since October 2024, its Defender Experts team has observed multiple campaigns using Node.js in novel ways to evade detection and persist in compromised environments.
The findings come from a detailed analysis by Microsoft's Defender for Endpoint and Defender XDR teams, who uncovered multiple attack chains using Node.js as a runtime environment or for inline script execution. These tactics were found in malvertising campaigns targeting users with cryptocurrency-themed lures, as well as in phishing-based social engineering schemes.
Node.js introducing malware
Node.js, an open-source JavaScript runtime widely used by developers for server-side and desktop applications, allows code to be executed outside a browser. Its legitimate use in development environments makes it an ideal tool for attackers seeking to blend in, especially in organizations with developer activity. By packaging malware into compiled JavaScript files and executing scripts directly with node.exe, attackers bypass conventional security mechanisms that typically flag suspicious scripts or executables.
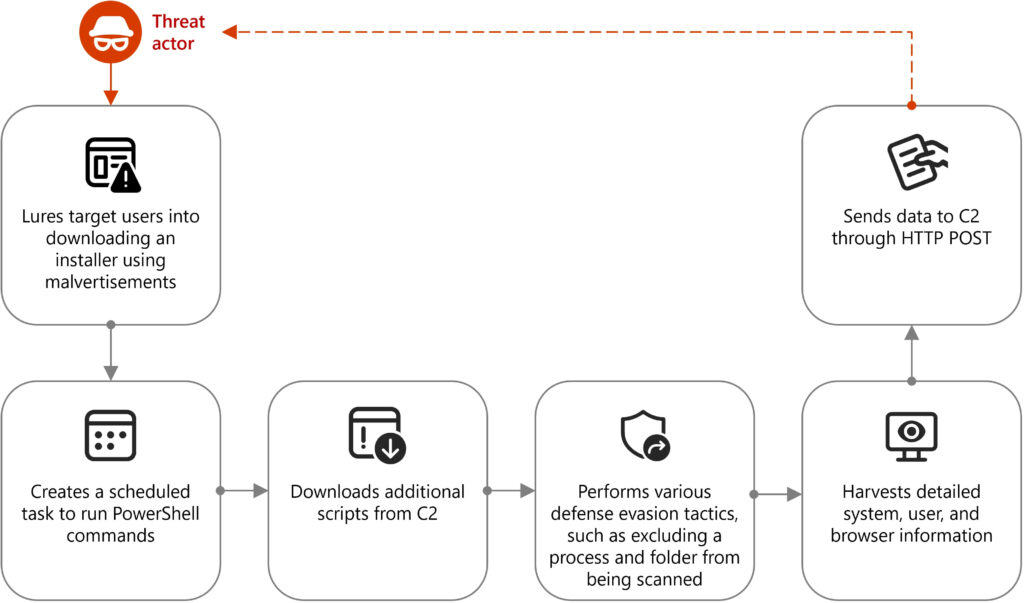
One active campaign, detailed in Microsoft's report, uses malvertising to lure users to fraudulent websites imitating cryptocurrency trading platforms like Binance or TradingView. Visitors are prompted to download a malicious installer crafted using Wix, which embeds a custom DLL (CustomActions.dll). Upon execution, this DLL gathers system data via Windows Management Instrumentation (WMI) and sets a scheduled task to run obfuscated PowerShell commands.
These PowerShell tasks modify Microsoft Defender for Endpoint settings, excluding specific processes and folders from scans to evade detection. The script then downloads further payloads from command-and-control (C2) servers, collecting extensive system metadata — ranging from BIOS and OS details to network adapters and user information — and exfiltrating it via HTTP POST requests.
The attack chain continues with a second-stage payload that includes a Node.js runtime (node.exe), a compiled JavaScript file (JSC), and additional libraries. Once executed, the JSC script initiates follow-on actions such as network connections, credential theft, certificate manipulation, and browser data extraction — suggesting multi-stage attack potential and long-term persistence goals.
Microsoft
Microsoft also identified a separate technique using inline script execution in Node.js. In this scenario, seen in a phishing campaign of the “ClickFix” type, a malicious PowerShell command installs Node.js and its modules, then runs JavaScript directly from the command line. The script performs domain reconnaissance, disguises C2 traffic as Cloudflare activity, and establishes persistence by altering registry run keys.
Catching malicious activity early
To defend against these evolving threats, Microsoft recommends a combination of technical controls and user education. Organizations are urged to:
- Monitor Node.js usage and set alerts for the unauthorized execution of node.exe.
- Enhance PowerShell logging, and enable script blocks, module, and transcription logging to uncover obfuscated scripts.
- Restrict software sources only to official and verified sites.
- Implement firewall rules to block outbound traffic to suspicious or unknown domains. Use EDR/XDR solutions in block mode to catch post-breach activity.
Additionally, Microsoft advises enabling tamper protection, turning on cloud-delivered antivirus defenses, and enforcing script execution policies where possible. Attack surface reduction rules in Microsoft Defender XDR can also help block the execution of suspicious files and scripts before they run.







Leave a Reply