
Microsoft's July 2024 Patch Tuesday update addresses 142 vulnerabilities on Windows, including two actively exploited zero-day flaws in Hyper-V and the MSHTML platform.
The two actively exploited zero-day vulnerabilities, CVE-2024-38080 and CVE-2024-38112, are particularly noteworthy. CVE-2024-38080 is a Windows Hyper-V Elevation of Privilege Vulnerability, allowing authenticated attackers to execute code with SYSTEM privileges. Exploitation of this flaw can lead to severe consequences, especially if utilized in ransomware attacks. Microsoft did not specify the extent of its exploitation, but given the potential impact, it is crucial for organizations using Hyper-V to deploy the update promptly.
CVE-2024-38112, a Windows MSHTML Platform Spoofing Vulnerability, was reported by Check Point Research. This vulnerability involves malicious .url files exploiting the outdated Internet Explorer to execute attacker-controlled URLs. Despite being retired, IE can still be called upon using specific tricks, such as the “mhtml” technique seen in this exploit. This trick deceives users into believing they are opening a PDF file, while in reality, they are executing a harmful .hta application. This vulnerability has been actively exploited in the wild, with attacks dating back to January 2023.
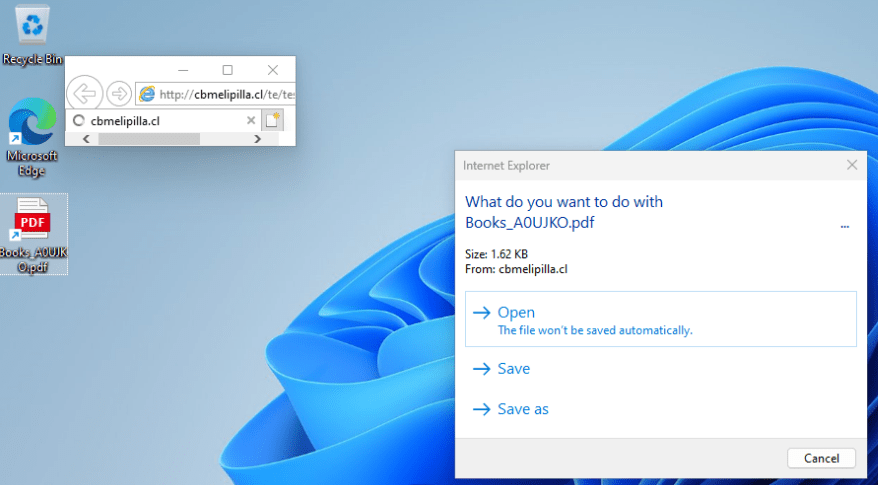
Check Point Research
Microsoft's July update also includes fixes for two other zero-day vulnerabilities, CVE-2024-35264 and CVE-2024-37985. The former is a .NET and Visual Studio Remote Code Execution Vulnerability caused by a race condition in processing HTTP/3 streams. The latter, disclosed by Arm, involves a side-channel attack known as “FetchBench,” which can steal sensitive information from heap memory.
Microsoft's extensive Patch Tuesday update covers a wide array of products, including Windows, Office, .NET, Visual Studio, and even Xbox. Of the 142 vulnerabilities, five are rated critical, 133 important, and three moderate. Notably, 59 of these are remote code execution vulnerabilities, highlighting the significant security risks addressed this month.
For organizations and individuals, it is imperative to apply these updates without delay. To do that, open Windows Settings, select Windows Update and click on the ‘Download & install’ button for the process to start. After the latest security updates are downloaded and installed on your system, a restart will be required to finalize their application.
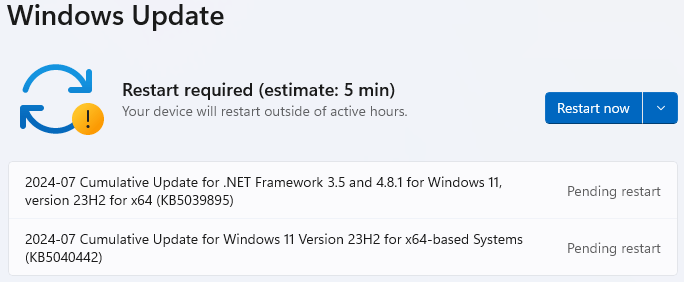
For known issues about this update, check out the release announcement on Microsoft’s support portal.
The actively exploited zero-day vulnerabilities, particularly in Hyper-V and MSHTML, pose substantial risks that could lead to severe security breaches. Users should also remain vigilant about .url files from untrusted sources, as these can be used to execute damaging attacks on their systems.







Leave a Reply