
A critical vulnerability (CVE-2024-20017) affecting MediaTek chipsets widely used in Wi-Fi 6 (802.11ax) devices has gained heightened attention following the publication of a proof-of-concept (PoC) exploit. The flaw, which received a CVSS score of 9.8, poses a severe security risk by allowing remote code execution (RCE) without any user interaction. The PoC was released by security researcher ‘Hyprdude,’ showcasing how attackers can exploit the vulnerability to take full control of affected devices.
The vulnerability originates in the wappd network daemon, part of MediaTek’s MT7622/MT7915 SDK, which handles wireless interface and access point management. It affects a range of chipsets, including MT6890, MT7915, MT7916, MT7981, MT7986, and MT7622, which are commonly found in devices from leading brands like Ubiquiti, Xiaomi, and Netgear. As a result, millions of embedded devices, including routers and access points, are potentially at risk.
At the core of the issue is a buffer overflow in the IAPP_RcvHandlerSSB() function of the wappd service, which improperly processes incoming network data. The lack of adequate input validation allows attackers to send malicious packets that overflow a stack buffer, leading to an out-of-bounds write. This vulnerability can be exploited to execute arbitrary code on the device by overwriting critical memory areas, enabling an attacker to take full control.
The PoC highlights several attack vectors, including:
- RIP hijacking via return address corruption, leading to system command execution.
- Arbitrary write by exploiting pointer corruption, which can be used to manipulate key parts of the system’s memory.
- Kernel exploitation by chaining multiple flaws, including issuing ioctl commands for deeper system control.
blog.coffinsec.com
Scope of impact
The vulnerability impacts MediaTek’s SDK versions 7.4.0.1 and earlier, as well as popular platforms such as OpenWrt 19.07 and 21.02. This means that a wide variety of consumer and enterprise devices are exposed, particularly those that use these chipsets for Wi-Fi connectivity, such as routers, IoT devices, and smartphones.
This vulnerability is particularly dangerous because it is zero-click, meaning that no user interaction is required for exploitation. Given the widespread use of these chipsets in critical infrastructure, such as home and business networking equipment, the potential impact is vast, making immediate action crucial for all users.
Exploit now public
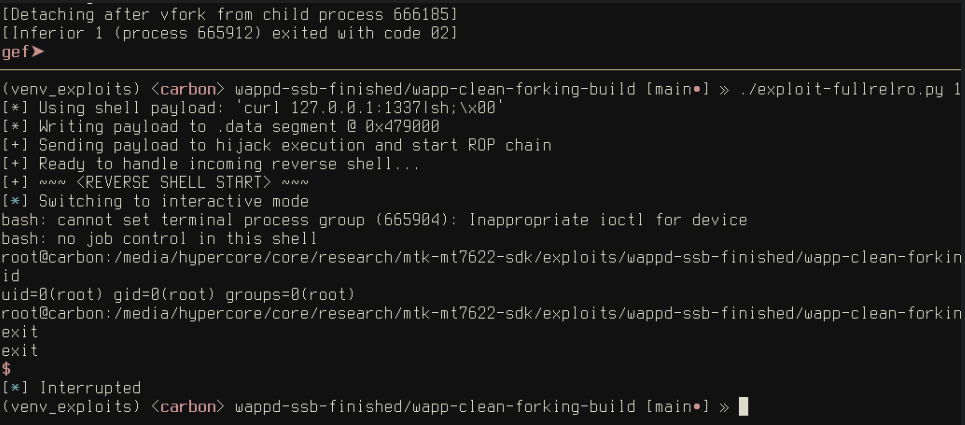
The PoC, made available on GitHub, showcases various exploitation methods. These range from simple stack overflows to complex return-oriented programming (ROP) and jump-oriented programming (JOP) techniques. The exploit code can work on different platforms, including both x86_64 and aarch64 architectures, covering a wide array of devices.
The published exploit demonstrates how attackers can leverage the vulnerability to bypass common mitigation techniques like ASLR (Address Space Layout Randomization) and stack canaries, which are designed to prevent such attacks. With these defenses disabled or bypassed, attackers can redirect execution flow to their controlled code.
Mitigation advice
MediaTek patched the flaw in March 2024, urging users and manufacturers to update to the latest firmware versions that include the fix. However, due to the complexity in the software supply chain and testing required downstream, it may take a while before the patch reaches impacted consumers.
The general recommendations are the following:
- Ensure that devices are running patched versions of the firmware, particularly for MediaTek SDK versions 7.4.0.1 and earlier.
- Device manufacturers, such as Ubiquiti, Xiaomi, and Netgear, have likely released their own updates addressing this issue. Users should verify with their vendors and apply these patches as soon as possible.
- Enterprises should audit their networks for any exposed devices using vulnerable chipsets and ensure proper network segmentation to reduce the risk of remote exploitation.







Leave a Reply