In a significant cyber incident, over 600,000 small office/home office (SOHO) routers from a single internet service provider (ISP) in the U.S. were taken offline between October 25 and 27, 2023.
This destructive event, discovered by Lumen Technologies' Black Lotus Labs, left the affected devices permanently inoperable, necessitating hardware replacements.
Attack details
The culprit behind this widespread disruption was identified as the Chalubo remote access trojan (RAT), a commodity malware first observed in 2018. Chalubo's advanced obfuscation techniques, including in-memory execution, random process naming, and encrypted communications with command and control (C2) servers, have contributed to its elusiveness.
Despite being a well-known RAT, Chalubo's deployment in this attack appears to have been strategic, aiming to obscure attribution by using a widely recognized malware family rather than a custom toolkit.
The attack's impact was confined to a single autonomous system number (ASN) belonging to the targeted ISP, resulting in a 49% reduction in the number of modems online. Public scan data confirmed the disappearance of nearly half a million devices, predominantly ActionTec and Sagemcom models. This led Black Lotus Labs to suspect a malicious firmware update, given the devices displayed symptoms that a factory reset could not resolve.
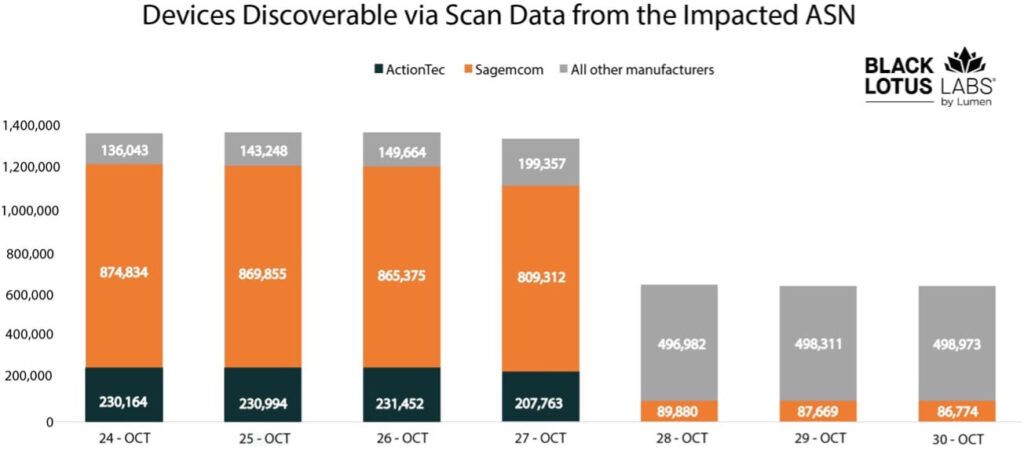
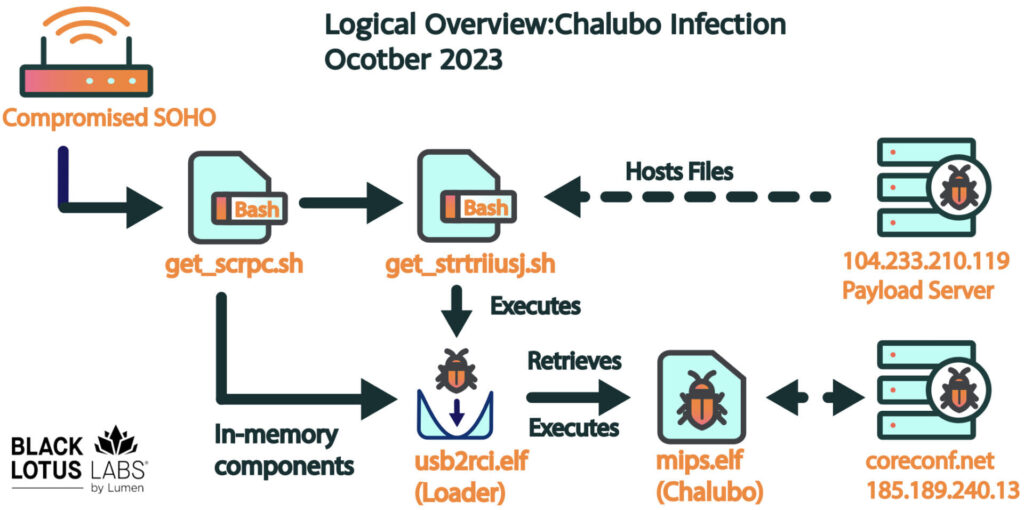
The infection process was initiated through the exploitation of weak credentials or exposed administrative interfaces, as no specific exploits for the affected models were listed in OpenCVE. The attack began with a bash script called “get_scrpc,” which facilitated the download and execution of the Chalubo binary.
Once installed, Chalubo conducted a series of actions to evade detection, including deleting itself from the disk, renaming processes, and using ChaCha20 encryption for C2 communications. The malware also had built-in functionality to execute Lua scripts, likely used by the attackers to deliver the destructive payload.
Mapping Chalubo
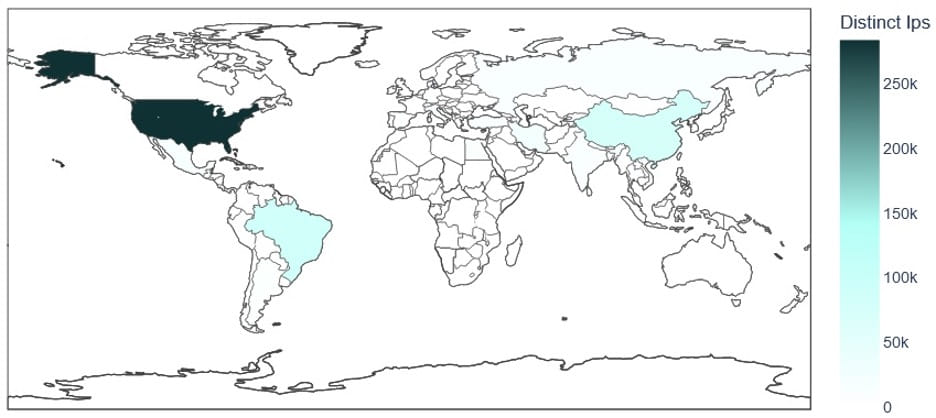
Lumen's telemetry indicated that Chalubo was highly active from November 2023 to early 2024, with over 330,000 unique IP addresses interacting with multiple C2 nodes. Despite the scale of the infection, Black Lotus Labs did not find evidence linking this activity to any known nation-state actors. The attack's deliberate and targeted nature, particularly affecting rural and underserved communities, raises concerns about the potential impact on critical services like emergency communications and telehealth.
Black Lotus Labs' detailed investigation, utilizing global telemetry and internet scan data, confirmed the widespread presence of the Chalubo malware, with a focus on U.S. based systems.
Organizations are advised to secure management interfaces, change default passwords, and ensure devices are regularly updated. For consumers, regular router reboots and timely installation of security patches are recommended practices.







Leave a Reply