
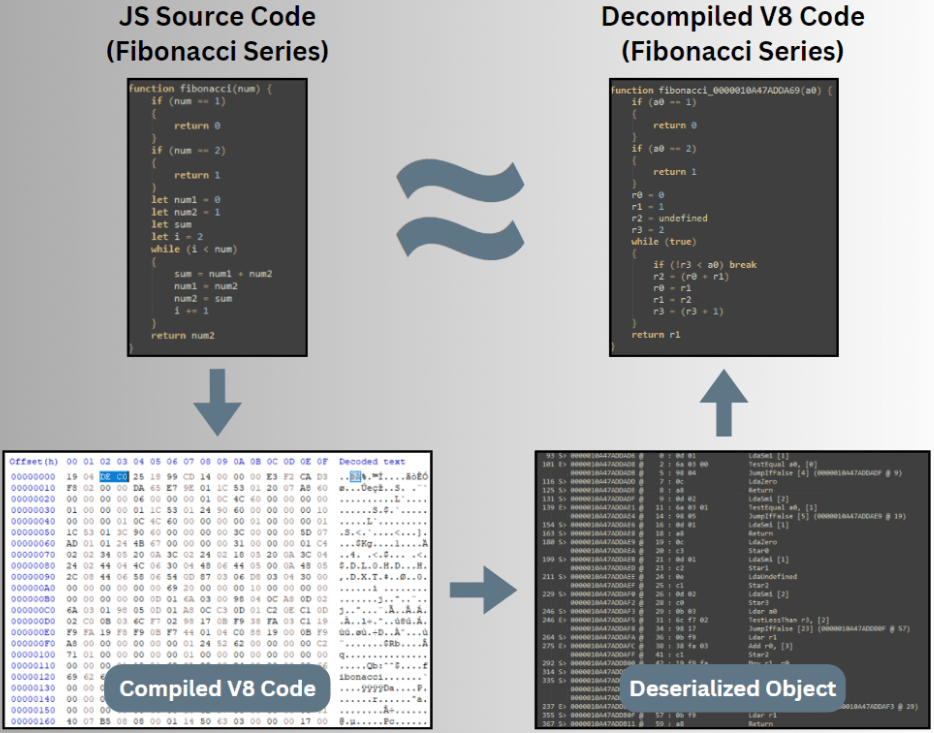
Researchers at Check Point Research (CPR) have uncovered a new trend in malware development: the use of compiled V8 JavaScript to evade detection. Utilizing a custom-built tool named View8, CPR decompiled thousands of malicious V8 applications, revealing a diverse array of malware exploiting this technique, including Remote Access Tools (RATs), stealers, miners, and even ransomware.
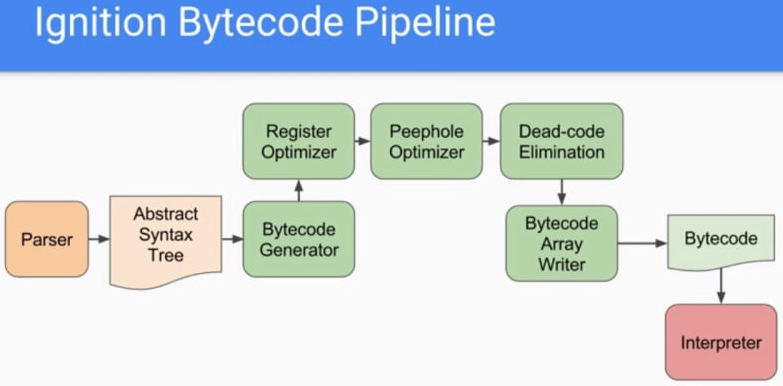
Moshe Marelus from CPR spearheaded the investigation into compiled V8 JavaScript, a feature of Google’s V8 engine that compiles JavaScript into low-level bytecode. This method effectively hides the original source code, making static analysis challenging. In response, CPR developed View8, a Python-based tool that decompiles V8 bytecode into a readable high-level language similar to JavaScript. This tool enabled the team to analyze thousands of malicious samples that had previously gone undetected by most security vendors.
Check Point Research
V8, an open-source JavaScript engine developed by Google, is integral to Chrome and Node.js. It converts JavaScript into bytecode, which boosts performance but also serves as a method for attackers to obscure their code. By using tools like Node.js’s vm module and bytenode, attackers compile JavaScript into bytecode, hiding their malicious activities. This bytecode runs only on the specific V8 version it was compiled for, requiring attackers to ensure compatibility for successful execution.
Check Point Research
Notable malware examples
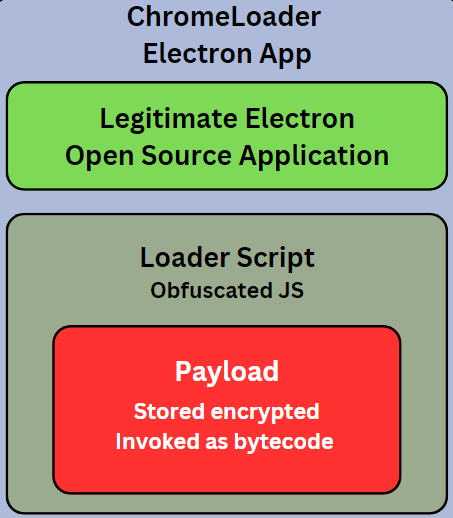
ChromeLoader:
First identified in early 2022, ChromeLoader hijacks browsers, steals information, and deploys additional malware. Recent variants use the Electron framework to embed malicious scripts in legitimate applications like FLB-Music-Player and PDF-Viewer. These scripts are heavily obfuscated, decrypting and executing bytecode payloads that were previously undetectable without View8. CPR’s analysis revealed ChromeLoader’s configurations, including command-and-control (C&C) domains and encryption methods.
Check Point Research
Ransomware and Wipers:
Among the analyzed files, CPR identified ransomware strains that encrypt files and send victim information via Discord webhooks. Despite successful encryption, these samples showed very low detection rates on VirusTotal. Additionally, a type of wiper malware was discovered that overwrites files with random strings, using the same obfuscation techniques.
Shellcode Loader:
A sophisticated shellcode loader malware was also identified. This malware fetches and executes x64 shellcodes from a remote C&C server using ffi-napi and ref-napi modules. The loader, based on a GitHub repository called ‘node-shellcode,’ demonstrates the increasing use of legitimate open-source tools in malware development.
Conclusion
The use of compiled V8 JavaScript offers significant benefits to cybercriminals, primarily due to its ability to evade traditional static detection methods. By compiling JavaScript into bytecode, attackers can obscure their malicious code, making it nearly impossible for security tools to analyze and detect threats without specialized decompilation techniques like those provided by View8.
This trend is particularly worrying because it leverages common and legitimate technologies, allowing malware to blend in with benign applications and bypass defenses that rely on code visibility. The low detection rates and increased use of sophisticated obfuscation methods pose a substantial challenge to cybersecurity, necessitating advanced tools and continuous vigilance to protect against these evolving threats.







Leave a Reply