
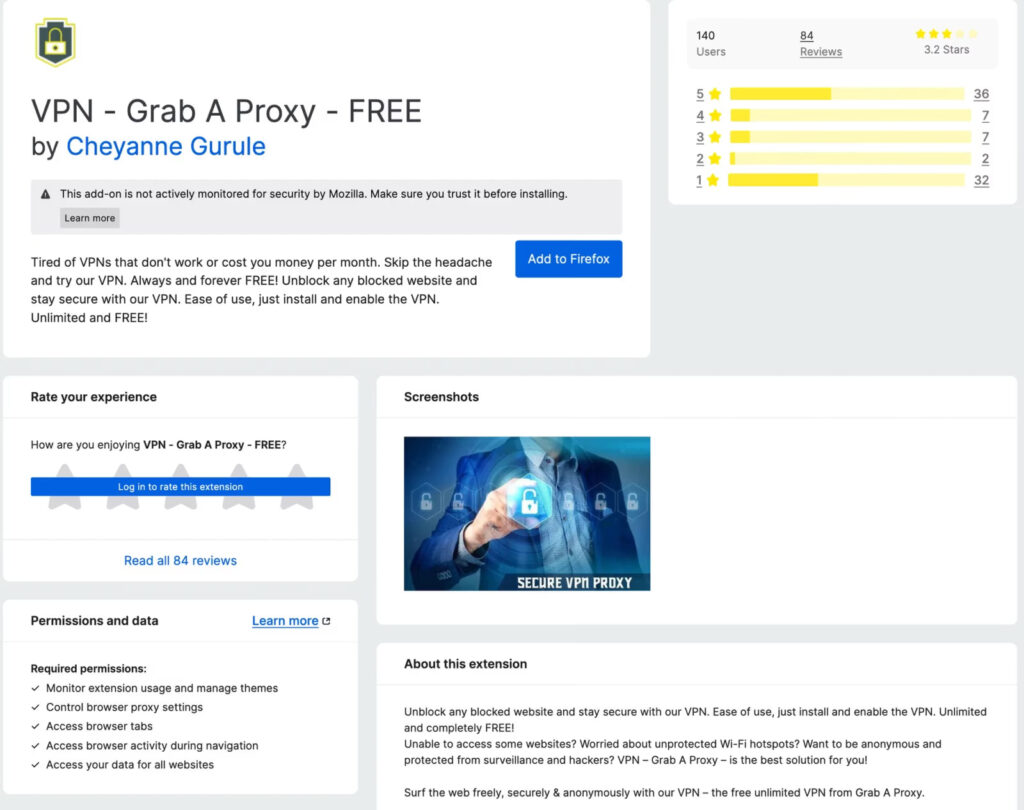
A new wave of malicious Firefox extensions has been uncovered, with the most alarming among them posing as a privacy-focused VPN while secretly hijacking all user traffic and injecting invisible trackers.
The spyware-laced extension, VPN Grab A Proxy Free, is part of a set of eight malicious add-ons recently identified by Socket's Threat Research Team, who warn that these tools abuse browser permissions to compromise user privacy at scale.
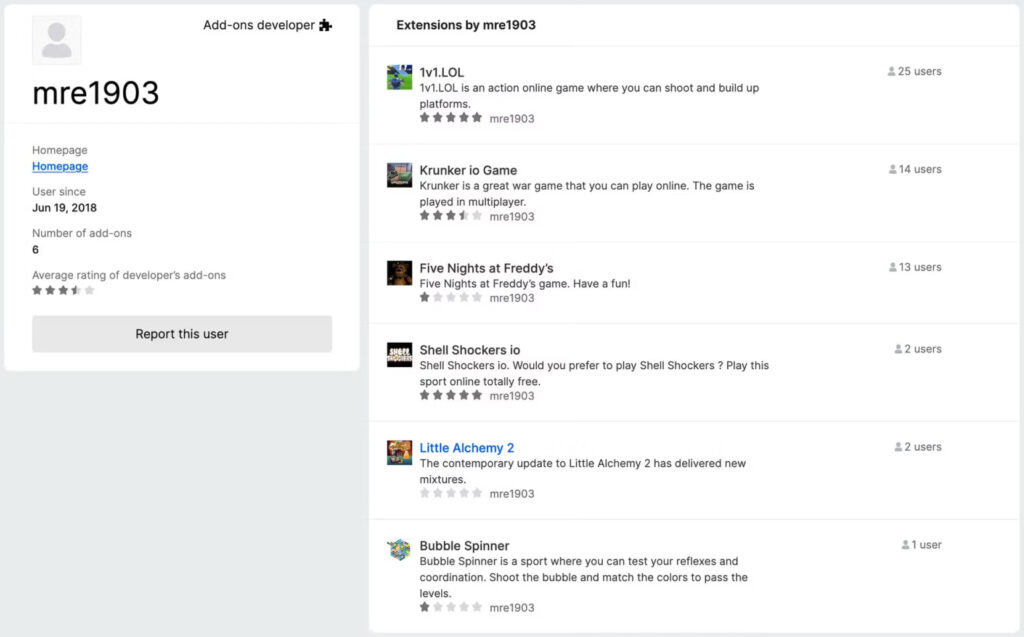
Socket discovered the extensions during a follow-up to an earlier investigation into Shell Shockers, a fake gaming extension that redirected users to tech support scams. This expanded inquiry exposed a wider ecosystem of malicious Firefox extensions, some operated by a persistent threat actor known as mre1903, while others appear to be opportunistic one-offs engaging in affiliate fraud and credential theft.
Grab A Proxy Spy
VPN Grab A Proxy Free is marketed as a free VPN for secure browsing, but the extension actually does the opposite: it covertly routes all browser traffic through an attacker-controlled proxy and injects invisible iframes for user tracking.
Socket
Specifically, the extension uses chrome.proxy.settings.set() to direct traffic through grabaproxy[.]com on port 8080. At the same time, it silently appends hidden iframes (<iframe>) with user identifiers to every loaded page. These iframes are styled with zero opacity and placed behind all visible content using a negative z-index, ensuring users remain unaware of their presence. This setup enables full surveillance of user activity, including intercepting credentials, private messages, financial information, and browsing behavior.
Worse still, by forcing HTTP proxies for all traffic, the extension downgrades secure HTTPS connections, effectively enabling man-in-the-middle attacks. This makes it trivial for the extension operator to intercept or manipulate encrypted data streams.
Malicious Firefox extensions
The VPN extension is just one among a broader group of eight malicious add-ons found by Socket. These include:
- CalSyncMaster – a malicious calendar sync tool that steals OAuth tokens by exploiting Google's web authentication flow. It targets users' calendar data, enabling persistent access to sensitive business and personal information.
- GimmeGimme – a fraudulent shopping assistant that hijacks user sessions on popular Dutch and Belgian e-commerce sites like bol.com and coolblue.nl. The extension secretly redirects clicks through affiliate links to siphon commissions, undermining legitimate rewards programs.
- A cluster of fake gaming extensions, attributed to the long-active threat actor mre1903, which masquerade as popular titles like Little Alchemy 2, 1v1.LOL, Krunker.io, Five Nights at Freddy's, and Bubble Spinner. None of these provide actual game functionality — instead, they redirect users to scam pages, including gambling sites and fake Apple virus warnings featuring scareware codes like “0x800VDS”.
These extensions abuse browser APIs like chrome.windows.create() to launch pop-up windows on install, catching users off guard and making them more susceptible to scam tactics.
Firefox, developed by Mozilla, is a widely used open-source web browser favored by many in the privacy-conscious community. While Mozilla curates its extension store and performs checks, the discovery of these malicious add-ons shows that threat actors can still slip through its defenses.
Notably, mre1903, the threat actor behind several of the gaming extensions, has been active since at least 2018, with malicious submissions dating back to late 2020. This suggests a long-running campaign that's evolved in sophistication over time, now operating across multiple domains and possibly multiple browsers.
Socket
To reduce exposure to malicious browser extension risks, be wary of extensions that demand broad access to data, remove those that request permissions unrelated to their advertised purpose, and monitor for unauthorized proxy settings or unexplained web traffic patterns after installing new extensions.







Leave a Reply