
A critical account takeover vulnerability in the LiteSpeed Cache plugin, affecting over 6 million WordPress sites, was patched yesterday with the release of version 6.5.0.1. The vulnerability allows unauthenticated users to take over logged-in accounts, including those with administrator privileges, by exploiting a debug log flaw.
Security researcher Rafie Muhammad from Patchstack uncovered the issue during an analysis of a previously discovered vulnerability. The flaw originates in the plugin’s debug log feature, where sensitive data, including authentication cookies, could be leaked. Specifically, the vulnerability stemmed from the HTTP response headers in a file related to LiteSpeed Cache’s debugging feature, exposing the “Set-Cookie” header that contains session data used for user authentication.
The LiteSpeed Cache plugin, known for accelerating WordPress websites through server-level caching, is widely used across the WordPress ecosystem, including in popular plugins like WooCommerce, bbPress, and Yoast SEO. Given its reach, the vulnerability posed a significant risk, potentially allowing attackers to install malicious plugins or take other destructive actions by impersonating site administrators.
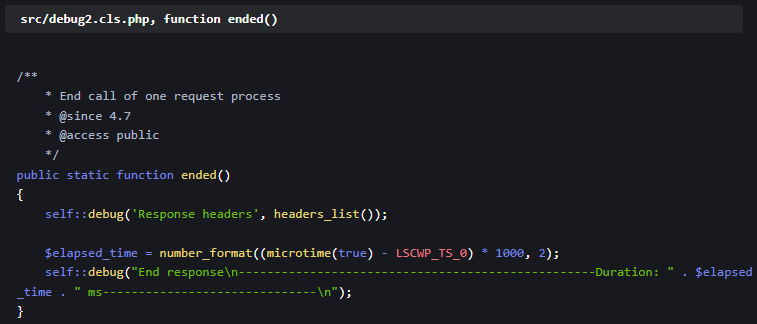
The vulnerability, tracked under CVE-2024-44000, was linked to the “ended” function in the src/debug2.cls.php file, which logs HTTP response headers, inadvertently including cookies. This allowed attackers to gain access to session information, putting entire websites at risk.
Patchstack
The vulnerability discovery timeline began on August 22, 2024, with LiteSpeed eventually releasing the patch on September 4, with version 6.5.0.1, which incorporates the following key changes:
- The debug log file was moved to a dedicated directory (/wp-content/litespeed/debug/) with randomized filenames.
- The “Log Cookies” option was dropped, preventing cookies from being stored in the log.
- Cookies were removed from response headers, reducing exposure to sensitive data.
- An additional security measure involved placing a dummy index.php file in the new directory to block unauthorized access.
Although these patches strengthen the plugin's security, experts recommend additional steps for users and developers. Site owners should immediately purge any old debug logs that may contain sensitive data, and apply .htaccess rules to block direct access to new log files. Additionally, developers are urged to avoid logging sensitive data like authentication cookies.
Continual source of risks
This isn't the first time LiteSpeed Cache has faced security challenges. In August 2024, a severe privilege escalation flaw (CVE-2024-28000) allowed attackers to gain administrator access by exploiting the plugin's user simulation feature, designed to pre-load cache files by mimicking logged-in users.
The vulnerability leveraged weak hash generation, which was predictable and easily brute-forced, allowing unauthorized access to critical WordPress functions, including setting the attacker as an administrator using the wp_set_current_user function. The patch for this issue (version 6.4) introduced stronger security checks, including the implementation of a more robust hash mechanism.
These vulnerabilities are part of a broader history of security incidents with LiteSpeed Cache. Earlier in 2024, WPScan reported active exploitation of older versions of the plugin, where attackers injected JavaScript malware into websites and created backdoor accounts such as “wpsupp-user.” These infections allowed attackers to embed malicious code into core WordPress files and databases, giving them complete control over affected sites.
Based on WordPress.org statistics, only 375,000 downloaded the plugin yesterday, when the patch was released. Assuming that all those downloads were for version 6.5.0.1, there still remain over 5.5 million sites open to attacks leveraging CVE-2024-44000.







Leave a Reply