
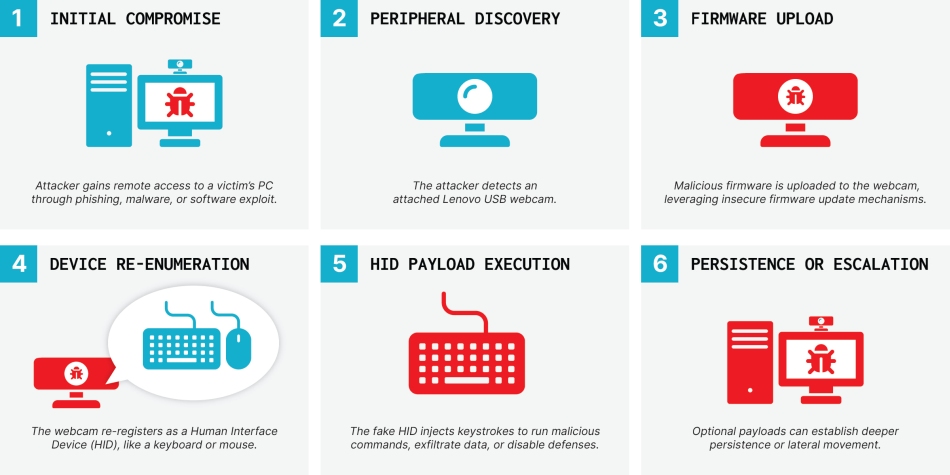
Eclypsium security researchers have demonstrated how certain Lenovo Linux USB webcams can be transformed into persistent “BadUSB” devices, capable of injecting keystrokes, delivering payloads, and surviving full system reinstalls.
The finding, presented at DEF CON 2025 by Jesse Michael and Mickey Shkatov, marks the first public case of attackers remotely weaponizing a peripheral already connected to a system.
The team focused on two Lenovo models, the 510 FHD Webcam and Performance FHD Webcam, both powered by SigmaStar SSC9351D ARM SoCs and running embedded Linux. Because the devices lack firmware signature verification, attackers with either physical access or prior remote compromise of the host can overwrite the camera firmware. Once modified, the camera can impersonate trusted USB devices such as keyboards (HID), enabling covert command execution and re-infection of hosts even after OS reinstalls.
Eclypsium
This attack builds on the “BadUSB” concept first unveiled in 2014 by Karsten Nohl and Jakob Lell, where modified firmware turns ordinary USB devices into stealth attack tools. Traditionally, this required introducing a malicious peripheral to the target system. Eclypsium’s work removes that barrier, turning existing, trusted devices into threats without unplugging or replacing them. The malicious firmware can persist across systems, meaning the weaponized webcam could spread to new hosts it connects to, potentially interacting with Wi-Fi or Bluetooth if supported by the hardware.
Eclypsium
Lenovo, a major PC manufacturer with a global presence, worked with SigmaStar to address the vulnerability following Eclypsium’s disclosure in March 2025. Firmware update tools with added signature validation were released on August 8, 2025, alongside security advisories. Users of the affected models can download updated firmware from Lenovo’s support site.
The root of the flaw lies in the ease of issuing firmware update commands over USB. Eclypsium found that simple SPI flash commands such as sf probe, sf erase, and sf write, could erase and rewrite the 8MB onboard firmware. Because the SigmaStar SoC runs a full Linux stack with USB Gadget support, the compromised webcam can emulate multiple device types, bypassing OS-level controls and evading endpoint detection tools.
While this research focused on two specific webcams, Eclypsium suspects other Linux-based USB peripherals may have similar weaknesses. Any device lacking firmware integrity checks could theoretically be repurposed for BadUSB-style attacks. The researchers warn that this shifts the USB security model, requiring defenders to consider attached devices as potentially hostile even if they originate from trusted vendors.
Users are recommended to take the following actions to mitigate the risk:
- Update affected Lenovo webcams to firmware version 4.8.0 via the official Lenovo support site.
- Limit USB port access where possible, especially in sensitive environments.
- Monitor for unusual USB device enumerations, particularly new HID devices appearing unexpectedly.
- Consider endpoint security tools capable of inspecting USB firmware integrity.







Leave a Reply