
A new phishing campaign linked to the CryptoChameleon group is targeting LastPass customers, cryptocurrency exchange users, and individuals using passkeys, with the goal of stealing master passwords and cryptocurrency holdings.
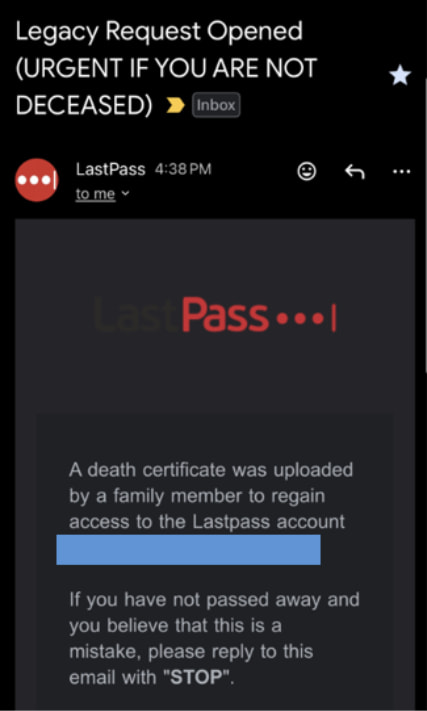
According to LastPass, the campaign began circulating in mid-October and uses spoofed emails that appear to originate from alerts@lastpass[.]com. The subject line, “Legacy Request Opened (URGENT IF YOU ARE NOT DECEASED),” attempts to alarm recipients into reacting quickly. The email falsely claims that a family member has submitted a death certificate to access the recipient’s LastPass vault and urges the user to “cancel the request” by clicking a malicious link.
LastPass
Victims who follow the link are taken to a phishing site hosted at lastpassrecovery[.]com, where they are prompted to enter their LastPass master password. Adding to the deception, the email includes fabricated case information, such as an agent ID, case status, and priority, and even advises users to confirm the sender’s email address, a method designed to reinforce the legitimacy of the spoofed message.
In a more aggressive twist, threat actors have also been calling victims directly, posing as LastPass representatives to further pressure them into entering their credentials on the fake recovery site.
LastPass is a password management service that stores encrypted credentials in the cloud, enabling users to generate, manage, and autofill secure passwords across devices. The platform has millions of users, including individuals and businesses.
Google Threat Intelligence has attributed this attack to CryptoChameleon (aka UNC5356), a financially motivated group previously linked to phishing campaigns targeting cryptocurrency users and exchanges. Notably, CryptoChameleon leveraged LastPass branding in earlier phishing kits observed in April 2024.
The group is known for deploying elaborate phishing infrastructure and bulletproof hosting services like NICENIC to evade takedowns. In this latest campaign, infrastructure used includes a wide array of phishing domains spoofing well-known crypto platforms such as Coinbase, Binance, Gemini, and Uphold, as well as services like Gmail and Google.
Several of the malicious domains suggest the attackers are also attempting to harvest passkey credentials. Domains such as mypasskey[.]info, passkeysetup[.]com, and related subdomains reflect the increased attention cybercriminals are giving to passkeys, which have been adopted more widely in recent months as phishing-resistant authentication methods.
LastPass users are advised not to click links in suspicious emails claiming to be from the firm, and never share their master passwords with anyone. Phishing attempts should be reported to ‘abuse@lastpass.com.’
Users should also verify that they are only entering credentials on the official LastPass domain (lastpass.com) and consider enabling multifactor authentication (MFA) if not already in use.







Leave a Reply