
The REvil cybergang has officially taken credit for the Kaseya ransomware attack and is demanding a $70 million payout. While this would appear to be the largest payout ever, we see payout demands continuing to increase, along with the frequency of attacks. We examine how many different industries remain vulnerable to further exploits and the potential impacts to society at large.
While many Americans were relaxing over the 4th of July holiday weekend, cybercriminals were hard at work exploiting vulnerabilities in Kaseya software, which is used by thousands of businesses around the world. The Russian-speaking REvil group is demanding $70 million in Bitcoin payment in exchange for the decryption key, while US federal authorities continue to investigate the situation.
In examining the event, it appears the hackers carried out a supply chain attack by exploiting a vulnerability they discovered in Kaseya VSA software. This Kasaya VSA attack was targeted at managed service providers (MSPs) and their downstream customers.
Scope of the Kaseya ransomware attack: Who is affected?
Kaseyea issued a statement today (July 6, 2021) confirming the scope of the attack to be around 60 direct Kaseya customers, in addition to about 1,500 downstream businesses:
To date, we are aware of fewer than 60 Kaseya customers, all of whom were using the VSA on-premises product, who were directly compromised by this attack. While many of these customers provide IT services to multiple other companies, we understand the total impact thus far has been to fewer than 1,500 downstream businesses.
– Kaseya official statement on July 6, 2021
Already we are seeing numerous businesses around the world affected by the Kaseya attack. This includes COOP, a large supermarket chain in Sweden, which had to close 800 stores due to cash registers being locked from the attack.
Kaseya is posting regular updates on their support website here.
Largest ransomware payout demand ever
The REvil group is currently using a darkweb (.onion) website to advertise their exploits. They are also using the site to demand a $70 million payout for the decryption key. This appears to be the largest ransomware payout demand ever.
Here is a screenshot we obtained from REvil\'s darkweb (.onion) website, which they sardonically refer to as the “Happy Blog”.
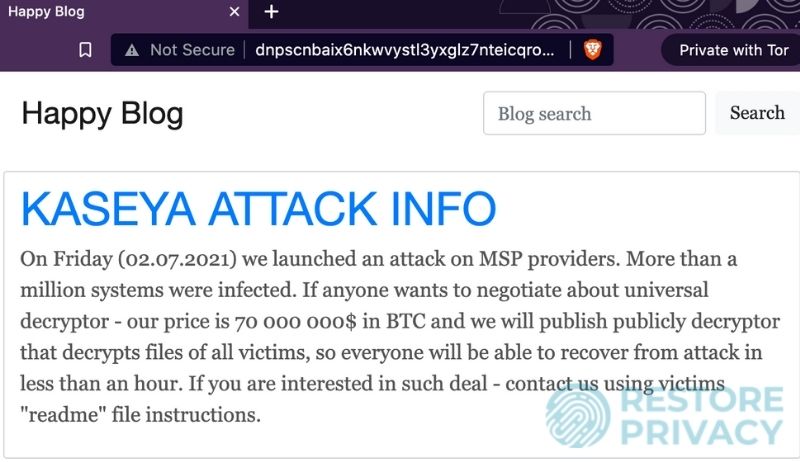
Note: We do NOT recommend directly visiting this darkweb website without taking proper precautions. This includes using a secure browser that routes traffic through the Tor network, on top of a good VPN to hide your IP address. Additionally, you should consider viewing the website in an isolated virtual machine, to prevent any potential malware or viruses from infecting your main operating system.
REvil cybergang targets many victims
Aside from their ransomware payout demands, REvil is also using their \”Happy Blog\” to showcase their other victims. Here are a few examples we found:
- University Medical Center of Southern Nevada
- Neroindustry.com
- Vic Pharma Industry and Trade Ltd.
- The Smith & Wollensky Restaurant Group, Inc.
- Whittlesey & Hadley
- Citroen Wells
- Agile Property Holdings
With every entry, the hackers posted a data sample as proof of their hack. This reveals sensitive data about their victims to anyone who visits the darkweb site. For example, under the entry for Law Offices of Michael B. Brehne, P.A. (a law firm in Altamonte Springs, Florida), we find private attorney passwords, internal corporate files, copies of letters and correspondence, and other internal documents uploaded to the site for anyone to view. Below is a redacted sample:
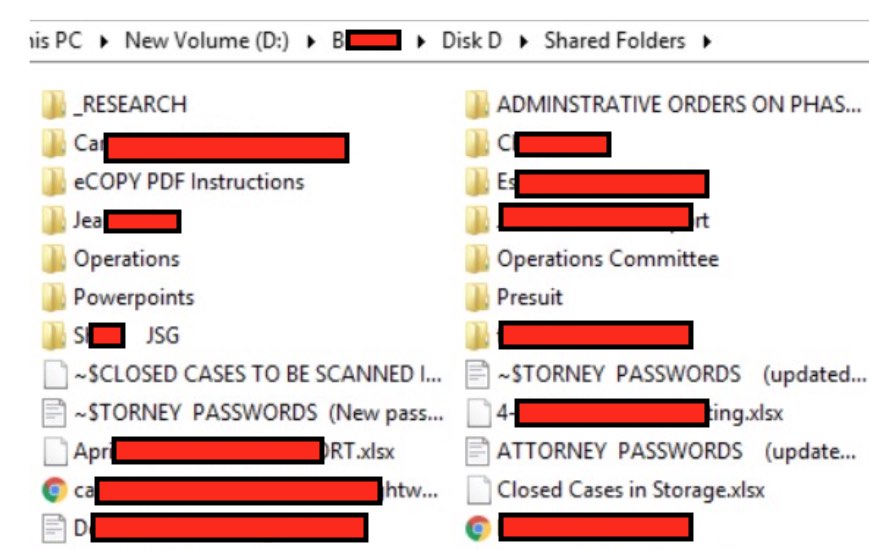
Tip: Don't save a giant list of passwords in cleartext on your computer. Instead, use a good password manager that keeps your passwords encrypted and secure.
And as we have noted before on RestorePrivacy, this data can be used by others to further exploit those who are affected by this latest ransomware attack.
At the time of this writing, we counted 239 different organizations and individuals being highlighted on REvil's website.
Ransomware payout demands are increasing
At $70 million, this is the largest ransomware payout demand ever. For comparison, below are the record-holding ransomware payout demands (along with payment status):
- Kaseya: $70,000,000 (Not Yet Paid)
- CNA Financial: $40,000,000 (Paid)
- JBS: $11,000,000 (Paid)
- Garmin: $10,000,000 (Not Confirmed)
- CWT Global: $4,5000,000 (Paid)
- Brenntag: $4,400,000 (Paid)
- Colonial Pipeline: $4,400,000 (Paid)
- Travelex: $2,300,000 (Paid)
- University of California: $1,140,000 (Paid)
- Riveira Beach City: $600,000 (Paid)
- Communication and Power Industries: $500,000 (Paid)
- Lake City: $500,000 (Paid)
- University of Utah: $457,000 (Paid)
- Jackson County: $400,000 (Paid)
- City of Florence: $300,000 (Paid)
- Tillamook County: $300,000 (Paid)
- Yazoo County School District: $300,000 (Paid)
- La Porte County: $130,000 (Paid)
- Baltimore City: $100,000 (Not Paid)
- Stratford City: $75,000 (Paid)
In previous years, such as in 2019, we saw ransomware payout demands in the five to six figure range. Starting in 2020, and going on to today, we see ransomware payout demands for millions of dollars, up to eight figures.
Looking at the data, we can see an unmistakable trend: ransomware payout demands are increasing.
The JBS food supplier paid $11 million to hackers just last month in June, 2021. A few months before that, the Colonial Pipeline ransomware saga was in the news, with a payout for $4.4 million. However, US federal authorities were able to seize back Colonial Pipeline ransomware funds, allegedly through a server seizure.
The previous ransomware payout record was CNA Financial, which paid $40 million in ransom to hackers this past spring.
Frequency of ransomware attacks is increasing; many industries remain vulnerable
Looking at the data, it is also clear that the frequency of ransomware attacks is trending upward. Aside from increasing frequency, we see this problem affecting many areas of the world economy.
Our analysis shows a wide swath of industries being targeted by ransomware gangs from around the world. Below are a sample of industries that have been affected by ransomware, as well as examples from each industry:
- Software providers (Kaseya VSA)
- Food suppliers (JBS)
- Financial service providers (CNA Financial)
- Critical infrastructure, including oil and gas suppliers (Colonial Pipeline)
- Healthcare providers (Scripps Health; Ireland national health service)
- Schools (University of Utah; University of California)
- Municipalities, including city, state, and federal governments (Baltimore; Stratford City; Jackson County)
The bad guys are making money (and you will foot the bill)
And for those wondering why ransomware attacks are increasingly in the news, the answer is simple.
Ransomware pays and the bad guys are making big money.
Unfortunately, this is leading to a self-perpetuating cycle. As various organizations around the world pay off ransomware hackers for decryption keys, the hackers are also becoming more emboldened. We see this directly leading to larger payout demands and an increase in the frequency of attacks.
Unfortunately, you are likely picking up the tab for these attacks, as businesses, governments, and other organizations are forced to pass on costs to their users. This means that costs for goods, services, and even your taxes may go up, while ransomware hackers rake in the money.
This also leads us to an interesting question:
Should ransomware hackers be paid?
One could argue that by paying off ransomware hackers, you are actually making the problem worse by incentivizing people to profit from hacking.
However, by not paying off the hackers, threat actors will likely release all data on their victims. This could lead to millions of people being exposed and becoming ripe targets for:
- Identity theft
- Extortion
- Phishing attacks
- Financial exploitation and fraud
So we see this problem as a catch-22, and wherever you fall on the payout debate, there is one thing we can probably all agree on….
Buckle up, it's going to get worse
So far in 2021, we have seen numerous major industries affected by cybercriminals. But it\'s not just businesses. When databases are exposed, it can put millions of customers, citizens, and end-users at risk. We saw this in the recent LinkedIn data leak that exposed information on 700 million LinkedIn users.
And it also leads one to wonder just how bad this can get.
- Will food supply lines be shut down, such as with a ransomware attack on JBS?
- Will energy prices with another attack on oil and gas infrastructure hack, such as with Colonial Pipeline?
- Will the global supply chain grind to a halt with attacks on logistics and transportation companies?
Time will tell. We\'ll keep you posted on the latest developments.







Leave a Reply