
The Japanese National Police Agency (NPA) and the Cabinet Cybersecurity Center have issued a comprehensive advisory about an ongoing cyberespionage campaign targeting the nation since 2019. The attacks, attributed to the Chinese threat group MirrorFace (also known as Earth Kasha), focus on stealing sensitive data related to Japan's national security and advanced technologies. These operations are suspected to involve Chinese state-backed actors.
MirrorFace's multi-year cyberespionage operation
The advisory outlines three distinct attack waves:
Campaign A (2019–2023): This involved spear-phishing emails containing malware-laden attachments targeting think tanks, government entities (including retirees), politicians, and media professionals. The malware used in this phase was primarily LODEINFO, which exploited macros in Microsoft Office documents.
Campaign B (2023): Attackers exploited vulnerabilities in VPN devices and public-facing servers, focusing on sectors such as semiconductors, manufacturing, telecommunications, academia, and aerospace. Tools like Neo-reGeorg and Cobalt Strike were deployed to establish backdoors.
Campaign C (2024): Starting mid-2024, this campaign shifted to phishing emails embedding malicious links. These led to malware downloads, with the ANEL malware used to compromise academic institutions, think tanks, and political figures.
The MirrorFace group demonstrated innovative methods to avoid detection.
The first is Windows sandbox abuse. The attackers leveraged this isolated virtual environment to run malware like LODEINFO, evading antivirus and Endpoint Detection and Response (EDR) systems. The use of sandbox configurations allowed for hidden malware execution, leaving minimal traces once the sandbox was terminated.
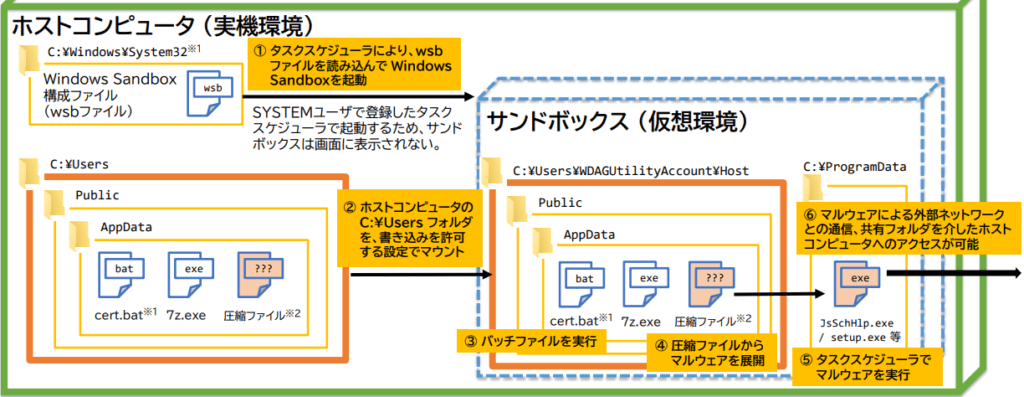
NPA
The second method is Visual Studio Code (VSCode) exploitation. This technique utilized the software's development tunnels for remote access. Attackers installed VSCode CLI tools on compromised devices, enabling remote command execution without the user's knowledge. Communication through devtunnels.ms and related domains facilitated their operations.
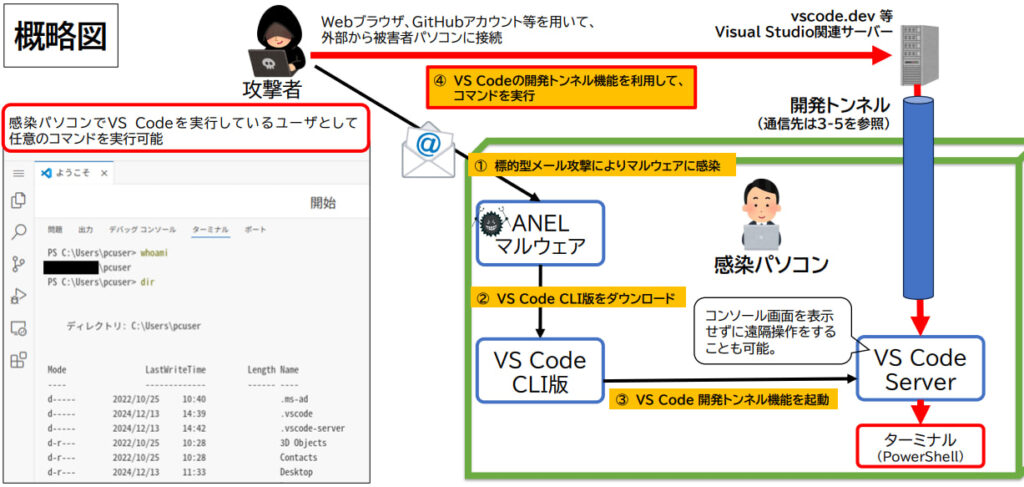
NPA
The targeted sectors reflect the campaign’s strategic objectives. Think tanks and academia suggest an interest in policy and innovation, while aerospace and semiconductors show industrial espionage aims. Media figures and political entities were also targeted, indicating the threat group's intent to influence or pre-empt political maneuvers.
MirrorFace used social engineering tactics, posing as trusted figures or organizations. For example, email subjects referenced topical issues like the “Taiwan Strait” or “Indo-Pacific strategies,” increasing the likelihood of user engagement.







Leave a Reply