
Interlock, a cybercrime group known for its double extortion tactics, has claimed responsibility for the ransomware attack on DaVita Inc. earlier this month.
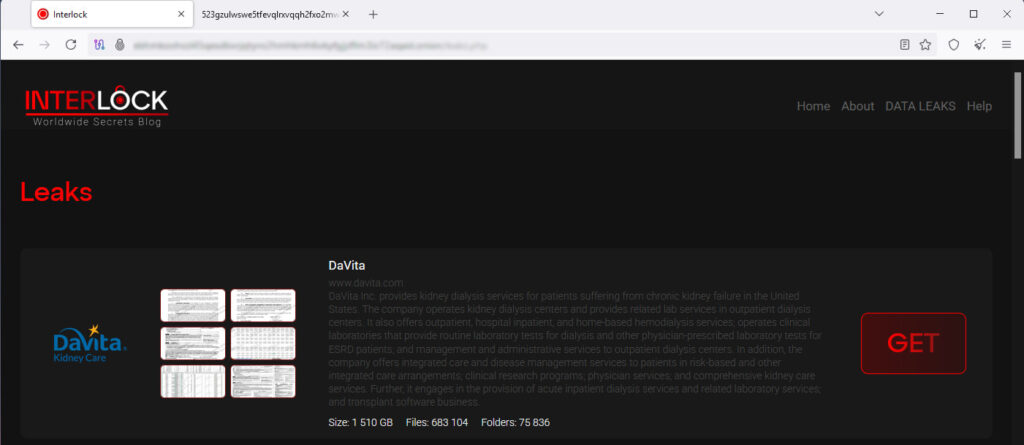
The group has now listed DaVita on its leak site, uploading what it claims is 1.5 terabytes of stolen data, including over 683,000 files and 75,000 folders. The data dump includes internal documents, spreadsheets, and screenshots of sensitive records, suggesting the exfiltration of potentially critical operational and patient-related information.
CyberInsider has reached out to DaVita to confirm the legitimacy of Interlock’s claims, but the company has not yet responded.
The ransomware attack was first disclosed on April 14, 2025, when DaVita submitted a Form 8-K filing to the U.S. Securities and Exchange Commission. At the time, the healthcare giant stated that ransomware had encrypted segments of its network, leading to operational disruption. Although patient care was reportedly unaffected, the incident forced DaVita to activate its incident response protocols and engage third-party cybersecurity specialists to assess the damage and contain the threat.
DaVita Inc., headquartered in Denver, Colorado, is one of the largest providers of kidney dialysis services in the United States. The company operates hundreds of outpatient dialysis centers and offers a broad range of renal care, hospital inpatient services, and laboratory diagnostics for patients with chronic kidney failure. Its digital infrastructure is integral to patient scheduling, treatment coordination, and clinical lab operations — making it a critical and attractive target for ransomware operators.
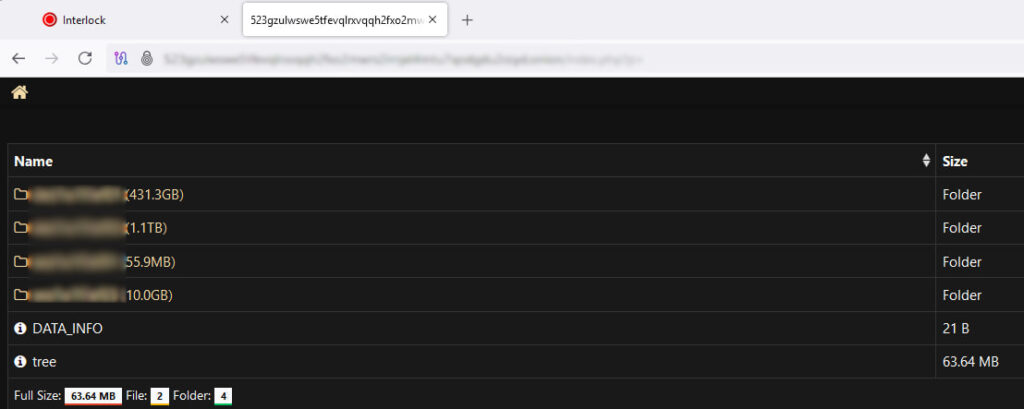
The leak announcement on Interlock’s darknet site includes a detailed profile of DaVita’s services and infrastructure, accompanied by several preview images of what appear to be internal documents. The leak page reveals the structure of some of the leaked directories, with folders reportedly containing hundreds of gigabytes of data. The folder sizes range from 55 MB to over 1 TB, suggesting a vast and varied data exfiltration campaign, likely staged before the ransomware payload was deployed.
The Interlock group operates under a familiar double extortion model: encrypting victims’ systems while also exfiltrating sensitive data and threatening to leak it unless a ransom is paid. The group’s leak site, branded “Interlock: Worldwide Secrets Blog,” hosts disclosures from past victims, many large enterprises in the healthcare and critical infrastructure sectors.
At this stage, DaVita has not confirmed whether any patient data was stolen, nor has it addressed the authenticity of the Interlock leak. The lack of a public response to Interlock’s claim, combined with the absence of forensic confirmation, means that the full impact on DaVita’s data security and patient confidentiality remains uncertain. Potentially impacted individuals should be on high alert for phishing and social engineering attempts.
Update: DaVita sent CyberInsider the below statement:
We are aware of the post on the dark web and are in the process of conducting a thorough review of the data involved. A full investigation regarding this incident is still underway. We are working as quickly as possible and will notify any affected parties and individuals, as appropriate. We are disappointed in these actions against the healthcare community and will continue to share helpful information with our vendors and partners to raise awareness on how to defend against these attacks in the future. – A DaVita spokesperson







Leave a Reply