
A security researcher has shared more details about a method he followed to find the IP address of a Tor hidden service hosting the data that a Ragnar Locker ransomware affiliate had stolen from Capcom in 2020.
The details were shared with the FBI at the time, helping the investigations in their work, and eventually leading to the indictment of the attacker in May 2023.
Background
Ragnar Locker claimed an attack on video game publisher Capcom in November 2020. Following a collapse in the ransom payment negotiations, the attackers leaked 67GB of stolen data on a dark web page.
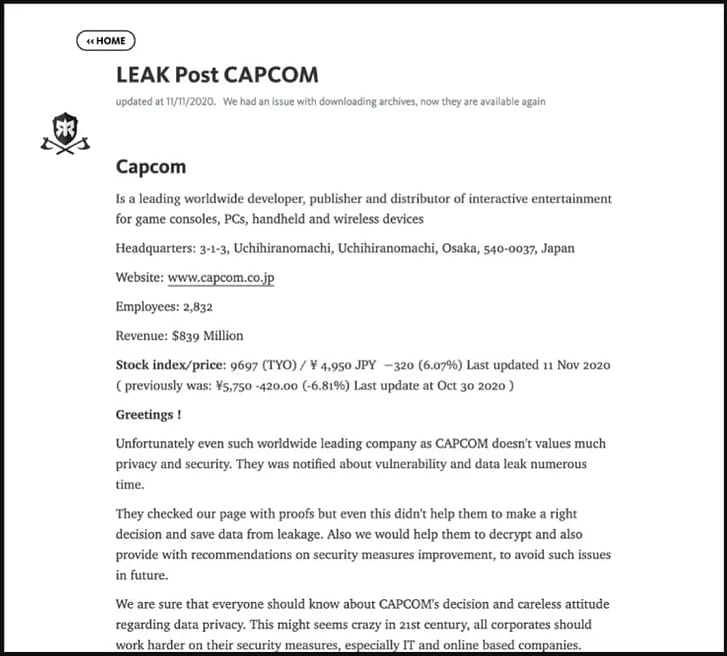
The files were hosted on an onion site, which is part of the Tor network, and hence the host’s IP address was obscured. The analyst tried to find anything useful, like the website’s source code, SSL certificate, etc., but nothing was retrievable.
Next, he checked the response headers, and the only accessible piece of information that might have had some value was the ETag data. Entity Tags (Etags) are part of the HTTP protocol used for web caching, providing a resource validation mechanism that reduces data exchange, bandwidth, and network overhead, by minimizing unnecessary data transfer.
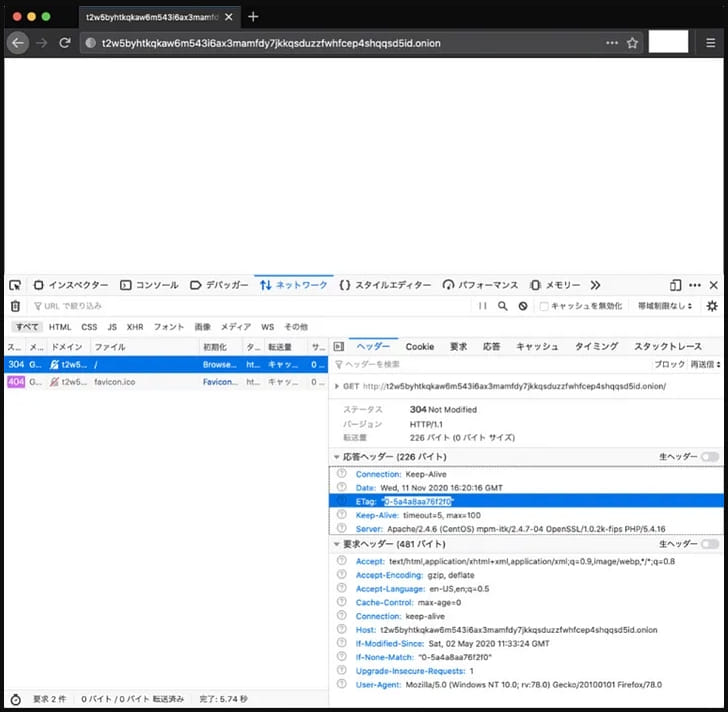
Simply put, ETags are identifiers characterizing the state of a resource, i.e., a website’s content, so the visitor’s browser uses it as a comparison token with the server’s ETag to determine if the cached version is still valid or needs to be updated.
From ETag to IP Address
In the case of the website hosting the Capcom data, the Etag (0–5a4a8aa76f2f0) acts as a unique identifier that could be inputted into the specialized internet search platform ‘Shodan’ to potentially find any matches.
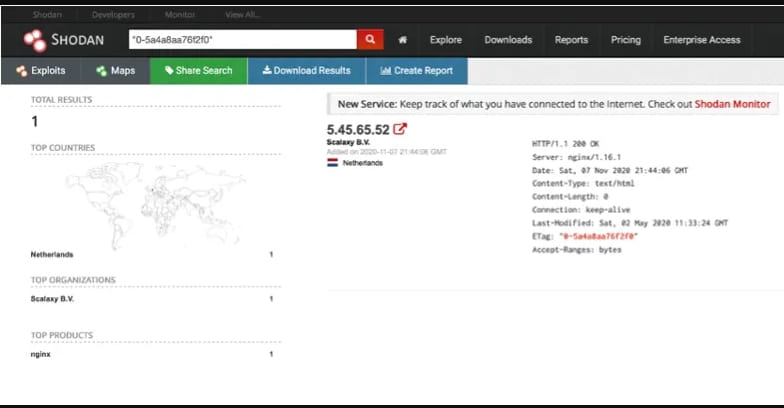
The investigator discovered 5[.]45[.]65[.]52, an IP address pointing to a Netherlands-based data center services provider that was serving the same content and the data leak link and had the same ETag in its response when trying to access it.
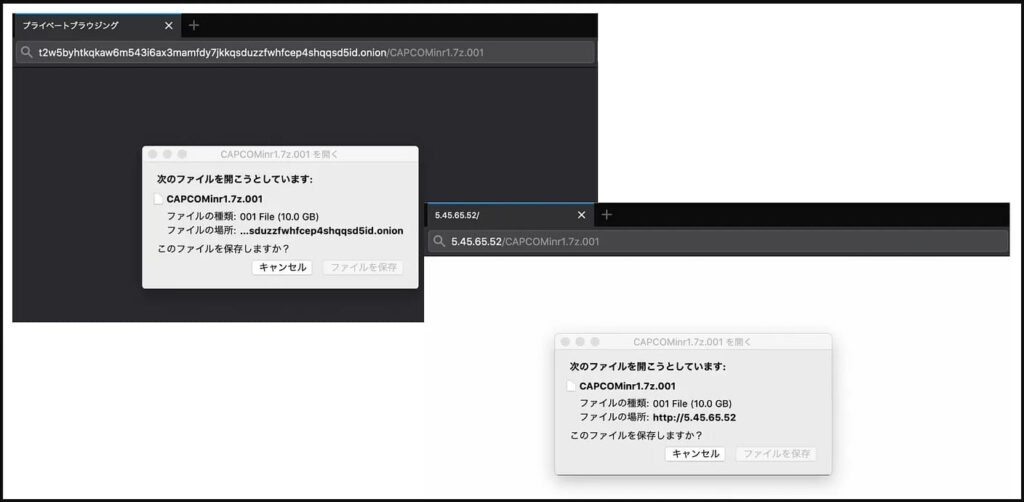
While the service provider wasn’t responsible for disseminating the stolen data, this finding could help FBI agents locate the firm’s customer, so it might have acted as a pivot point in their investigations. Indeed we see the particular IP address mentioned in the associated Flash Alert; however, no further details about it were shared by the law enforcement agency.
Using ETags to uncover more information about hidden hosting locations is a possibility that security researcher Adam Maxwell first highlighted back in 2018 on a Medium post, explaining that even though ETags may not lead to straight server identification, they are always helpful in narrowing down results.







Thank you Heinrich. A very interesting post. I can see the Etag header did not prevent tracking. A great learning!