
Cybereason's latest report uncovers Cuckoo Spear, a stealthy cyber-espionage campaign attributed to the Chinese state-sponsored group APT10. The campaign, which targets critical sectors in Japan, India, and Taiwan, has managed to stay undetected on victims' networks for years, using a sophisticated mix of persistence mechanisms and defense evasion techniques.
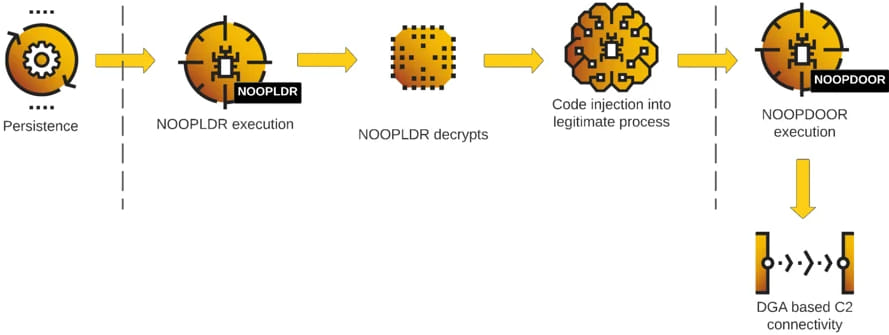
At the heart of Cuckoo Spear's stealth are two malware components, NOOPLDR and NOOPDOOR, which serve as a loader and backdoor, respectively. Together, they form a persistent foothold in victim networks, often remaining active for over two years. The campaign's longevity is primarily due to its advanced persistence mechanisms, such as leveraging legitimate system processes and tools, ensuring that APT10’s presence blends in with normal network activity.
Cuckoo Spear’s stealth tactics
APT10 uses scheduled tasks to ensure the NOOPLDR malware loader is continually re-executed. The malware is loaded through a malicious MSBuild script, which compiles and executes it in real time. MSBuild is a legitimate tool used for building applications on Windows systems, so its use is less likely to trigger suspicion from security tools. The scheduled tasks automatically restart NOOPLDR upon system reboot, maintaining persistence across multiple incidents observed by Cybereason.
The threat actors also use Windows Management Instrumentation (WMI) event consumers, a common tactic in advanced attacks, to achieve persistence. WMI event consumers allow for the execution of custom scripts, triggered by specific system events. In the Cuckoo Spear campaign, these scripts load NOOPDOOR through MSBuild when certain events occur. Because WMI is deeply integrated into Windows and commonly used for legitimate system management, its misuse is difficult to detect without specialized monitoring.
APT10 also establishes persistence by creating malicious Windows services that load unsigned DLL files (specifically the NOOPLDR-DLL variant). By placing the malware in trusted directories, such as C:\Windows\System32, and modifying the registry to ensure it is loaded by svchost.exe (a legitimate system process), the attackers can hide the malware’s presence.
NOOPDOOR’s command-and-control (C2) communication uses a Domain Generation Algorithm (DGA), which creates new domains based on predefined patterns, making it harder to track. If the external C2 servers are blocked or unreachable, NOOPDOOR enables internal pivoting (lateral movement) within the compromised network. This allows infected machines to communicate with each other locally, ensuring that the attacker maintains control even if external network access is restricted.
Cybereason
Finally, the attackers delete system logs after performing malicious activities to remove traces of their presence. Additionally, they use legitimate system commands, such as ping, nslookup, and net, to conduct reconnaissance within the compromised network, avoiding triggering alarms.
Impact and recommendations
The Cuckoo Spear campaign has primarily targeted Japanese organizations in the manufacturing, industrial, and political sectors. APT10’s focus on critical infrastructure suggests a motive rooted in long-term intelligence gathering, with the goal of exfiltrating valuable data.
To defend against such stealthy threats, Cybereason recommends the following:
- Monitor for abnormal scheduled tasks and MSBuild activity.
- Look for unusual WMI event triggers, especially those that execute scripting engines or system-level commands.
- Employ strict controls around the loading of unsigned DLL files and ensure proper monitoring of critical system directories like System32.
- Monitor for unusual traffic on internal ports commonly used by NOOPDOOR, such as 5984, to detect potential lateral movement and internal pivoting.
- Utilize IOCs, YARA rules, and open-source scripts provided by Cybereason on GitHub to proactively detect NOOPDOOR and related malware.







Leave a Reply