
Security researchers at Tarlogic Security have discovered an undocumented feature in the widely used ESP32 Bluetooth microcontroller, which is reportedly used in over a billion IoT devices.
This hidden functionality could enable attackers to bypass security controls, execute arbitrary modifications, and impersonate trusted devices — posing a major risk to smart devices, including phones, computers, smart locks, and medical equipment.
Bluetooth commands as attack vector
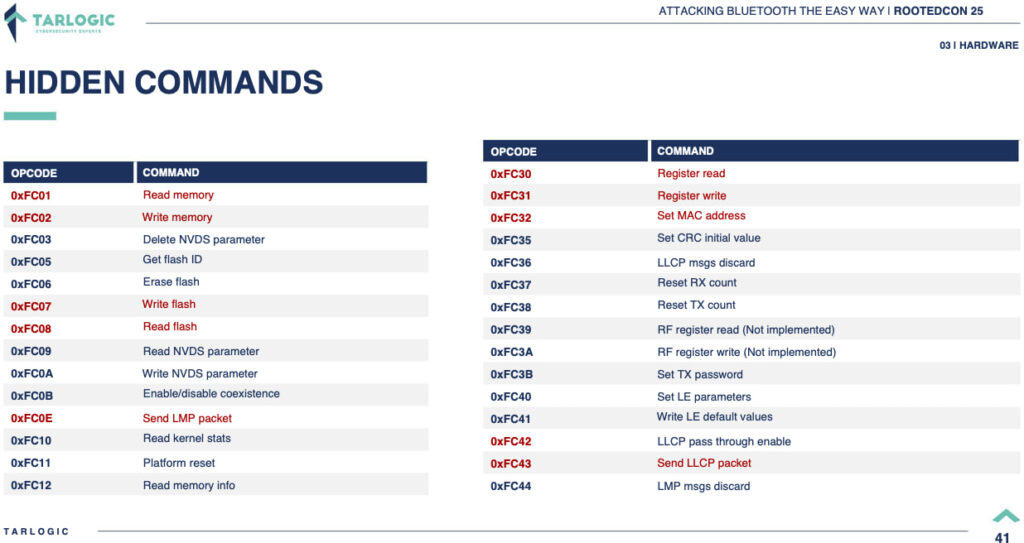
The findings were presented at RootedCON 2025, a leading Spanish-language cybersecurity conference, by Tarlogic's Miguel Tarascó and Antonio Vázquez. Their research, focused on Bluetooth security, revealed that the ESP32 chip — a low-cost microcontroller with WiFi and Bluetooth capabilities — contains undocumented HCI (Host Controller Interface) commands. These commands allow direct memory access and modification, which could be leveraged to introduce persistent malware or conduct identity theft attacks.
ESP32, developed by Espressif Systems, is one of the most commonly used microcontrollers for consumer and industrial IoT devices. With over one billion units sold worldwide, it is widely integrated into smart home products, industrial sensors, medical devices, and consumer electronics. The affordability of the chip, often available for €2 on major e-commerce platforms, has made it a default choice for IoT manufacturers — amplifying the potential impact of this security issue.
According to Tarlogic, the undocumented commands in ESP32 could allow attackers to:
- Modify device memory to introduce malicious code.
- Bypass code audit controls, making detection and remediation more difficult.
- Impersonate trusted Bluetooth devices, tricking victims into connecting with compromised hardware.
- Extract sensitive data from connected mobile phones, laptops, and other devices, even when offline.
This feature, while not explicitly designed as a backdoor, raises serious security concerns, particularly in supply chain attacks, where threat actors could manipulate chipsets before they even reach consumers.
In the context of this study, Tarlogic also unveiled BluetoothUSB, a new free and open-source tool designed for Bluetooth security audits. Existing tools for Bluetooth testing suffer from compatibility issues, lack of maintenance, and expensive hardware requirements, making comprehensive audits difficult. Tarlogic's tool solves most of these problems by being platform-agnostic and free from requiring specialized hardware.
Backdoor claims questioned
Following the initial report, cybersecurity firm Dark Mentor's researcher Xeno Kovah challenged the characterization of the ESP32 functionality as a “backdoor.” Kovah noted that the vendor-specific HCI commands found in the ESP32 are a common industry practice rather than a covert or maliciously designed access point. Similar functionalities exist in Bluetooth chips from Broadcom, Cypress, and Texas Instruments, where vendor-specific commands serve as a private API for debugging and firmware management.
Kovah emphasized that undocumented commands do not inherently constitute a security vulnerability unless they violate a specific security model. They further criticized the fear-mongering language in initial reports, stating that while the security risks of memory read/write capabilities should not be dismissed, calling them a backdoor was misleading. Tarlogic has since updated its report to reflect this distinction, replacing “backdoor” with “hidden feature.”
Espressif responds to the security concerns
Earlier today, Espressif Systems released an official statement clarifying that the undocumented HCI commands in ESP32 chips were intended as internal debug commands for testing purposes. Espressif emphasized that these commands:
- Are not remotely accessible via Bluetooth, radio signals, or the Internet.
- Exist as part of vendor-specific HCI implementations, a common industry practice.
- Do not pose an inherent security risk to ESP32 devices.
- Are only present in the ESP32 series, with ESP32-C, ESP32-S, and ESP32-H chips unaffected.
While Espressif maintains that these debug commands do not constitute a security vulnerability, the company has committed to releasing a software update that removes them entirely.
Following the publication of the initial report and the voiced concerns around the use of the term “backdoor,” Tarlogic updated its report, clarifying that the ESP32 issue should be described as a “hidden feature” instead. However, the risks remain significant, particularly in supply chain security, where manufacturers and cybersecurity teams must ensure robust protections against potential exploitation.
Tarlogic plans to release further technical details in the coming weeks, shedding more light on how these hidden ESP32 commands function and their potential misuse in cyberattacks.







Leave a Reply