
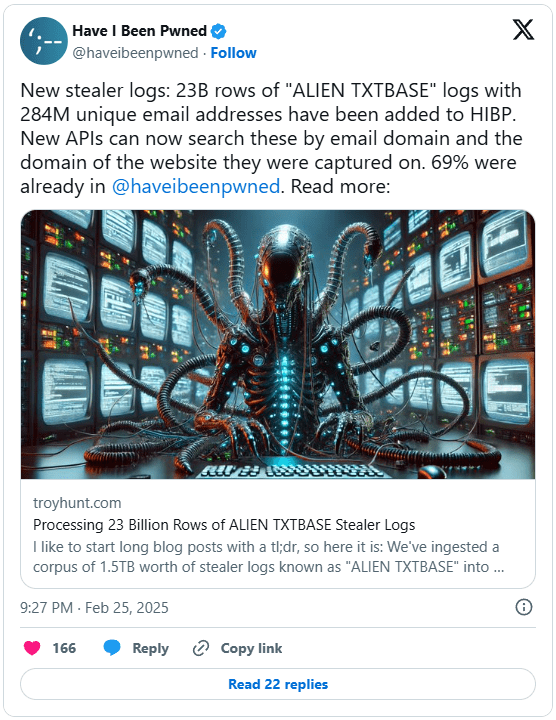
Have I Been Pwned (HIBP) has integrated a massive dataset of 23 billion rows from the ALIEN TXTBASE stealer logs, exposing 284 million unique email addresses linked to credentials stolen through malware.
The logs, originally distributed via Telegram, have also contributed 244 million previously unseen passwords to HIBP’s Pwned Passwords repository, with additional APIs introduced to help domain and website owners identify affected users.
The data surfaced in February 2025 after a government agency tipped off HIBP’s founder, Troy Hunt, to two files totaling 5GB, containing email addresses and passwords linked to various websites. Further investigation led to a larger 1.5TB dataset of stealer logs from 744 files uploaded to a Telegram channel. Telegram, which has increasingly been used as a platform for cybercriminal data distribution, facilitated the widespread availability of these credentials.
Verification of the dataset was conducted through multiple methods. One approach involved testing email addresses captured from login pages against legitimate services like Netflix, which confirmed account existence when password reset requests succeeded. Additionally, direct communication with affected users helped validate the authenticity of stolen credentials, reinforcing the dataset’s reliability.
What Is ALIEN TXTBASE?
ALIEN TXTBASE is a collection of stealer logs, data harvested from info-stealer malware that infects devices to capture login credentials as users enter them into websites. Victims often fall prey to malware through pirated software, malicious downloads, or phishing attacks. Once infected, their credentials are extracted and sold on criminal marketplaces or freely distributed on forums and Telegram channels, facilitating account takeovers, identity theft, and corporate breaches.
Each record ties an email address, website, and password together, giving attackers direct access to compromised accounts.
HIBP steps in
HIBP, a widely-used breach notification service, has processed and integrated the ALIEN TXTBASE dataset to enhance public awareness and cybersecurity defenses. 244 million new compromised passwords have been added to HIBP’s open-source password repository to allow users and organizations to perform password security checks. The data is fully searchable, so individuals can check if their email addresses appear in the logs via HIBP’s notification service.
To minimize the risk of credential theft, individuals and organizations should take proactive security measures:
- Use a password manager to generate and store unique passwords for every service.
- Enable multi-factor authentication (MFA) to add an extra layer of security to accounts.
- Avoid downloading pirated software or files from untrusted sources, as they often contain malware.
- Regularly check for breaches using HIBP and update compromised passwords immediately.
- Use endpoint security solutions to detect and block malware infections.







Is HIBP the worlds biggest honeypot/suckerbait?
Once you have entered details there, they are confirmed as existing 🙂
No, definitely not a honeypot. HIBP has done a lot for the community over the years.